Mixed intrusion detection method of wireless sensor network
A technology of wireless sensor and intrusion detection, which is applied in the direction of data exchange network, transmission system, digital transmission system, etc., and can solve problems such as wireless sensor network security attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
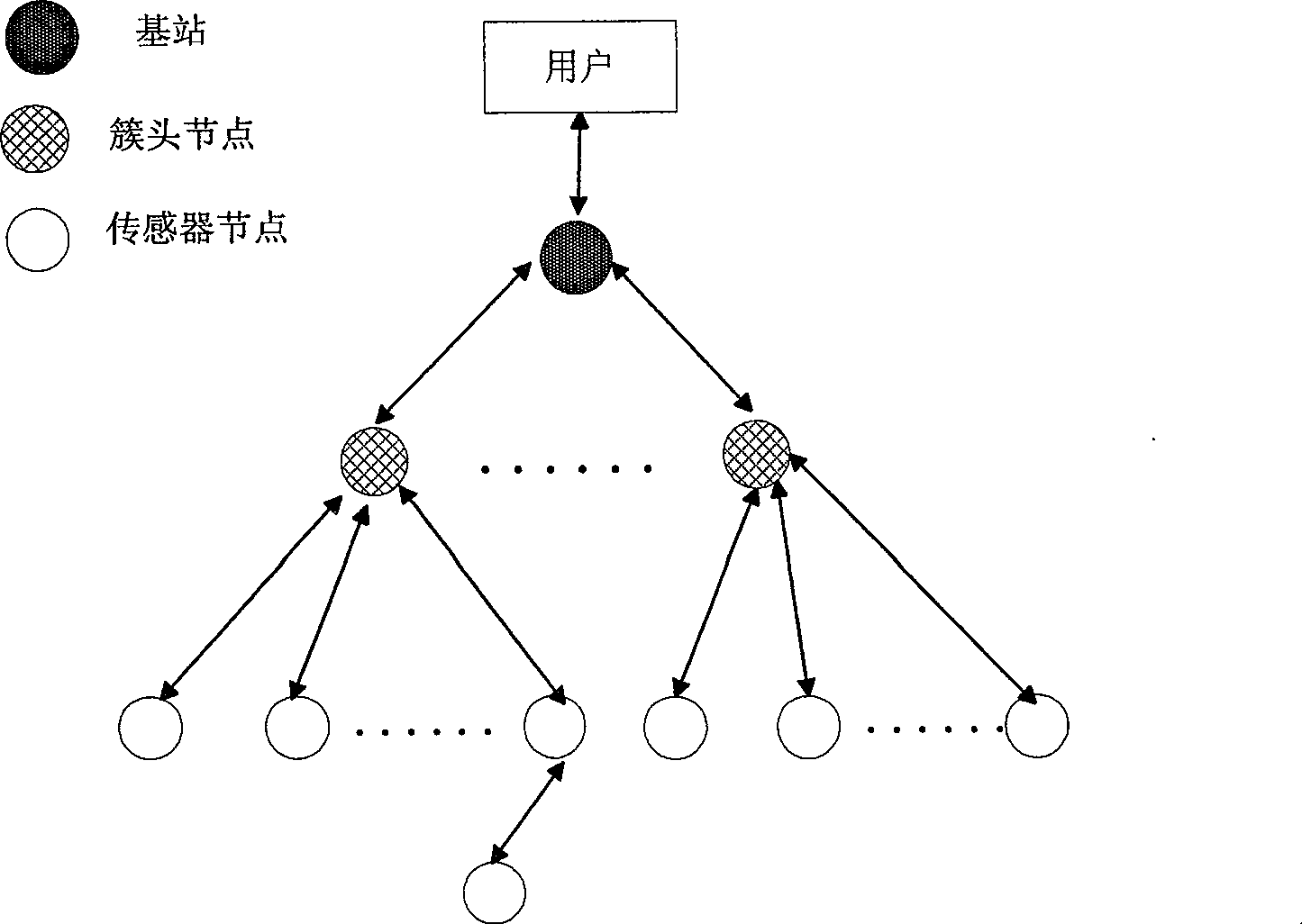
[0080] Assume that within a short period of time after the wireless sensor network is deployed, there are no malicious nodes in the network; each node saves its own neighbor table (reachable by one hop) and neighbor table through the neighbor discovery process; the base station keeps The topology of the entire network; the data contains the identity information of the source and target nodes.
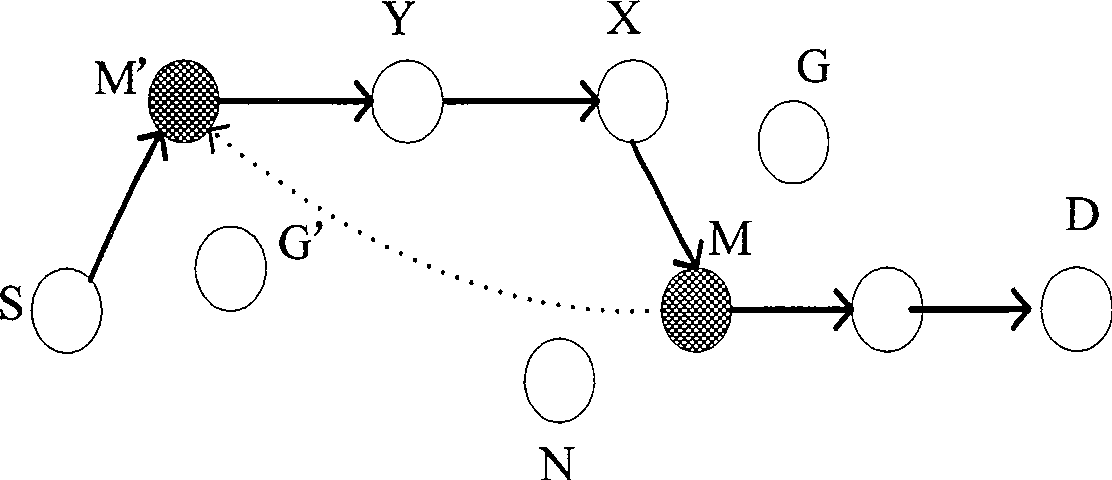
[0081] For the convenience of description, we divide the attacks that wireless sensor networks are vulnerable to into external attacks and internal attacks, and accordingly illustrate the specific implementation of the above hybrid intrusion detection method.
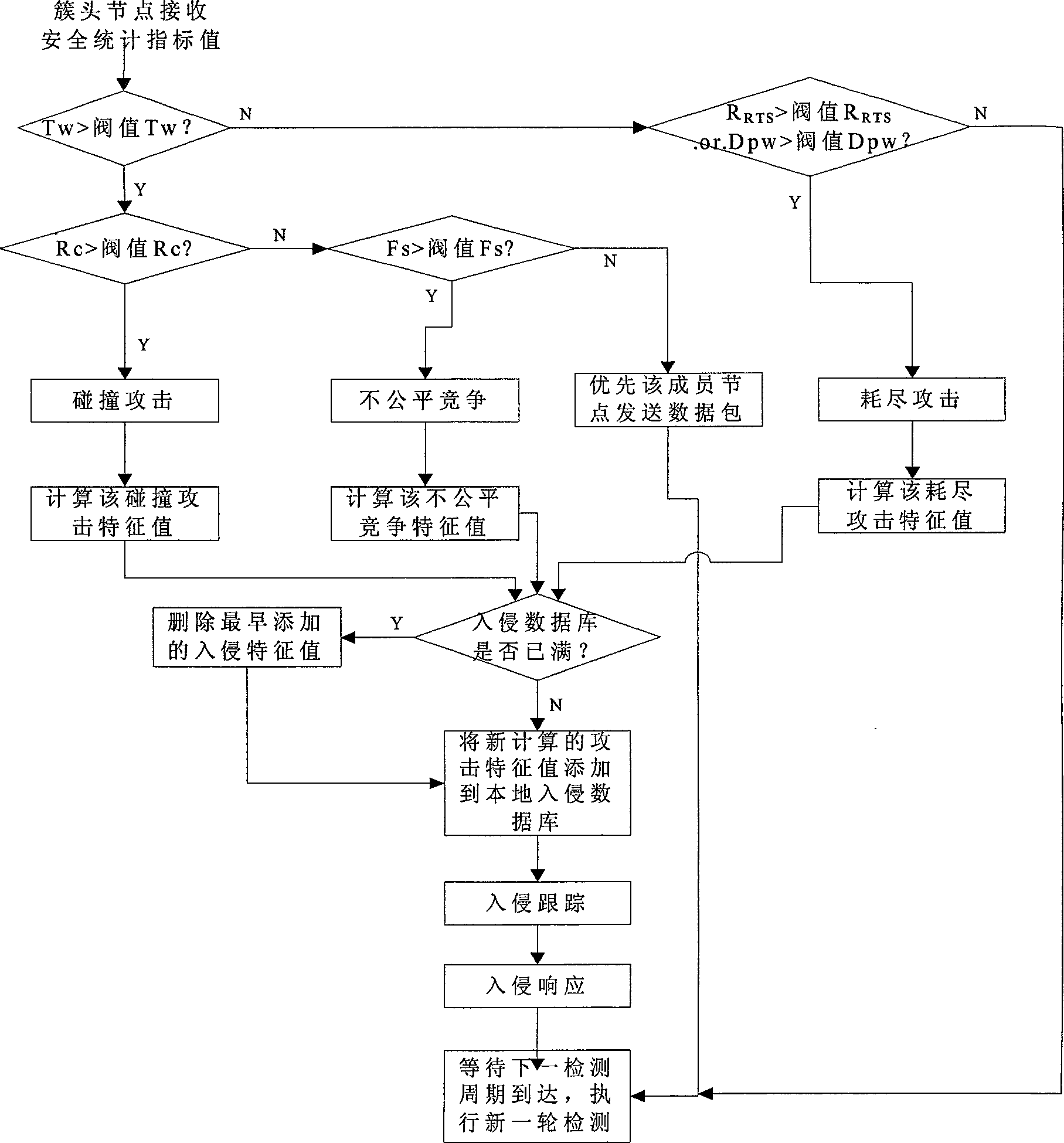
[0082] 1. Intrusion detection of external attacks
[0083] External attacks against wireless sensor networks mainly occur at the data link layer, including collision attacks, unfair competition, resource exhaustion attacks, and integrity attacks.
[0084] Collision attack: When the channel is not idle, malicious nodes intentiona...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com