A method for sub-network connection protection via serial monitoring function
A technology of subnet and function, applied in the field of optical communication, can solve the problems of normal service impact of H subnet, unsteady service, frequent service switching, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
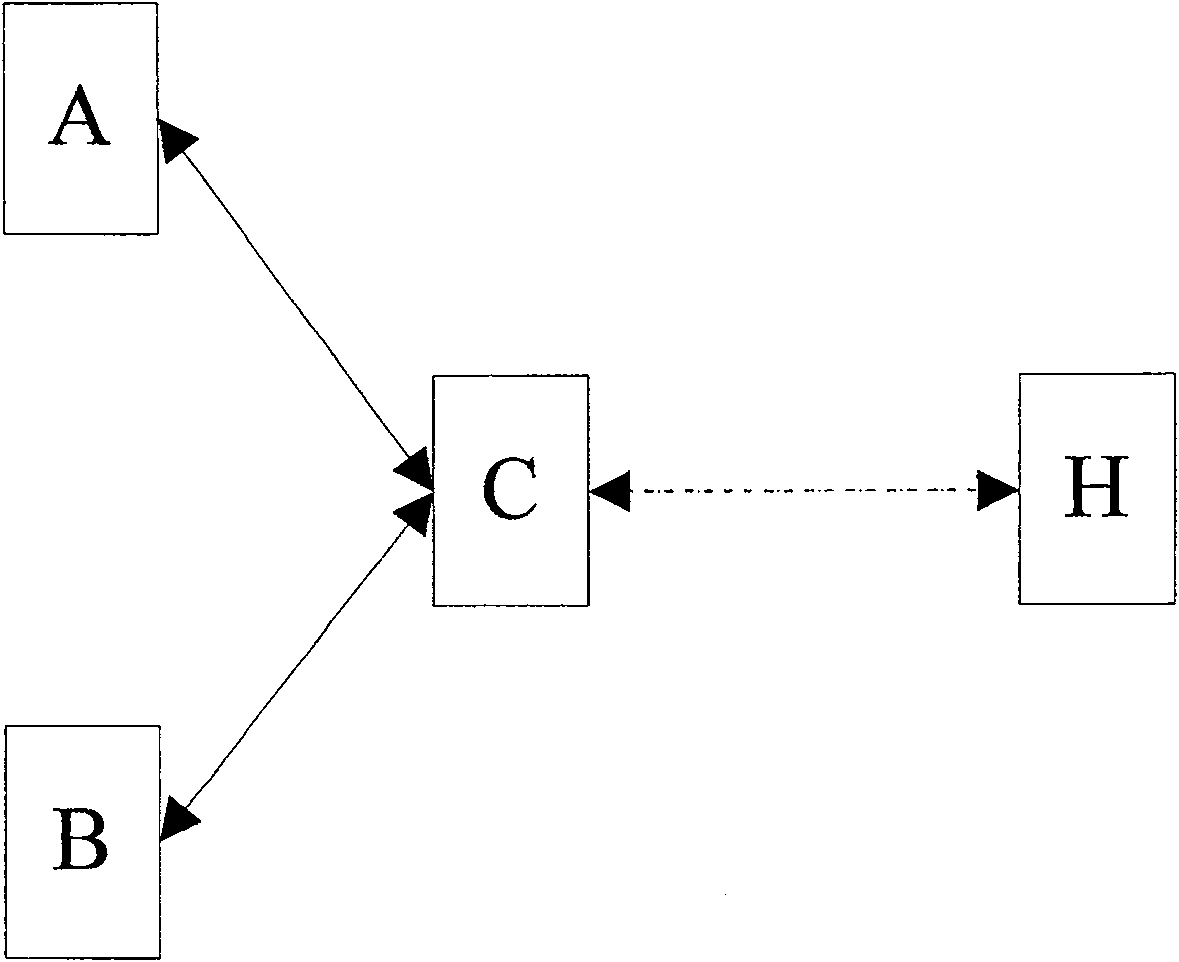
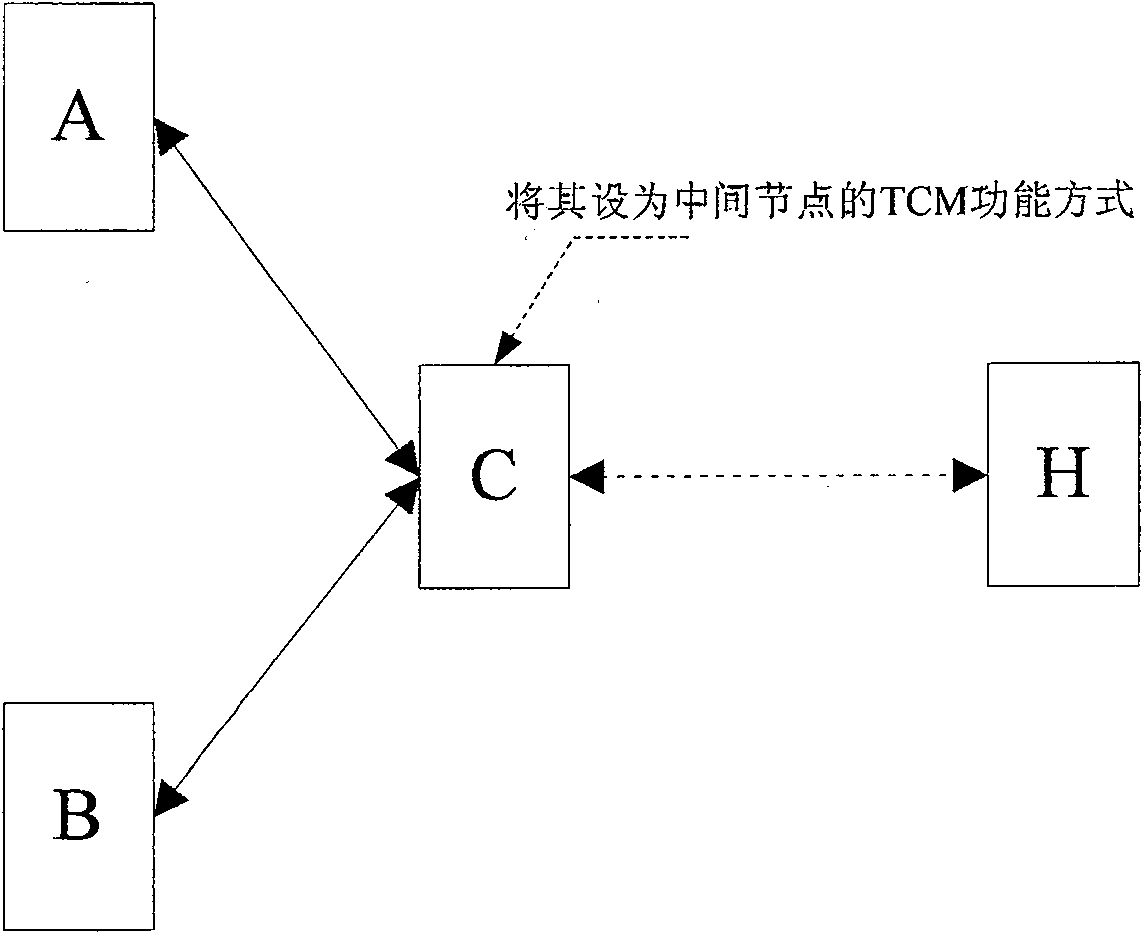
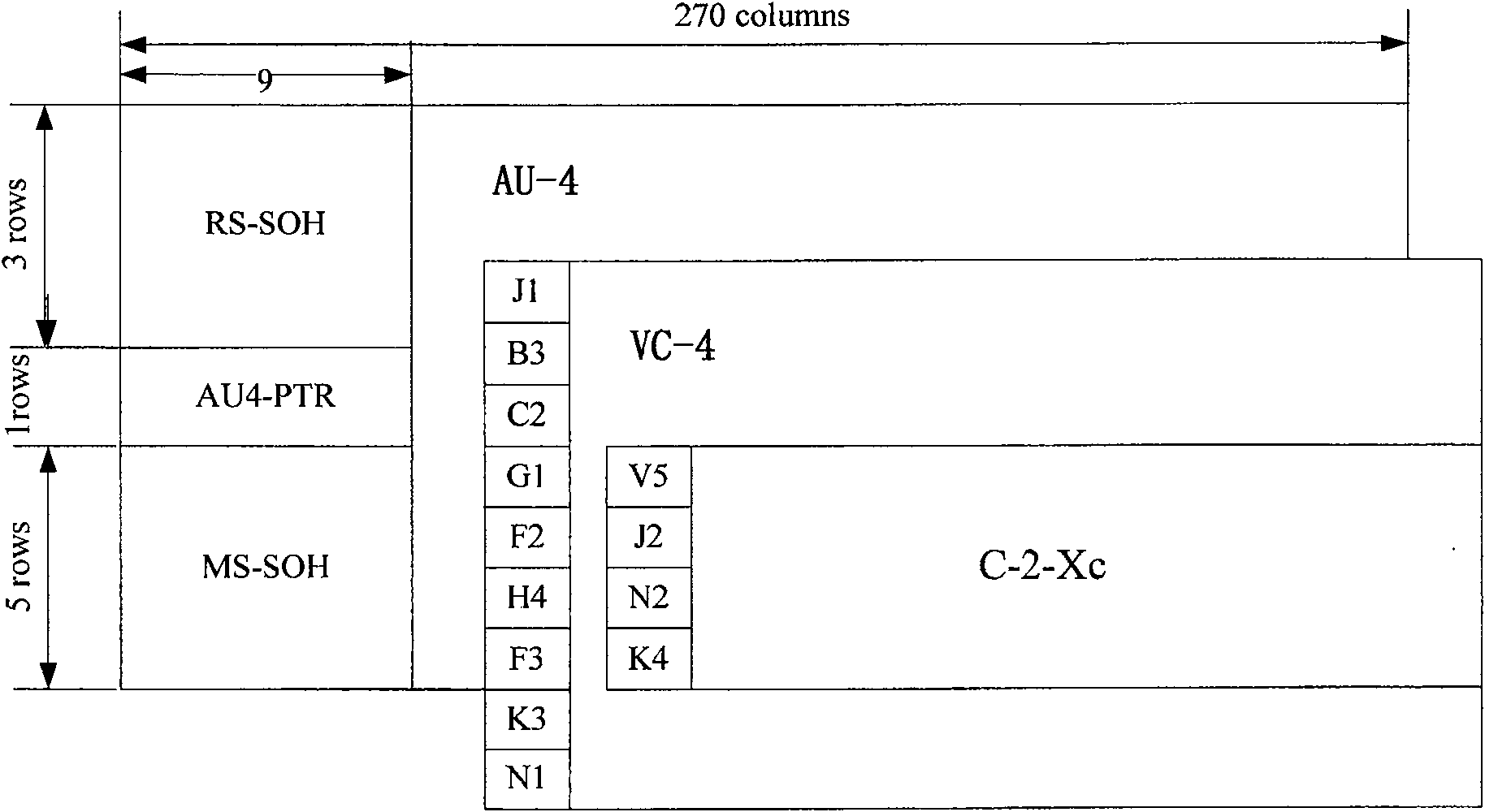
[0023] The method for realizing subnet connection protection by monitoring the TCM function in series provided by the present invention is suitable for the synchronous digital system SDH domain composed of two TCM source terminal networks and one TCM sink terminal network. The method introduces the TCM function of the intermediate node mode , Including the steps: (a) Set the subnet for configuring the subnet connection protection as the intermediate node TCM function mode; (b) Detect the signals transmitted by the two TCM source terminal networks respectively, when the TCM on the current working channel is detected In the signal transmitted by the source terminal network, the N1 or N2 byte contains the incoming alarm indication signal Incoming AIS information, and the protection channel signal is valid, the switching action is executed to switch the service from the working channel to the protection channel; (c) for N1 or N2 The content of the byte is processed through and transpa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com