A cross-domain access control system for realizing role and group mapping based on cross-domain authorization
A control system and access control technology, applied in the field of cross-domain access control systems, can solve problems such as complex role mapping work, inability to use cross-domain access control, and unsuitability for cross-domain access control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] The present invention will be described in further detail below in conjunction with the accompanying drawings.
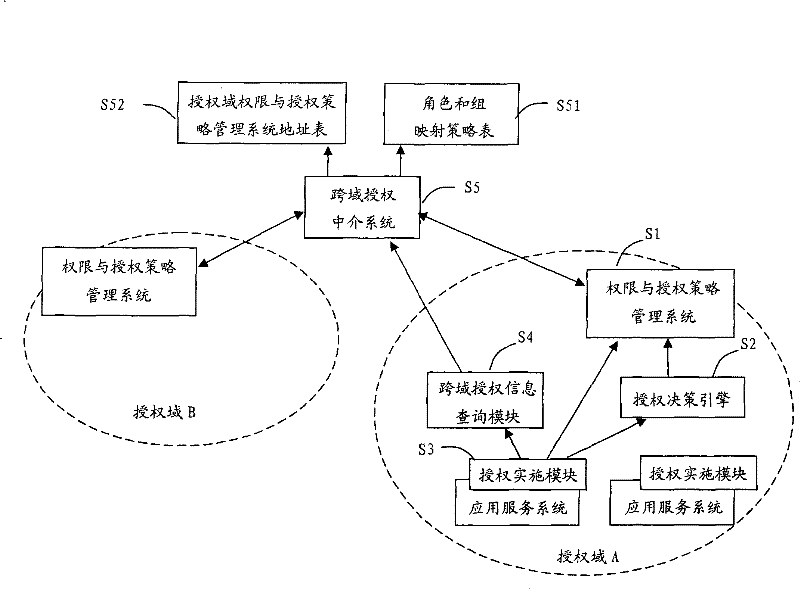
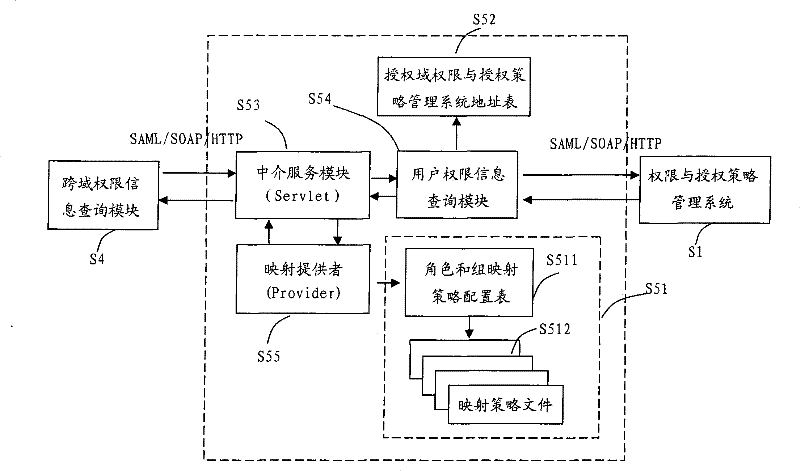
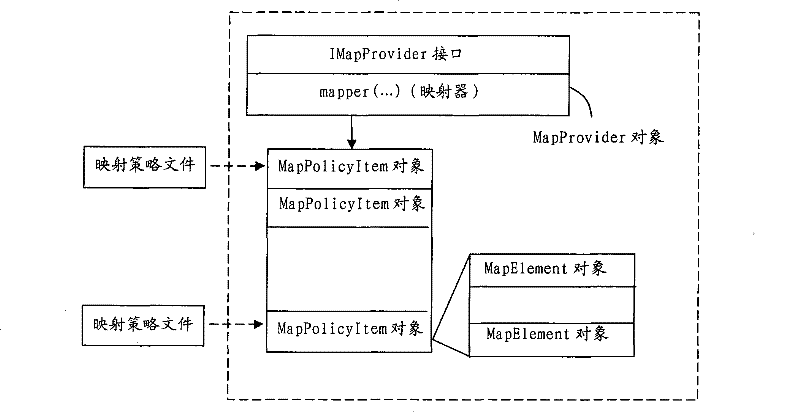
[0058] The overall structure of the cross-domain access control system of the present invention is as follows: figure 1 As shown, Domain A and Domain B in the figure represent different authorized domains. In each domain, one or more application systems provide external services, and the access control system implements resource access control for users, and the access control system is divided into There are two parts, the basic access control system and the cross-domain system, in which the authority and authorization policy management system S1, the authorization decision engine S2, and the authorization implementation module S3 constitute the basic access control system, while the cross-domain authorization intermediary system S5 and the cross-domain authorization information query module S4 constitutes a cross-domain system, and the cross-domain authoriz...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com