Method and system for generating cryptographic-key identification identifier
A technology of identity identification and identifier, which is applied in the field of key identity identifier generation, which can solve the problems that the key has no identity identifier and cannot be reused
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
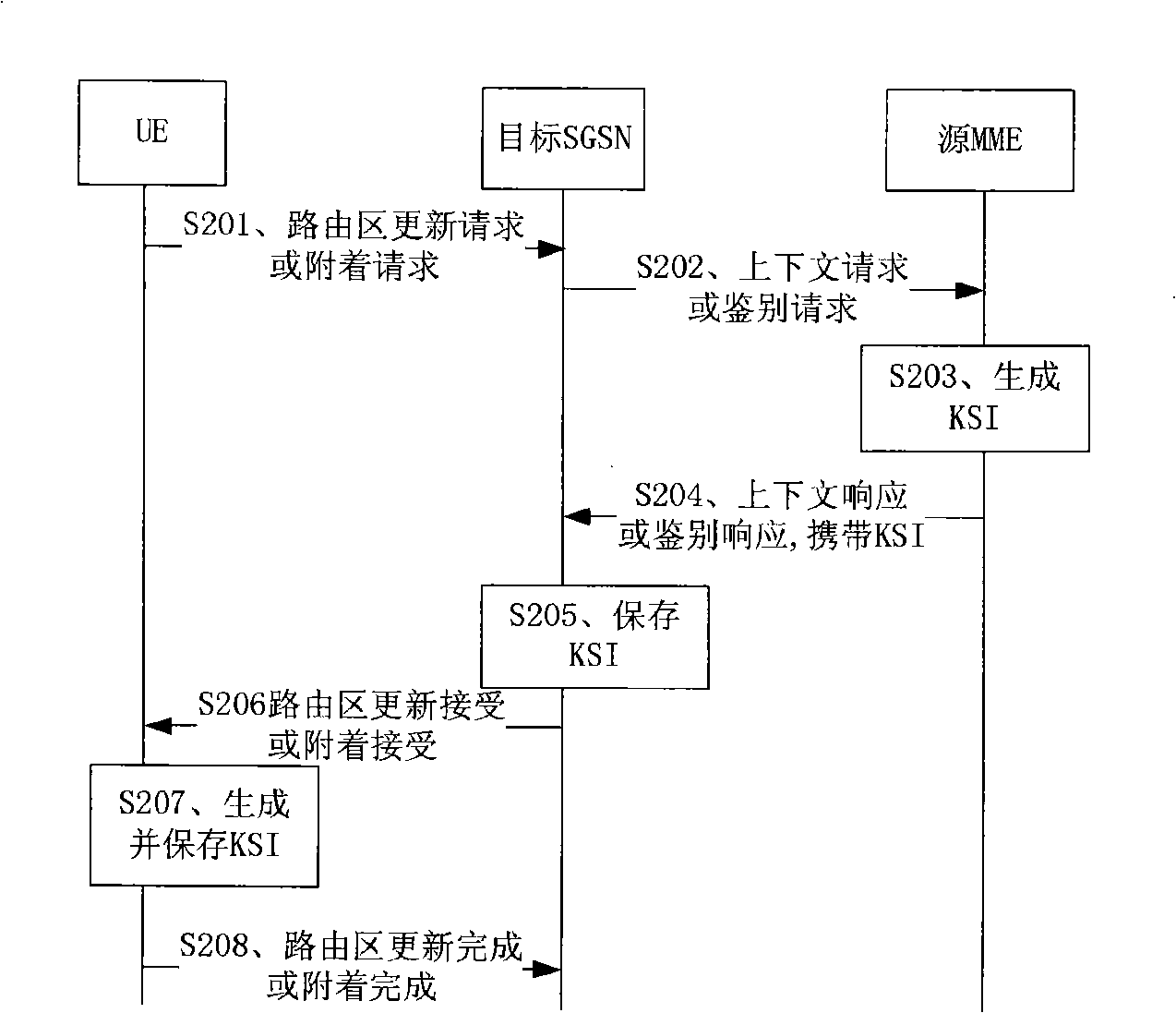
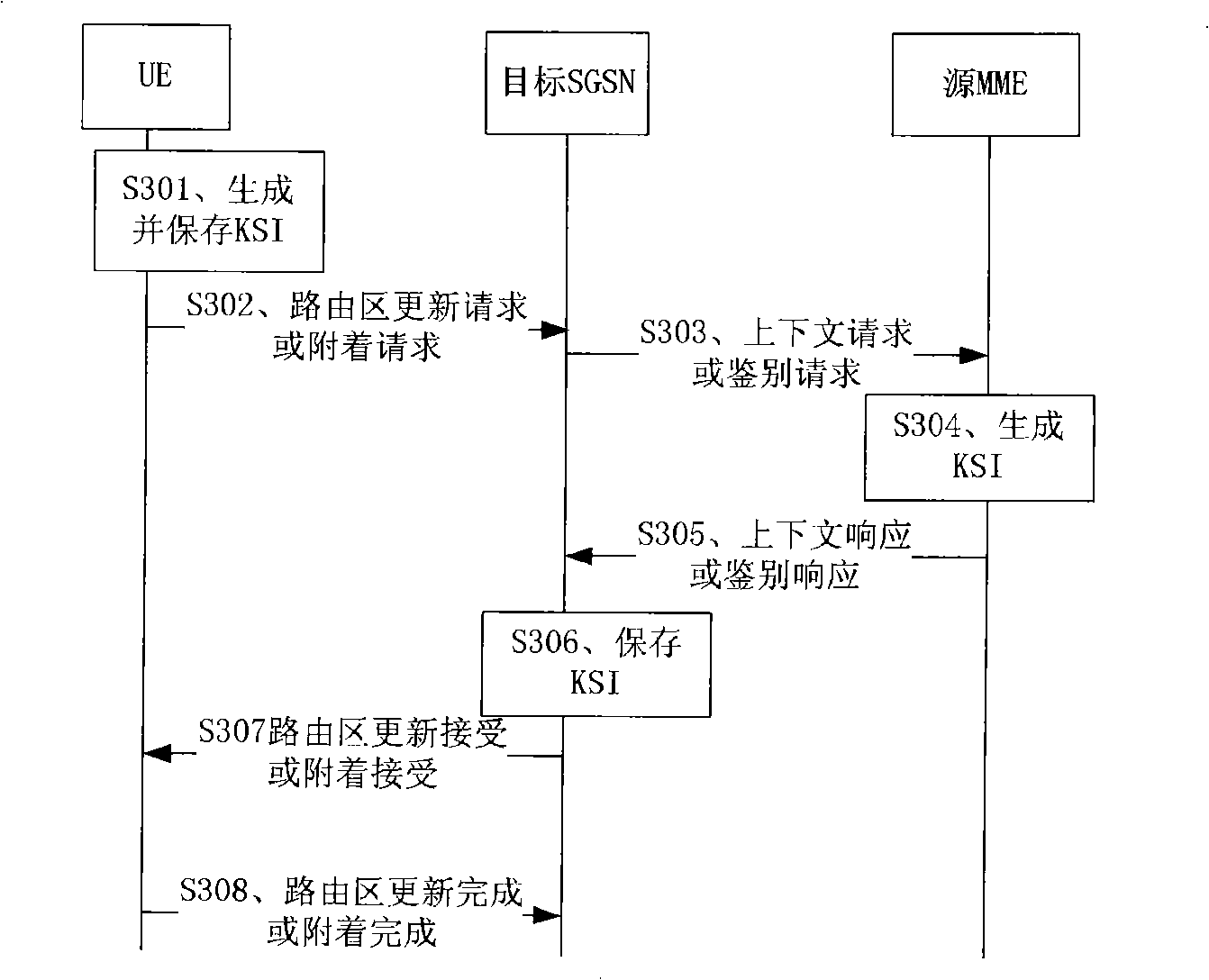
[0072] figure 2 It is the first embodiment of the method of the present invention. This embodiment is a method flow for generating a key identity identifier when EUTRAN is transferred to UTRAN in an idle state, including the following steps:
[0073] Step S201, the UE decides to transfer to UTRAN when idle, and sends a request message for transferring to UTRAN when idle, and the request message can be a routing area update request or an attach request;
[0074] Step S202, after receiving the idle transfer to UTRAN request message sent by the UE, the SGSN sends a request message to the MME, and the request message corresponds to the received transfer request message type, which is a corresponding context request or an authentication request;
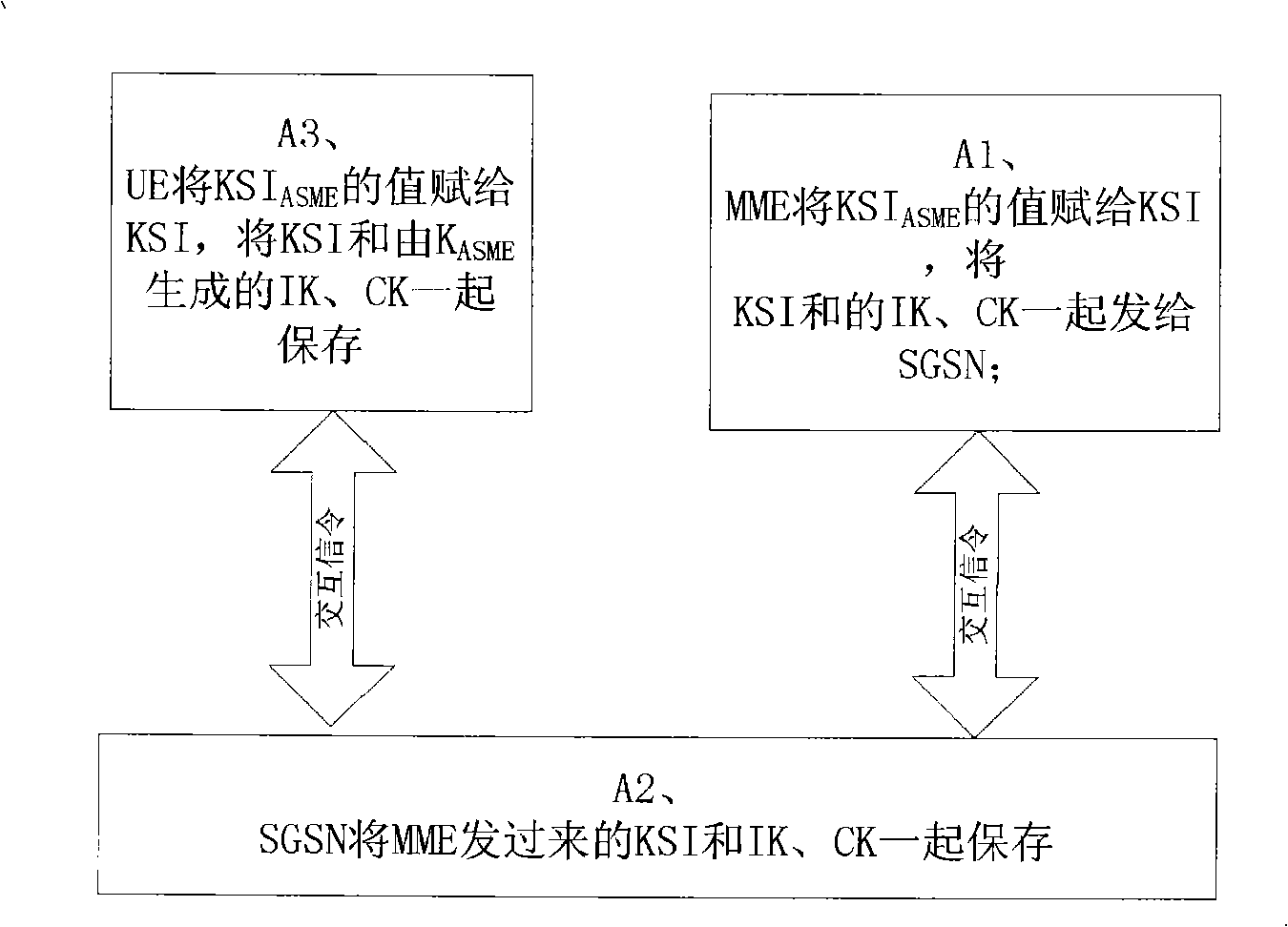
[0075] Step S203, after the MME receives the request message sent by the SGSN, it sends the KSI ASME The value of is assigned to KSI, that is, KSI=KSI ASME , and use K ASME Generate CK and IK;
[0076] Step S204, MME sends context re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com