Malicious code detection method based on SDN (Software Defined Networking)
A malicious code detection and malicious code technology, applied in the field of computer network security, can solve the problem of high computational consumption of malicious code
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
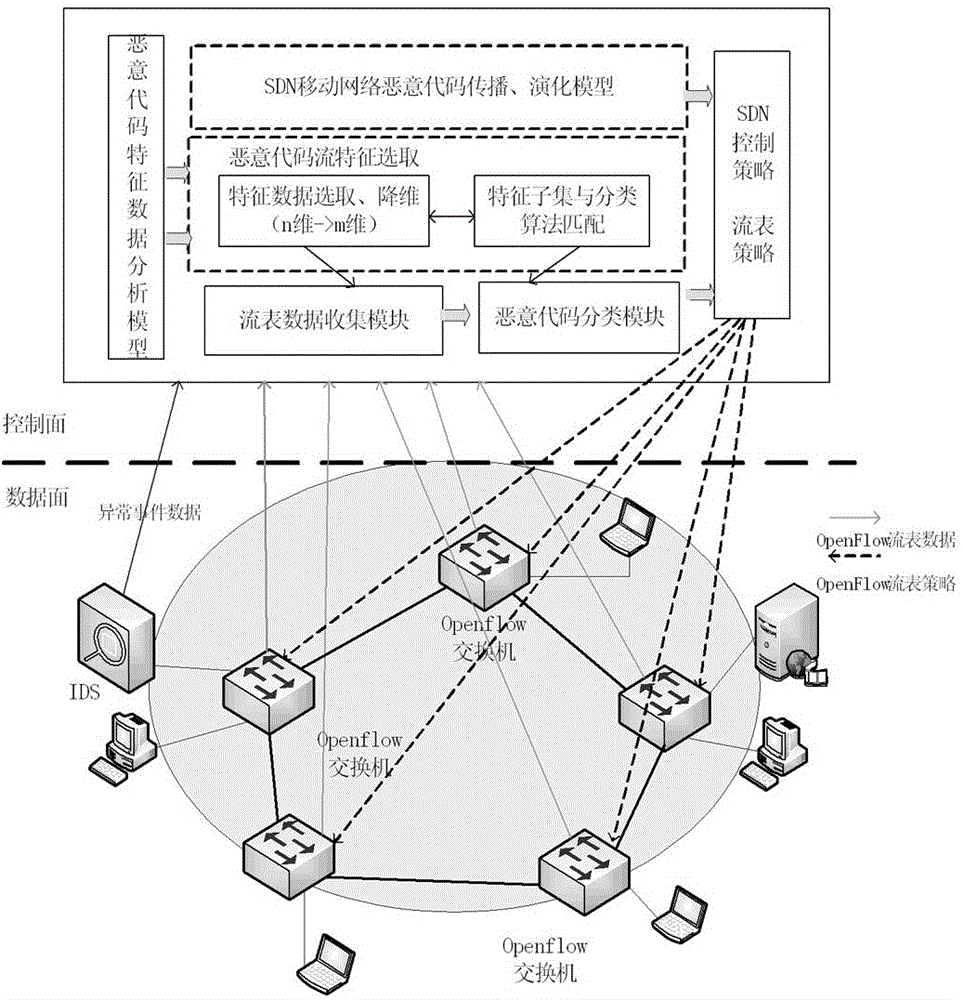
[0019] The roadmap of the present invention is as figure 1 shown.
[0020] In actual detection, the flow table data collection module periodically sends flow table requests to the OpenFlow switch, and the flow table information replied by the switch is transmitted to the flow table collection node through an encrypted channel. According to the result of feature analysis, the flow feature extraction module receives the flow table data collected by the flow table collection module, and extracts related m flow features to form m-tuples. Each m-tuple uses the ID of the switch that collected the data as identification, so that it is possible to monitor which SDN switch discovers a certain type of malicious event. The classifier module is responsible for classifying the collected m-tuples to distinguish which type of abnormal traffic or normal traffic is the traffic during the period.
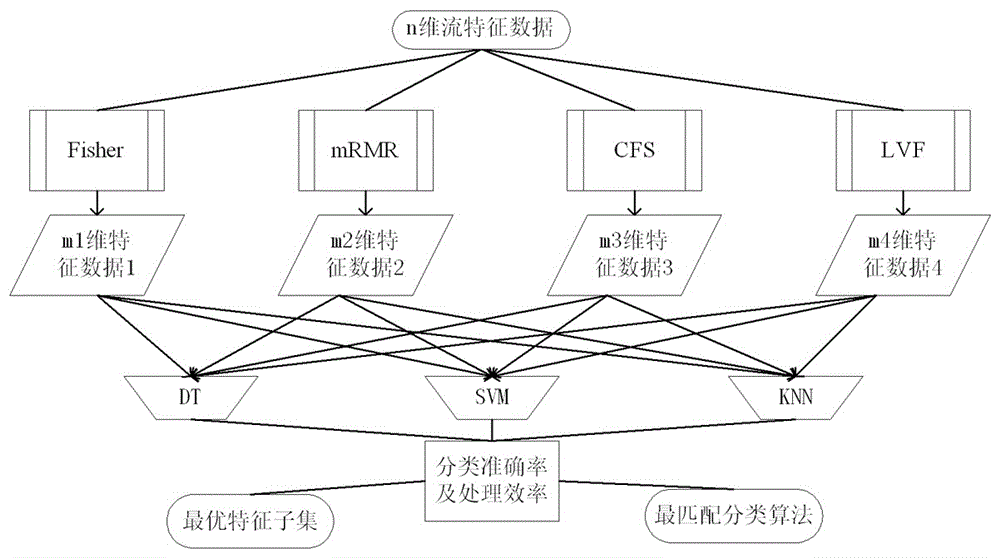
[0021] (1) OpenFlow flow table feature selection and importance ranking
[0022] The OpenFlow ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com