Method and device for setting application permissions
A technology of application programs and permissions, applied in the Internet field, can solve problems such as the inability to monitor and control students' mobile phones, and achieve the effect of timely and effective monitoring and control
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
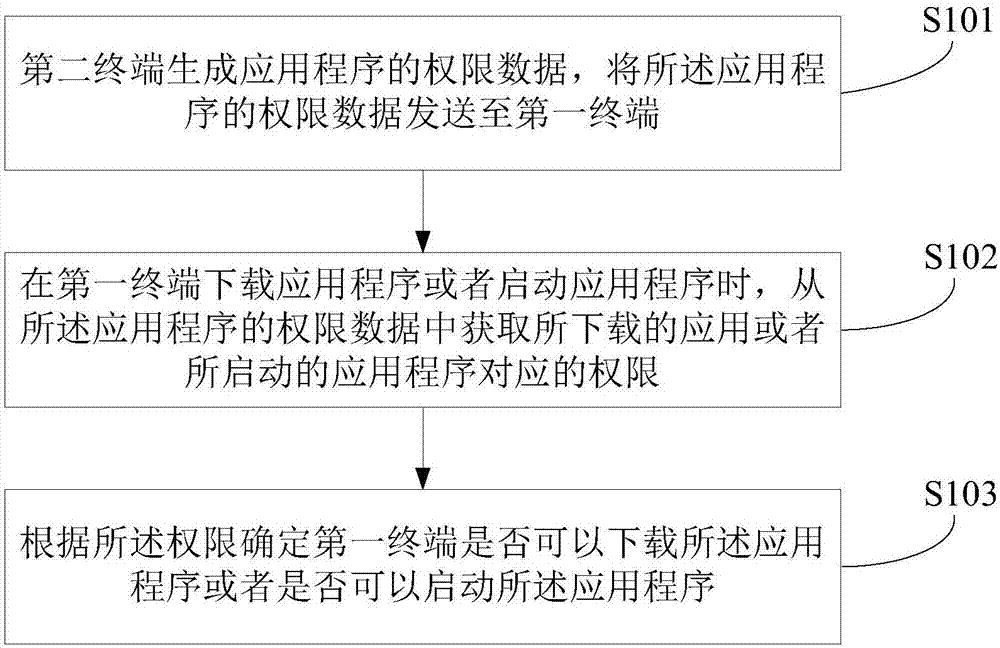
[0051] figure 1 The implementation flow of a method for setting application program permissions provided by the first embodiment of the present invention is shown, and the details are as follows:
[0052] In step S101, the second terminal generates permission data of the application program, and sends the permission data of the application program to the first terminal.
[0053] Specifically, the first terminal in the embodiment of the present invention may be a controlled terminal, for example, it may be a mobile phone used by a student user or other users whose use of some application programs is restricted. In the first terminal, the application corresponding to the method is preset with data communication permission and execution permission. During the running or starting process of other application programs, other application programs can be started or downloaded through the application corresponding to this method. Moreover, in order to ensure the effectiveness of mon...
Embodiment approach
[0057] In addition, as a preferred embodiment of the present invention, the step of generating the permission data of the application program at the second terminal is specifically as follows:
[0058] Receive the parent's permission setting voice, and extract the voice keywords and voice features in the permission setting voice;
[0059] judging whether the voice feature matches the preset voice feature;
[0060] If the voice feature matches the preset voice feature, an instruction corresponding to the voice keyword is executed.
[0061] After receiving the authority setting voice, the second terminal may extract frequency features and the like in the authority setting voice. The text information in the voice is recognized by a voice recognition algorithm, and keywords in the text information in the voice are extracted, such as "allow", "prohibit", "not allowed", "authorize" and so on.
[0062] After extracting the feature of the authority setting voice, compare the feature...
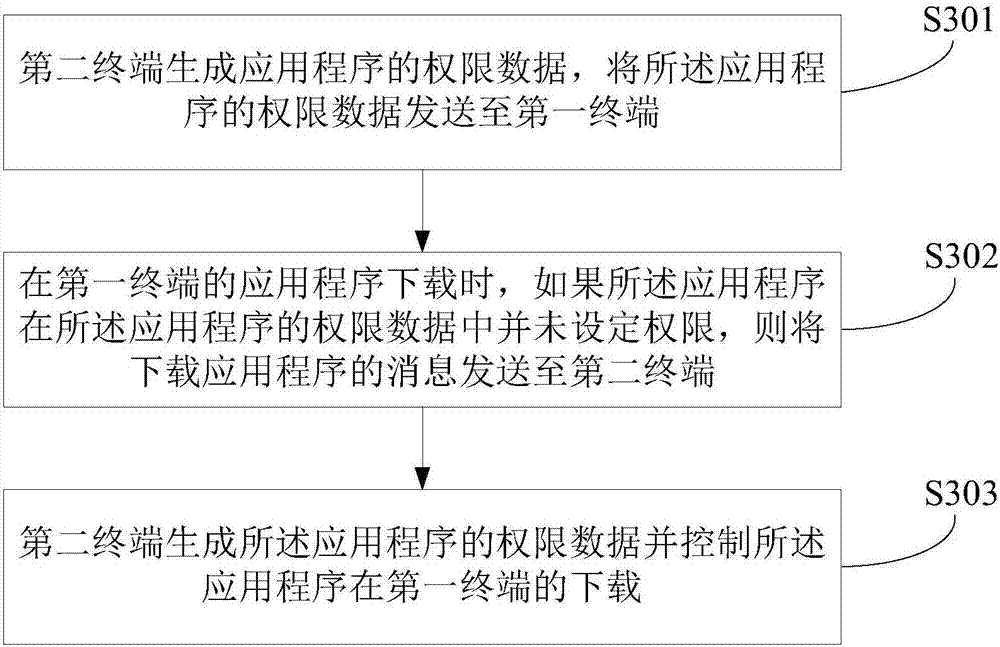
Embodiment 3
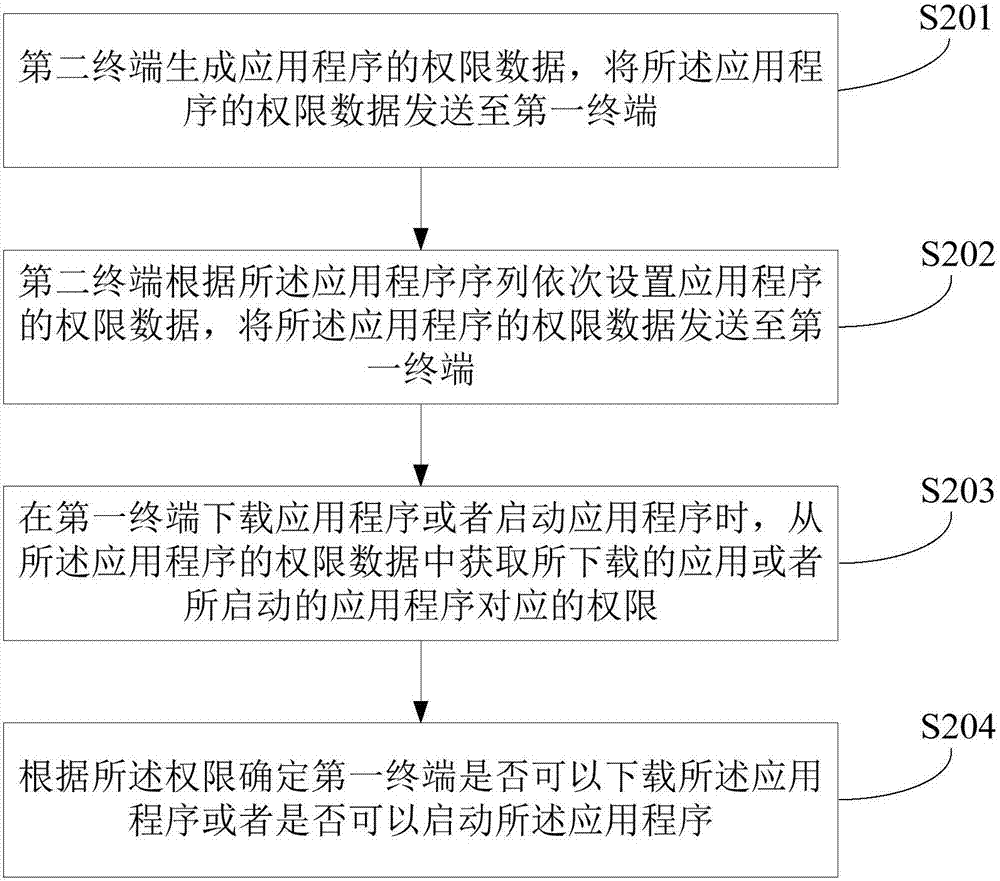
[0072] figure 2 The implementation process provided by the second embodiment of the present invention is shown, and the details are as follows:
[0073] In step S201, the second terminal acquires an application program sequence generated by the number of application programs downloaded by student terminals in the application market.
[0074] Specifically, the application sequence generated by counting the number of application programs downloaded by student terminals in each mainstream application market can be counted. Wherein, the student terminal can be determined according to whether it is the first terminal described in this method, that is, whether it is bound to the second terminal, and can receive the permission data of the application program set by the second terminal, and according to the received permission data Controls the download or launch of an application.
[0075] After counting the number of times the application program is downloaded by the student term...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com