A verification information display method, mobile terminal
A technology for verifying information and mobile terminals, applied in the field of terminals, can solve problems such as machine snatching tickets, password brute force cracking, ticket purchase, etc., and achieve the effect of avoiding automatic identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
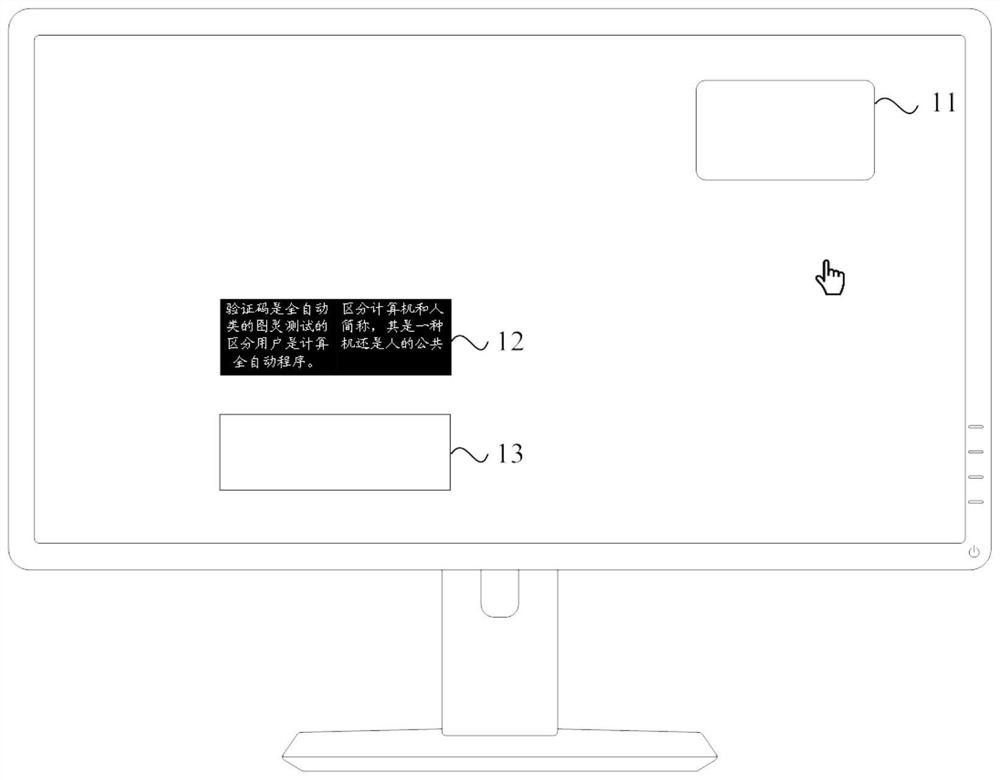
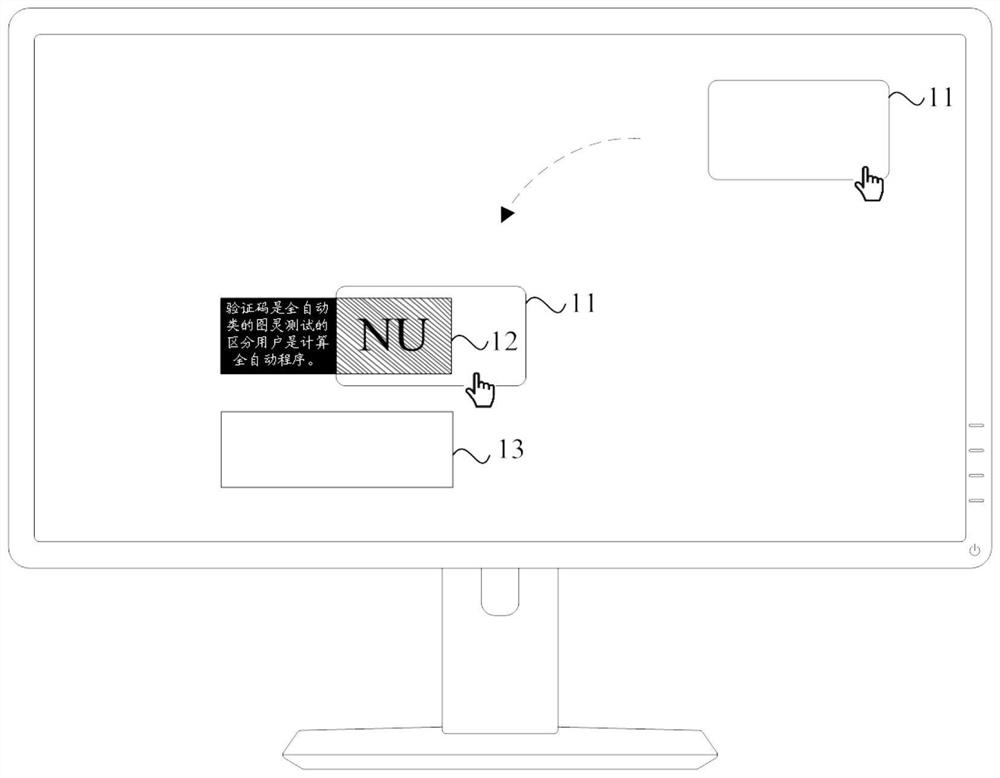
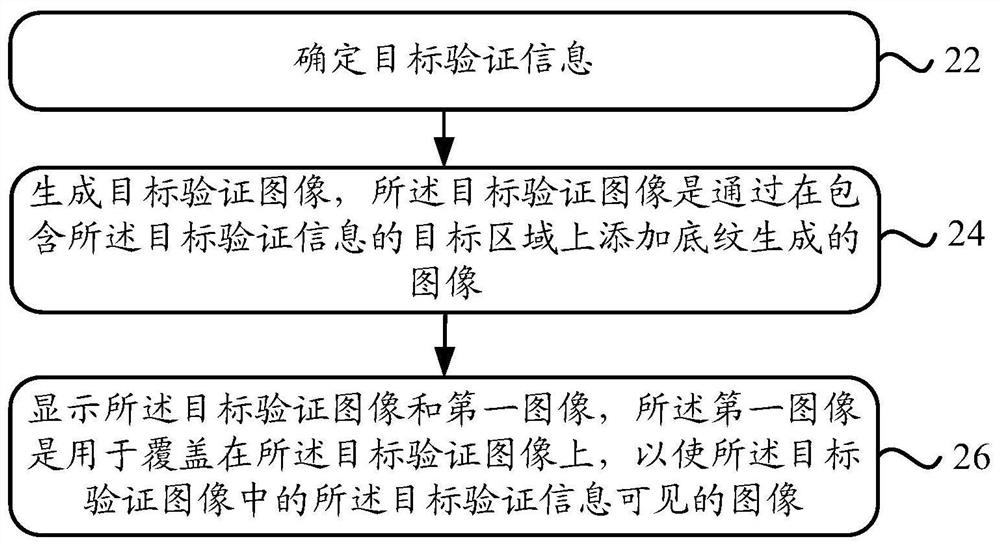
[0039] figure 2 It is a schematic flowchart of a verification information display method provided in Embodiment 1 of the present invention, see figure 2 , the method may be executed by a processor of the mobile terminal, and may specifically include the following steps:
[0040] Step 22, determine target verification information;
[0041] Step 24, generating a target verification image, the target verification image is an image generated by adding shading to the target area containing the target verification information;
[0042] It should be noted that step 22 and step 24 are generally steps performed by the processor in the background, invisible to the user, and the first implementation method may be:
[0043] When it is detected that the mobile terminal is adjusted to an interface that requires input of verification information, a target verification information is obtained based on a random algorithm, for example: a combination of letters and numbers; then, a target ve...
Embodiment 2
[0069] Figure 4 It is a schematic flowchart of a verification information display method provided in Embodiment 2 of the present invention, see Figure 4 , the method may be executed by a processor of the mobile terminal, and may specifically include the following steps:
[0070] Step 42. Obtain a first picture, and the first picture carries a verification code;
[0071] It should be noted that the first implementation of step 42 may be:
[0072] Based on user operations, when the mobile terminal jumps to the verification code display interface, the processor determines the verification code to be displayed based on a random algorithm, such as a combination of letters and numbers, and displays it on the first picture, and then obtains The first picture with verification code.
[0073] The second implementation of step 42 can be:
[0074] Based on user operations, the terminal initiates a request for login, payment, etc. to the server, and the server returns a verification...
Embodiment 3
[0101] Figure 5 It is a schematic flowchart of a verification information display method provided in Embodiment 3 of the present invention, see Figure 5 , the present invention will be described in detail below from the perspective of examples:
[0102] Step 52, determine the first shading and the second shading
[0103] It should be noted that the rules for setting the first shading and the second shading are generally stored locally by the terminal, and then dynamically updated by the server. Therefore, the processor of the terminal can determine the first shading pattern and the second shading pattern based on the locally stored rules. For example:
[0104] A group of mathematical functions with the same slope (first slope) and different intercepts: y=k1x+ib1 (A1 function) realizes the same density curve group in the same shading direction, and obtains the first shading picture 61;
[0105] Use a linear mathematical function group y=k2x+ib2 (A2 function) with a differ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap