Authentication method and system adopting captchas
A verification code and legal technology, applied in the field of verification code verification methods and systems, can solve problems such as normal operation, Internet application system attacks, and easy cracking, and achieve the effect of avoiding automatic identification of illegal programs and improving security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] In order to make the purpose, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
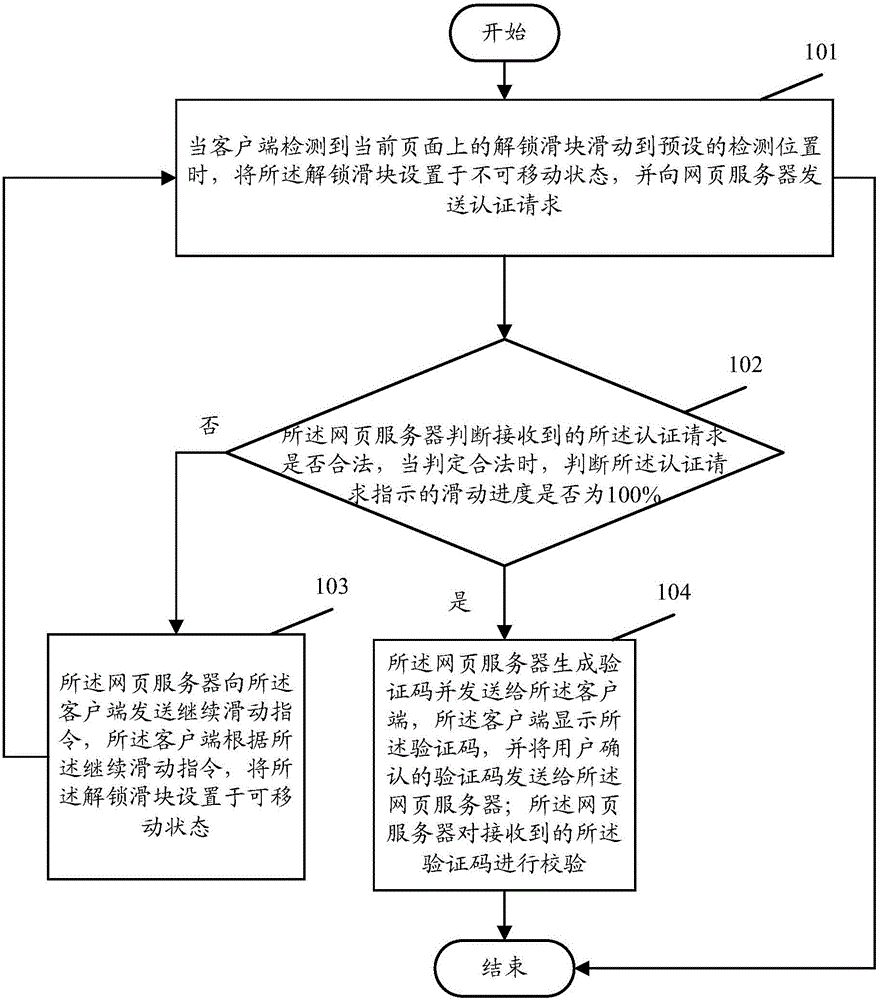
[0024] The core idea of the present invention is to introduce the sliding unlocking technology, and the webpage server controls the display of the verification code on the webpage by monitoring the sliding unlocking action of the user. In this way, during the monitoring process, it can identify Whether the sliding operation is performed manually or triggered by software, so as to ensure that the verification code can be sent to the client and displayed only during manual operation, so that the verification code can be effectively prevented from being automatically recognized by the software.
[0025] figure 1 It is a schematic flow diagram of the method of the embodiment of the present invention, such as figure 1 As shown, this embodim...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap