A method and system for dynamic adaptation and control of electronic file permissions
A dynamic adaptation and electronic file technology, applied in the field of G06 computing, can solve the problems of judging protection loopholes and poor real-time performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
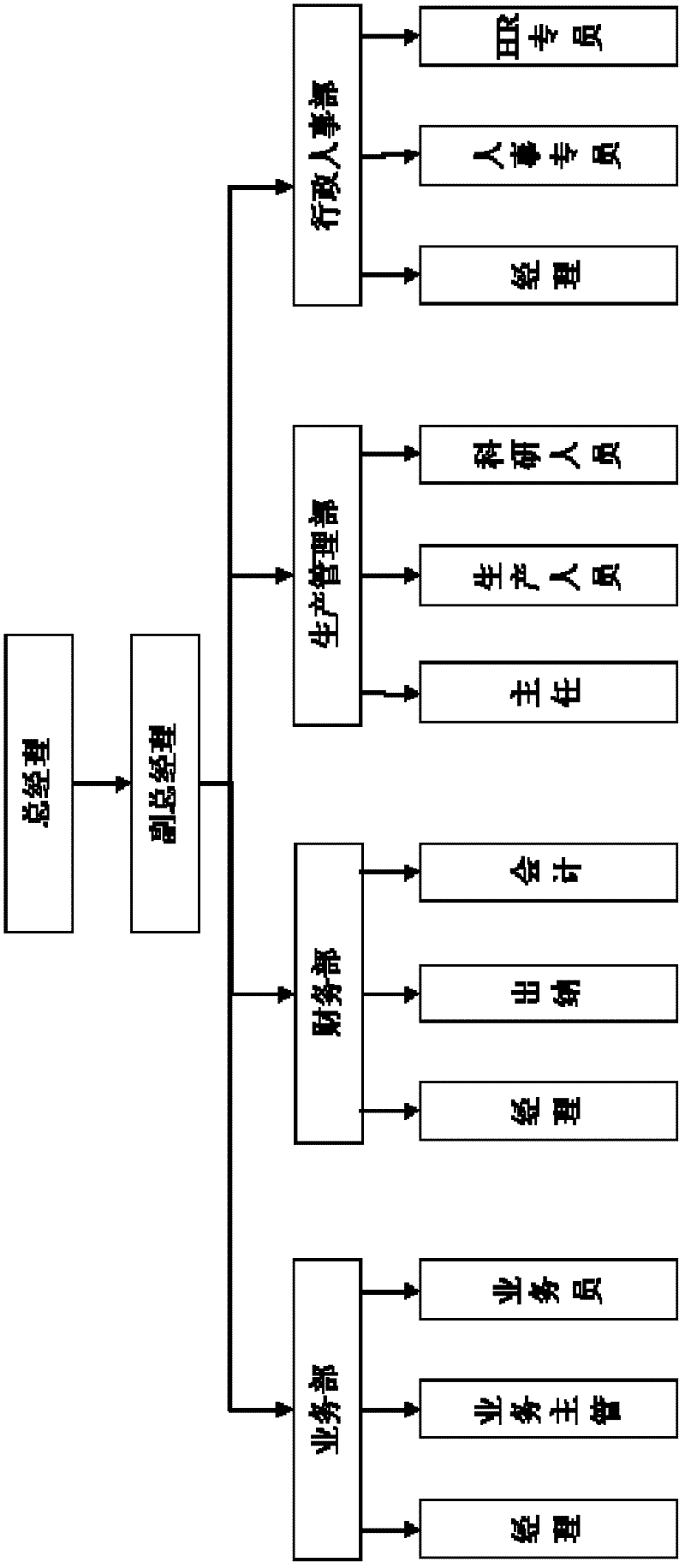
[0047] Example 1, for organizational structure image 3 , specify the method of operation of the present invention:
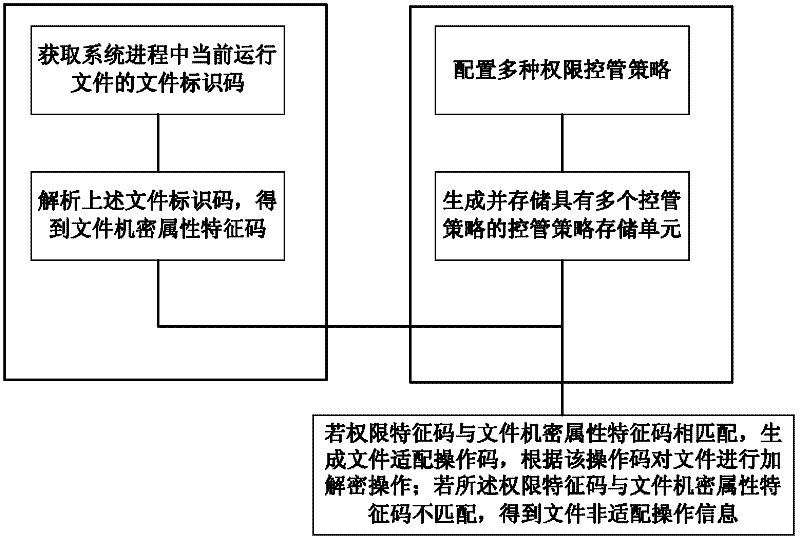
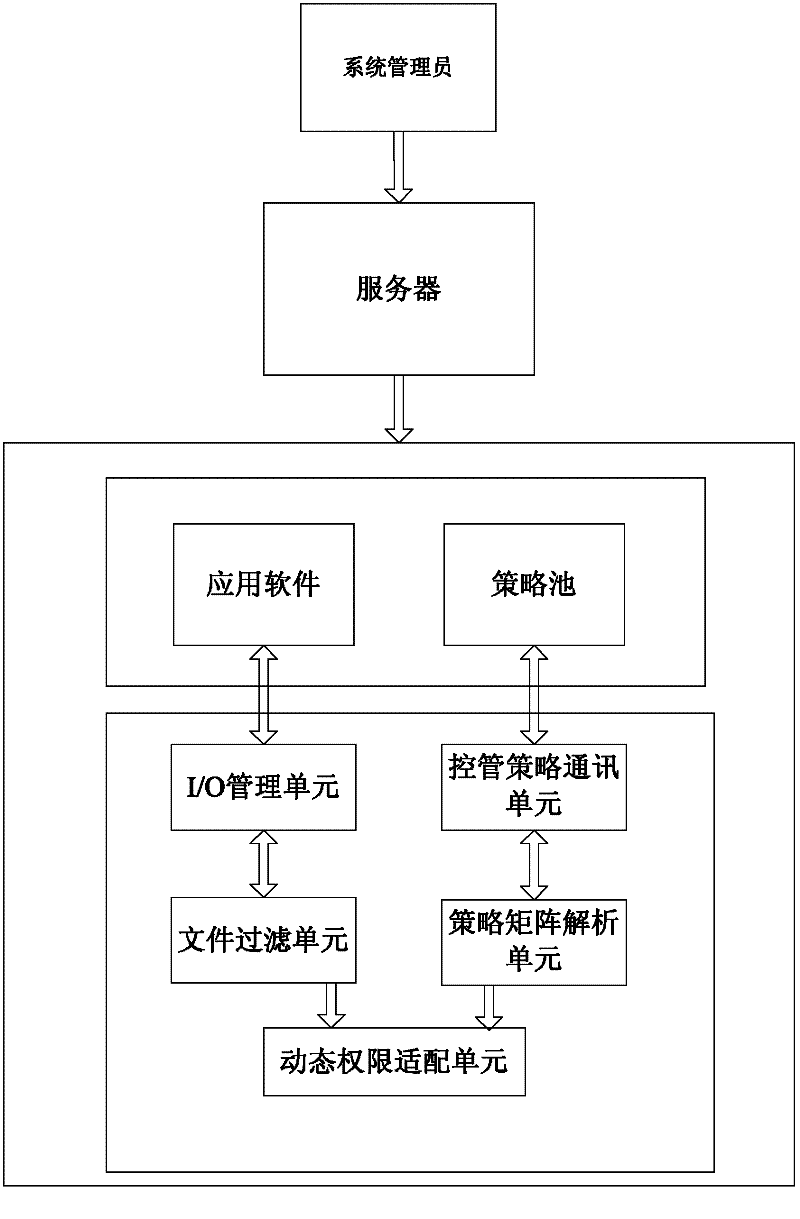
[0048] The system administrator on the server side sets authority control policies for employees according to the needs of the organizational structure, such as the manager of the financial department, and sets the manager to have control over all documents of the financial department, such as the September financial statements, etc., which have the ability to read, edit and delete Permissions, as well as read permissions for documents related to finance in the production management department. It is set that the business department manager has no authority to the above two types of files. At the same time, set access rules for the control files of the finance department. The file control policies and file access rules are stored and delivered to the clients of the two employees, and stored in the permission control policy pool of the clients.
[0049] When ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com