Compiling method and compiling system for obfuscating codes by means of assembly
A technology of code obfuscation and compilation method, applied in the field of NDK compilation, can solve the problems of first cracking of competing teams, code obfuscation, inability to hide system calls, etc., and achieve the effect of reducing software running speed and increasing memory
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
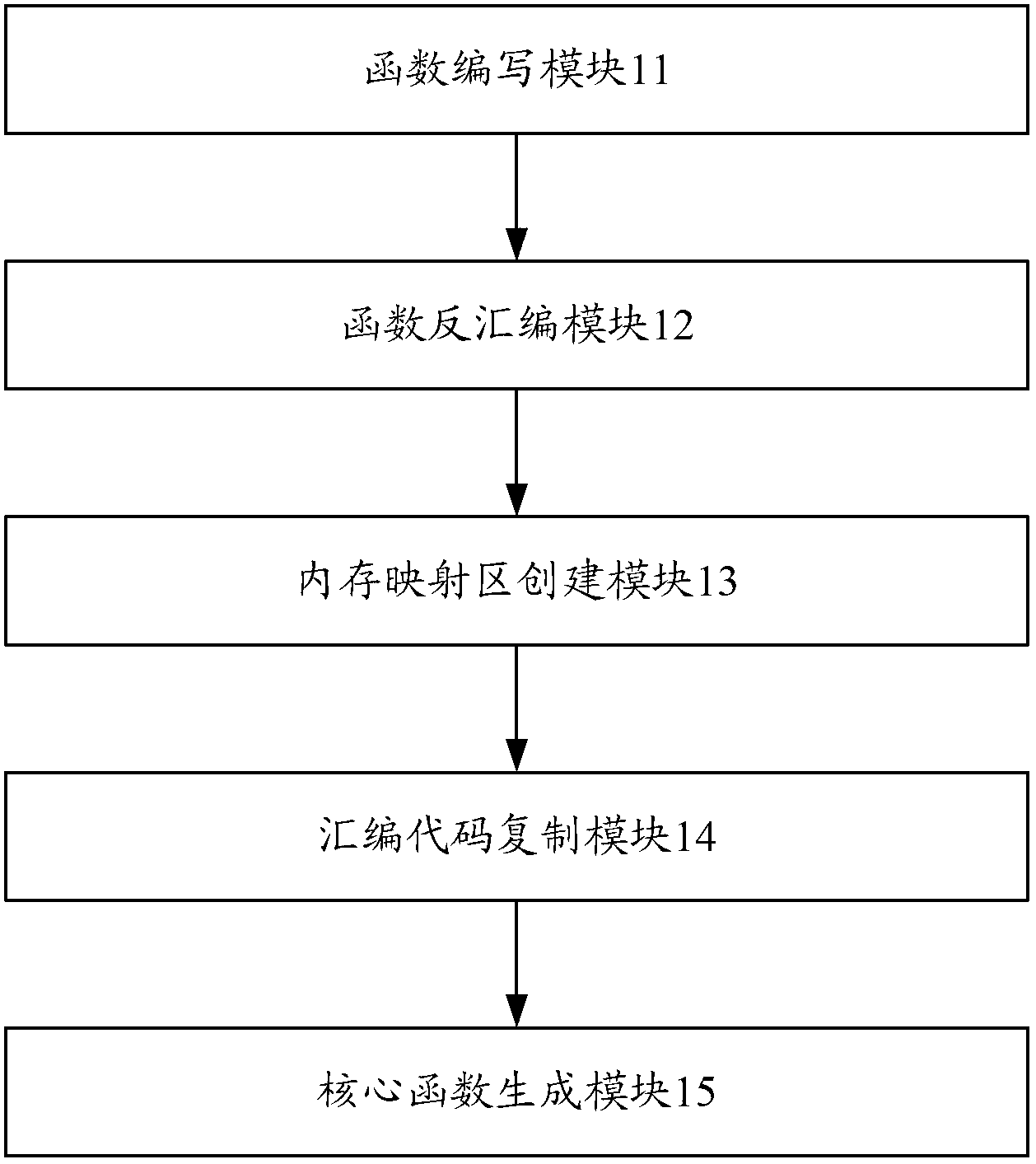
Image
Examples
no. 1 example
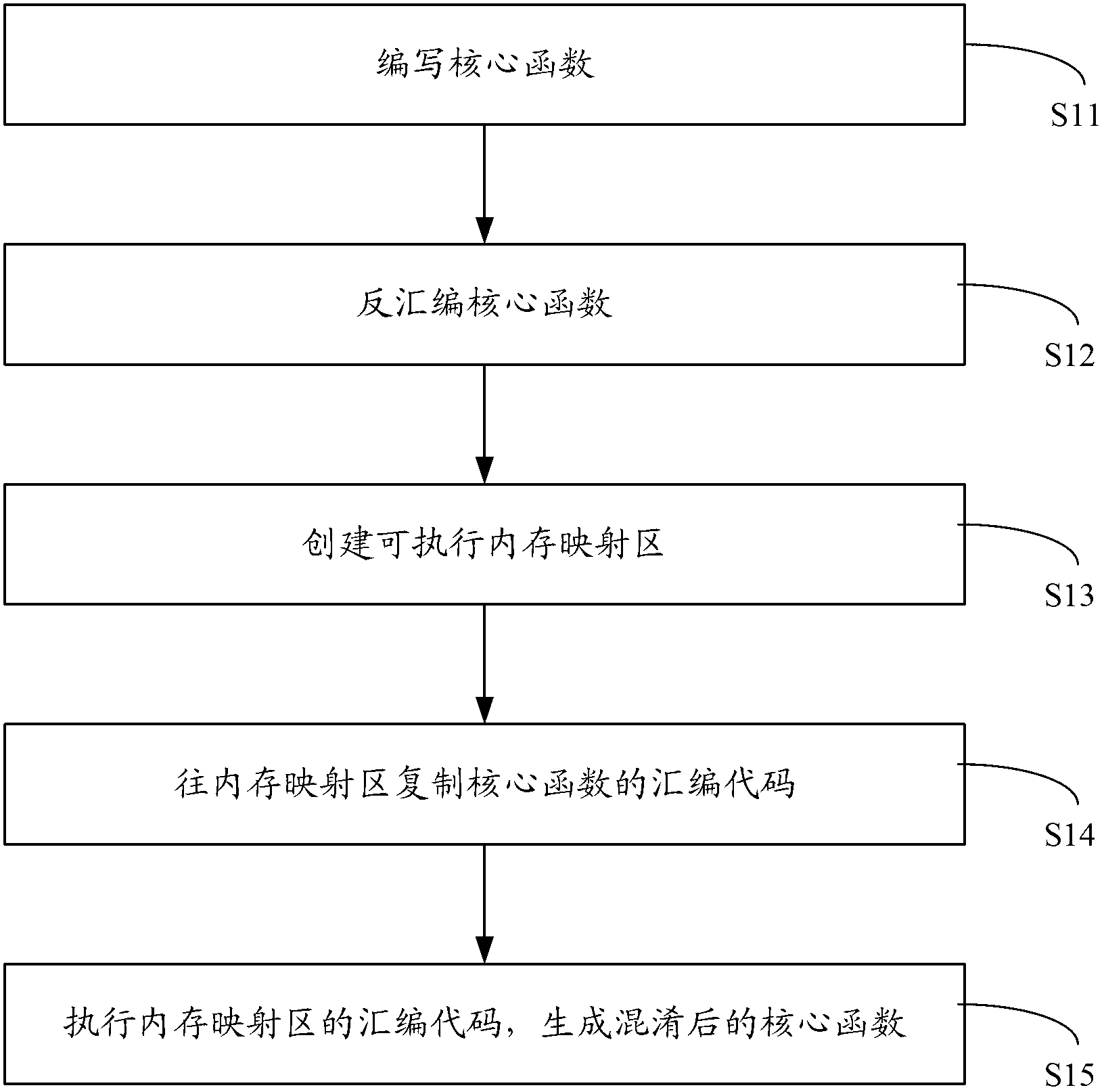
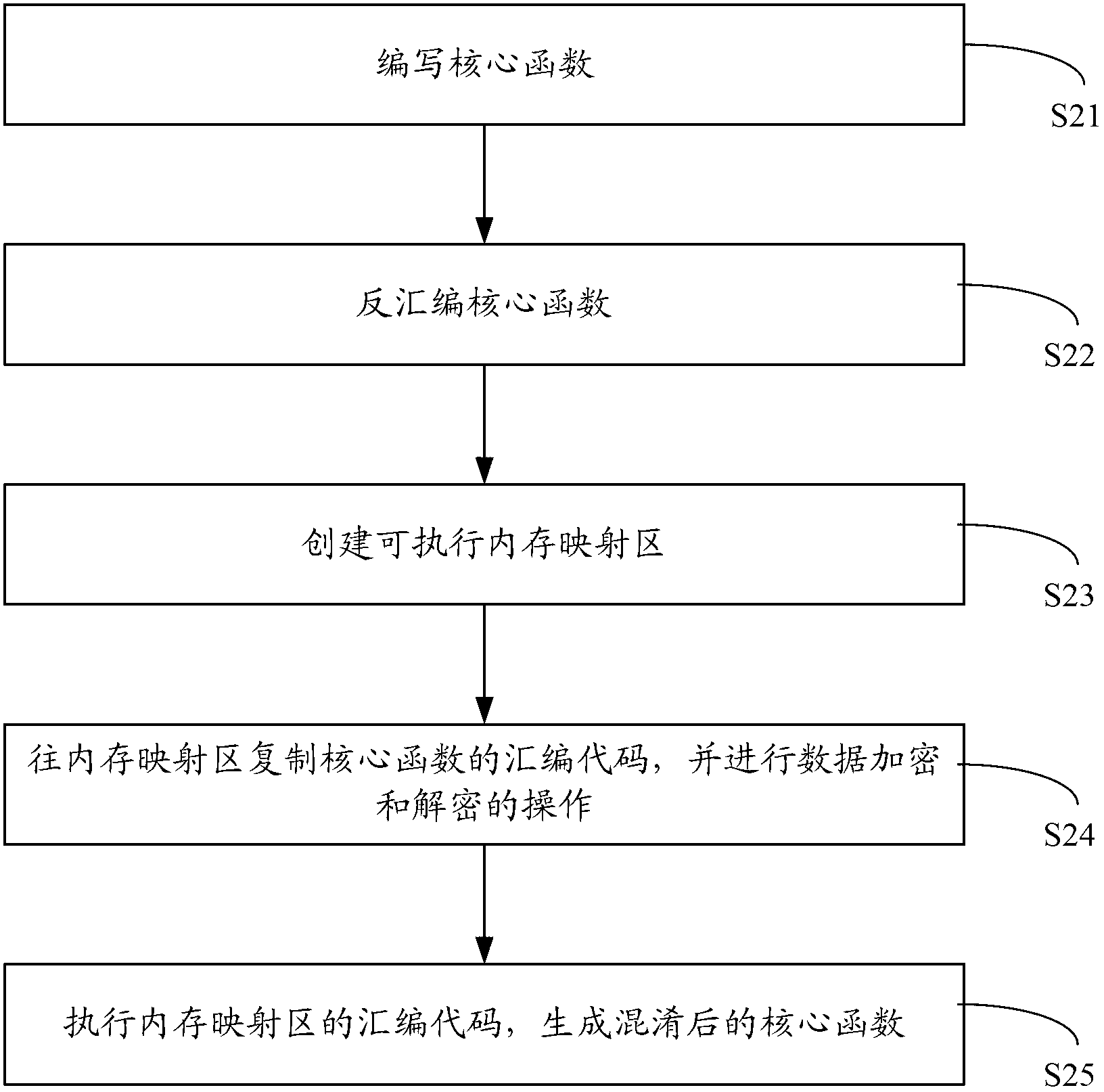
[0040] figure 1 It shows the flow of the first embodiment of the compiling method for implementing code obfuscation through assembly in the present invention. See figure 1 , the following is a detailed description of the implementation steps of the code obfuscation compiling method of this embodiment.
[0041] Step 11: Write the core function.
[0042] In this embodiment, the Android NDK code can be used to write, the core part is extracted and written in an independent function, and the system call or the standard C library is changed into an indirect call. The code is as follows:
[0043]
[0044] Step 12: Disassemble the core function.
[0045] In this embodiment, the GDB debugging tool or IDA Pro Advanced can be used to disassemble the code of the core function into ARM platform code, as shown below. (gdb)x / 20i funcx
[0046]
[0047]
[0048] Analyze the above assembly code:
[0049] 1) The C code corresponding to the C code assembly code combined with fu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com