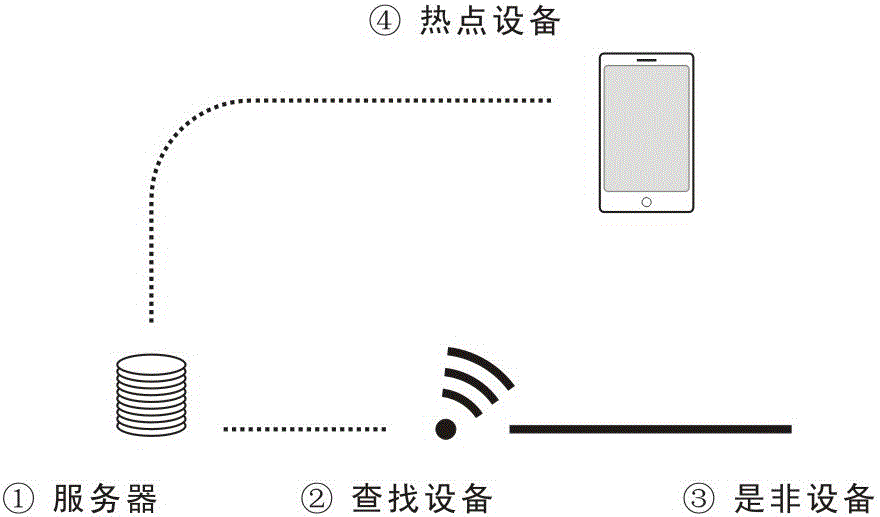
A yes-no-operations approach based on hotspot lookup
An operation method and hotspot technology, applied in the field of information interaction between devices based on hotspot, to achieve the effect of simple information interaction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The above-mentioned technical solution of the present invention has provided the method for generating the electronic key after registration.
[0033] For a user with a temporary access requirement, the user may require the registered user to give him an additional identification. This additional identification can be accepted by the server and be distinguished from registered users. The additional identifier may be a time limit for temporary access or a limit for the number of temporary access.
[0034] Therefore, for adding an additional identification method, the non-operational object described in the present invention may have a corresponding change, this change is not essential, and also falls within the scope of the infringement applicant's claim.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com