A Modified LSTM-Based Approach to Classifying APT Attack Malware Traffic
A malware and traffic technology, applied in the field of network security, can solve the problems of difficult APT attack malware traffic, classification, and difficult to identify APT attack malware traffic, etc., to achieve the effect of increasing detection effect, strengthening pertinence, and strong memory ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
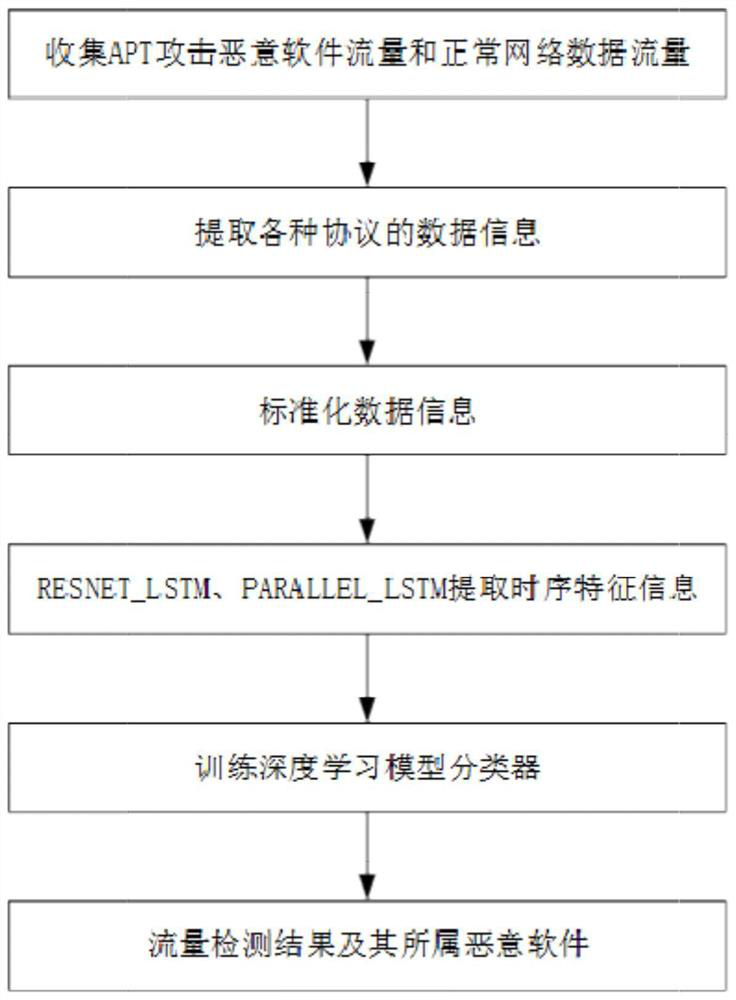
[0070] The collection of abnormal traffic is partly collected by the network, and partly by the collected malware, that is, build a sandbox environment to run the malware, and then collect the malicious traffic information during the corresponding malware process;
[0071] Normal traffic is by visiting the top 10,000 websites ranked by Alexa, and then collecting data on visits to these websites.
[0072] Extract the current static feature information of each protocol in the common malware flow data or / and normal flow data of APT attacks, including the static feature information of the IP protocol, the static feature information of the ICMP protocol, the static feature information of the UDP protocol, and the static feature information of the TCP protocol , Static feature information of the DNS protocol.
[0073] The extracted static feature information of each protocol is shown in the following table:
[0074]
[0075]
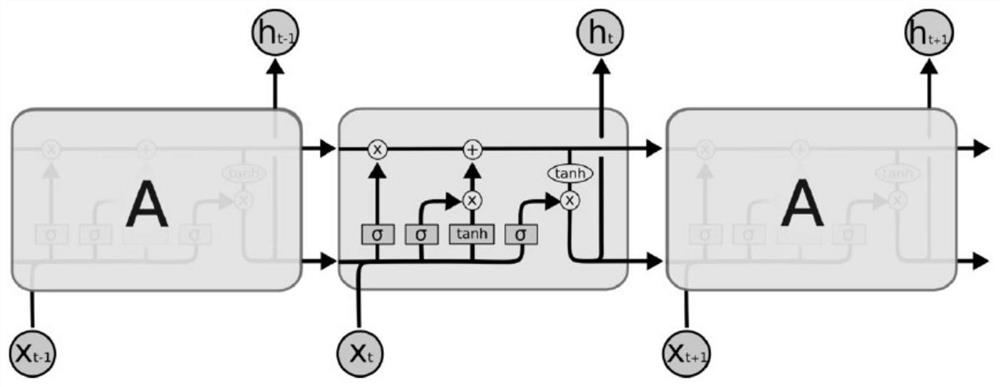
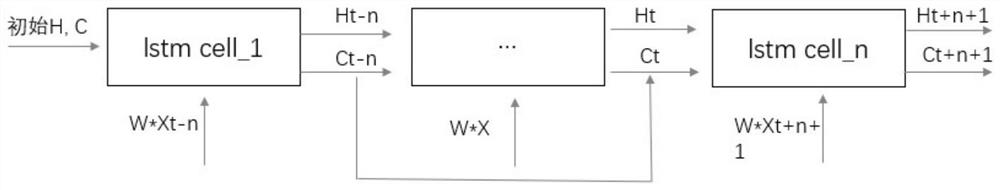
[0076] While extracting the static characteristic...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com