Fault protection method and device, storage medium and electronic device
A fail-safe and failure-prone technology, applied in the field of communication, can solve problems such as difficulty in equipment deployment
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
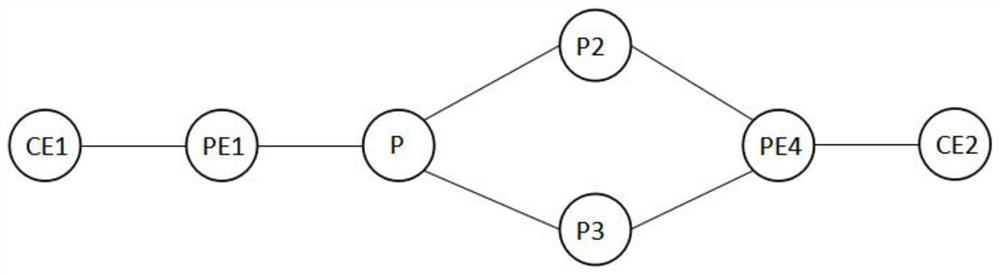
[0063] image 3 is a schematic diagram of intermediate node protection networking according to a fault protection method in an optional embodiment of the present invention, such as image 3 As shown, the intermediate node P2 is the master node, P3 is the backup node, the prefix on P2 is LOC2, a segment identifier SID21 of type END is allocated to P2, and a SID22 of type END.X is allocated to the link P2-PE4. Similarly, the prefix on P3 is LOC3, a SID31 of type END is allocated to P3, a SID32 of type END.X is allocated to the link P3-PE4, and a protection relationship is configured on P3.
[0064]P3, as the standby node of P2, configures the protection relationship, and the configuration method includes at least one of the following:
[0065] Method 1: configure by prefix;
[0066] Specifically, in an optional embodiment of the present invention, P3 needs to protect the segment identifier SID on P2. Configure the prefix that needs to be protected on P3. The prefix covers the...
Embodiment 2
[0075] Figure 4 is a schematic diagram of a service chain protection scenario of a fault protection method according to an optional embodiment of the present invention, as shown in Figure 4 As shown, the transmission from CE1 to CE2 needs to be filtered by the firewall. Under normal circumstances, the service flow is CE1->PE1->P->P2->FW->P2->PE4->CE2, and the firewall FW does not support SRv6. P2 and P3 have SRv6 proxy functions (such as END.AS), that is, they can replace the FW to process SRv6 packets. Before the packets are sent to the FW, the SRv6 packet headers are stripped, and the packets are sent back to the agent after the FW has processed them. After that, the proxy encapsulates the SRv6 packet header and continues to forward it.
[0076] Configure protection relationship on P3. In embodiment two, P3 needs to protect the SID (segment identification) on P2, configure node P2 that needs to be protected on P3, and specify to only protect the SID of static proxy type; ...
Embodiment 3
[0078] Figure 5 is a schematic diagram of a tail node / link fault protection network according to a fault protection method in an optional embodiment of the present invention, such as Figure 5 It should be noted that the prefixes on PE1, PE2, and PE3 are LOC1, LOC2, and LOC3 respectively; VPN neighbors in IPv6 form are deployed between PE1-PE2, PE1-PE3, and PE2-PE3, and PE2 and PE3 Configure the VPN instance VPN1, carry the RT (remote) parameter in the VPN instance, and configure the SRv6 VPN SID at the same time. The VPN SIDs on PE2 and PE3 are assigned as SID2 and SID3; after PE2 receives the private network route released by CE2, it encapsulates it into a VPN route , sent to PE3, the route carries VPN SID, RT, RD and possible constraints.
[0079] In the SR-TE scenario, CE1 sends traffic to CE2 through PE1, P, and PE2 along the specified SR-TE tunnel. The possible format of the packet sent by PE1 is: DA=SID-P,SRH, where SID-PE1, SID-P, and SID-PE2 correspond to SIDs on PE...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com