System and method for privacy protection using identifiability risk assessment
a technology of privacy protection and risk assessment, applied in the field of privacy protection, can solve the problems of identity theft, unauthorized access to personal data, and increased dangers, and achieve the effect of preventing unauthorized disclosure of records
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
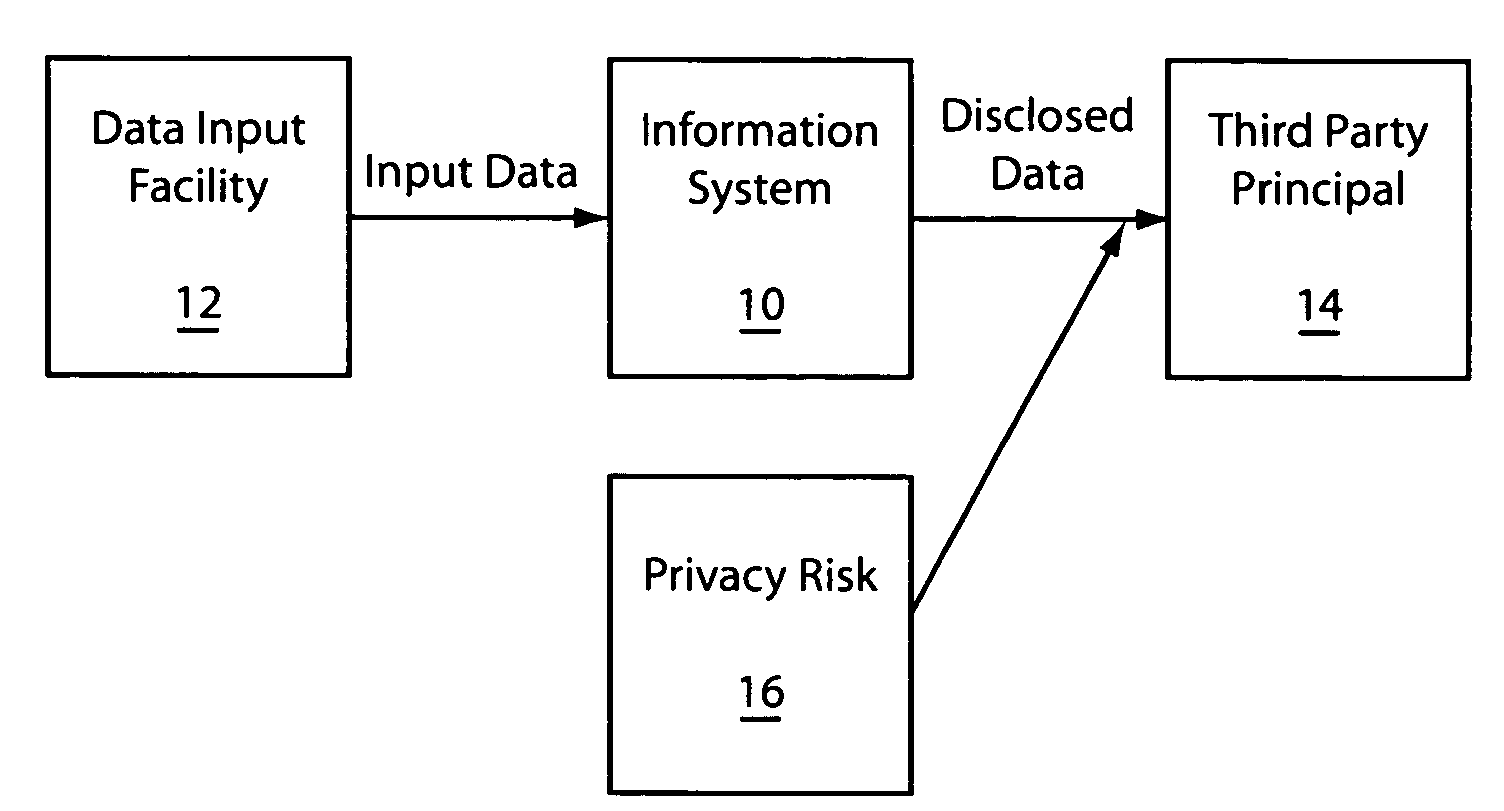
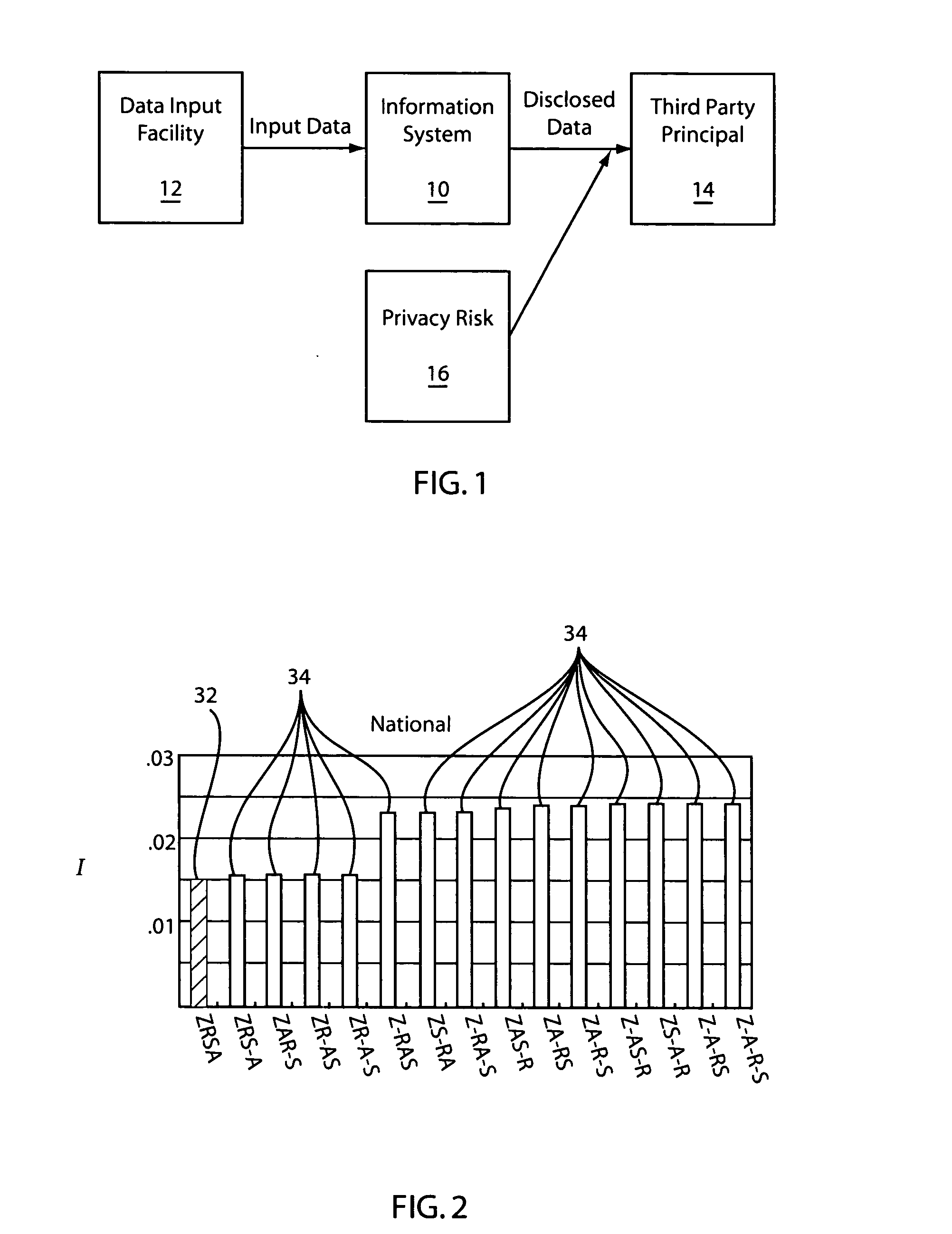
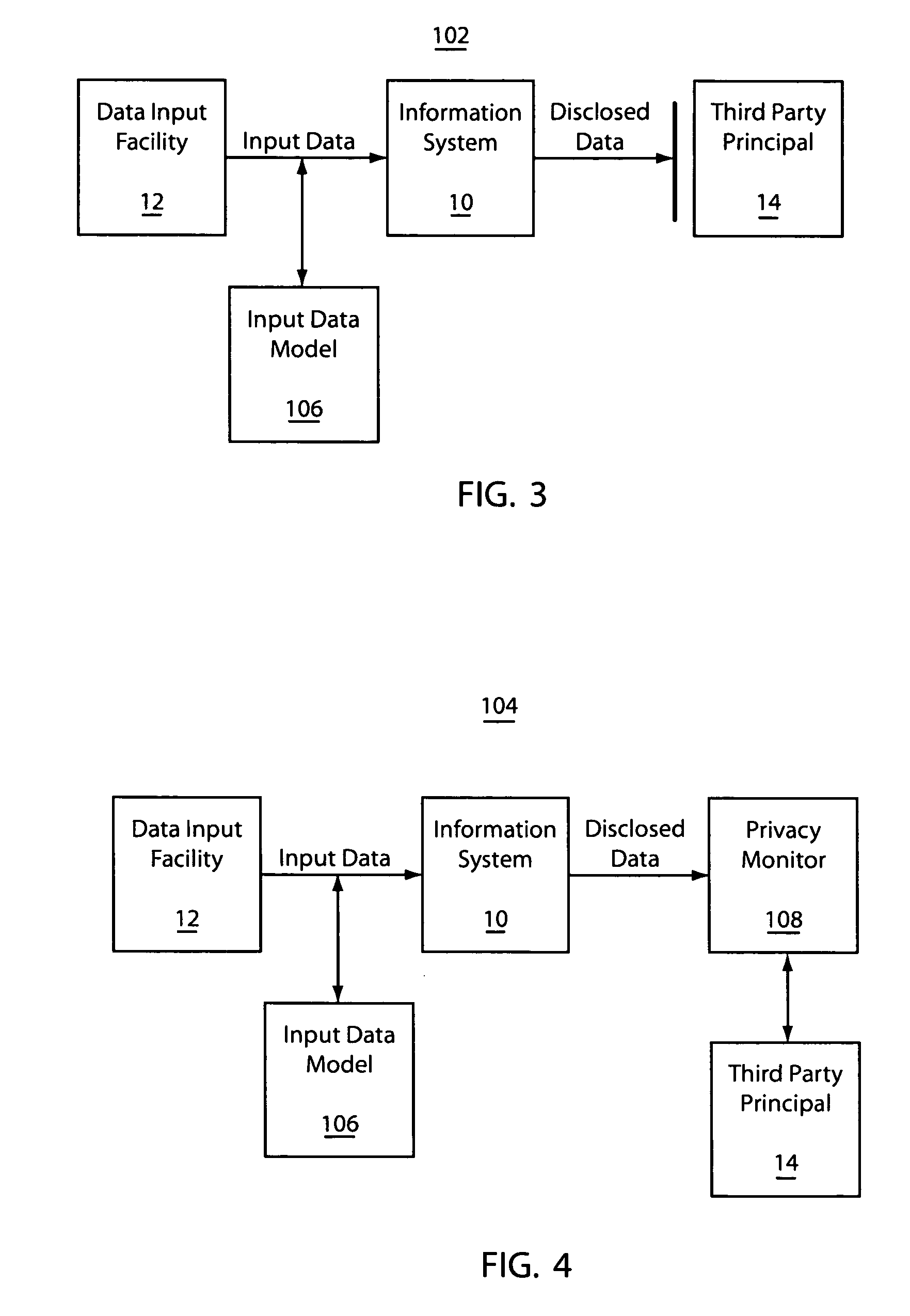
[0025]Embodiments in accordance with the present principles address at least two previously unsolved important problems of privacy protection arising in business and government information systems. These problems include evaluating and managing a tradeoff between privacy protection and business efficiency, and quantifying the privacy risks associated with various business operations. The present embodiments provide systems and methods for evaluating and managing the tradeoffs between business efficiency and privacy protection.
[0026]The systems and methods are preferably based on a privacy risk quantification method for the estimation of the numeric value of privacy risk associated with a particular use of protected information. An organization's employees cannot be relieved from the duty of making their own, frequently highly subjective, estimates of the risks, and can be provided with a system which will automatically compute the risk value and keep the records of the value, the em...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com