Method of linking network equipment and invading detection system
An intrusion detection system and network equipment technology, applied in the field of network security, can solve problems affecting normal use, achieve simple implementation, and improve the overall protection ability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
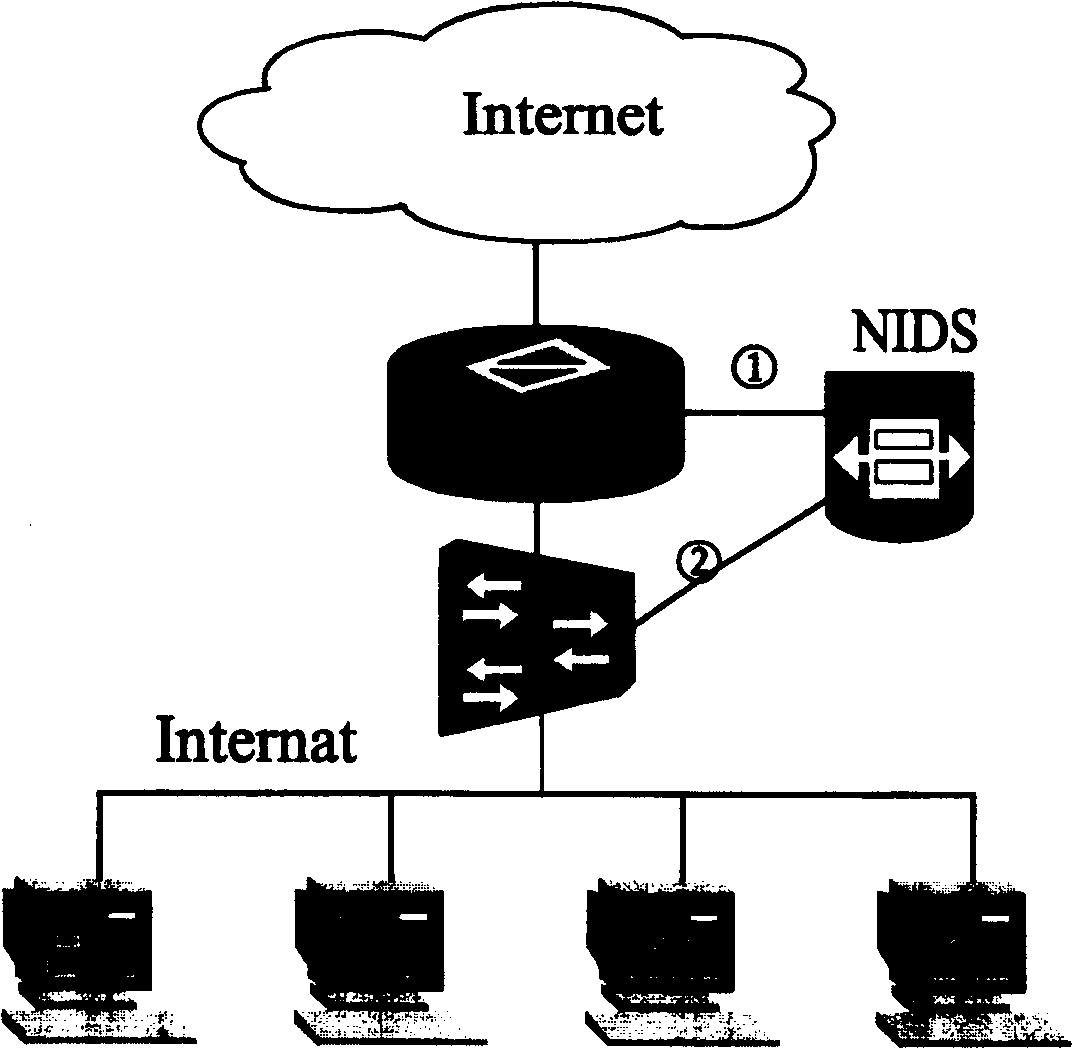
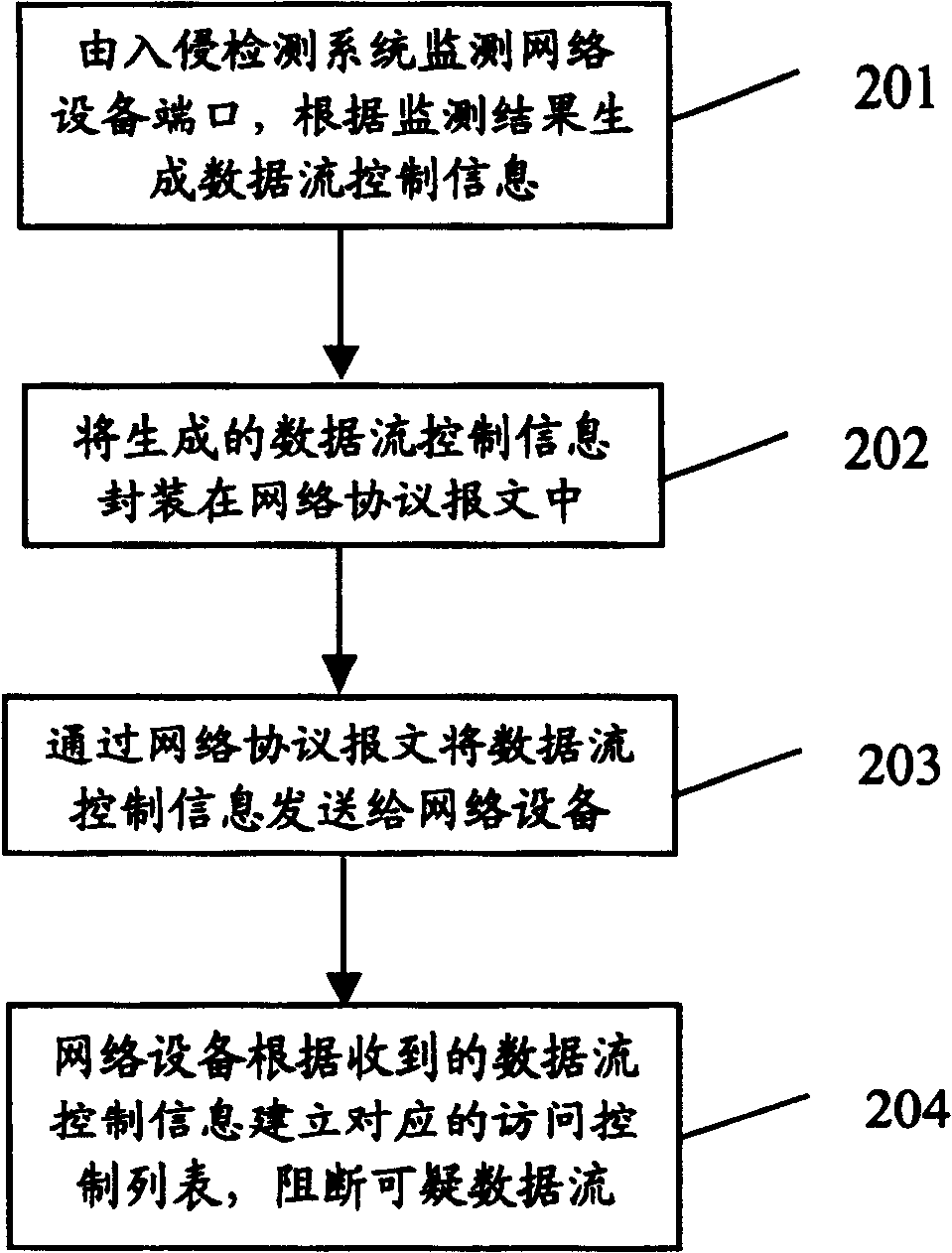
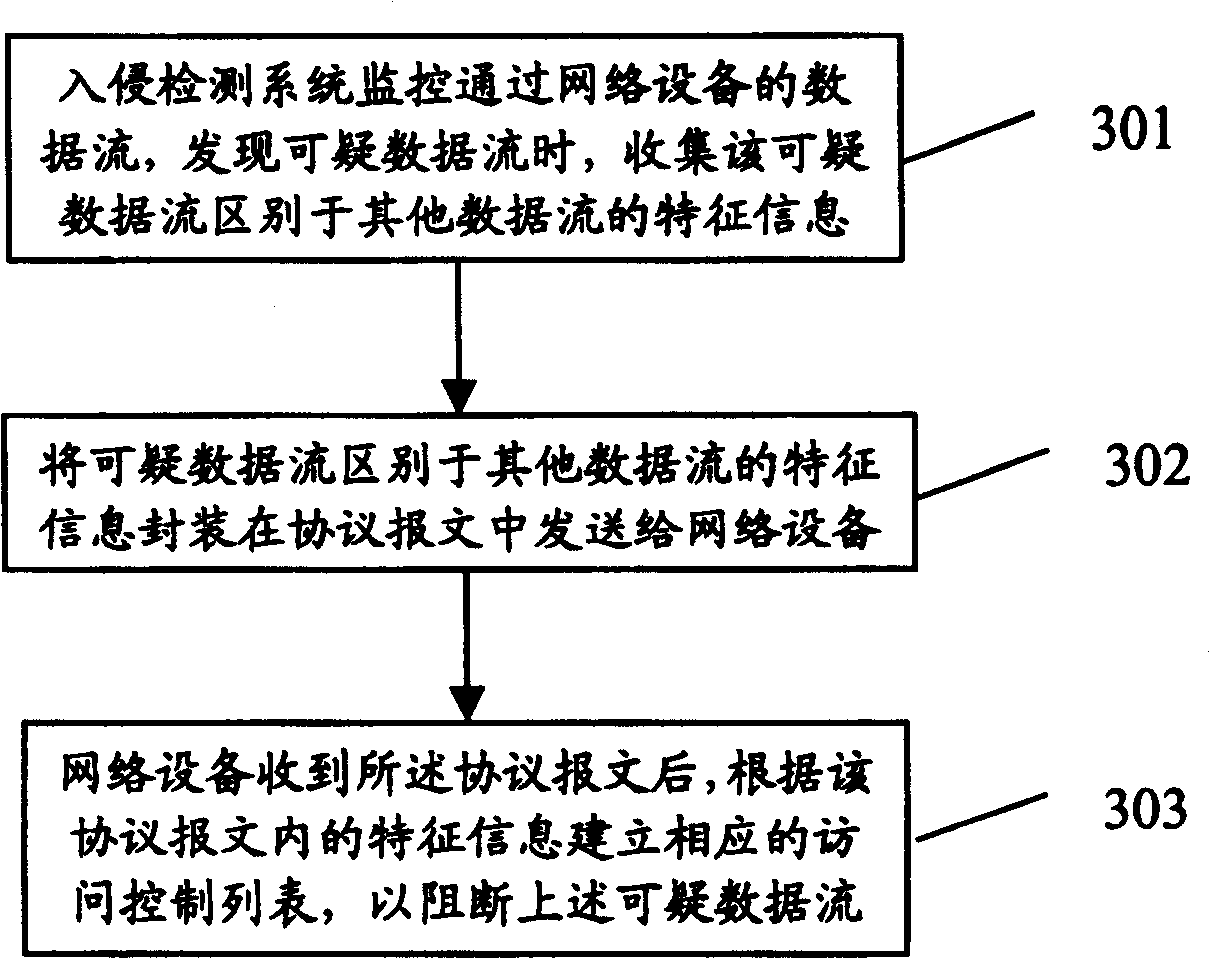
[0032] The core of the present invention is to set up listening port on the network equipment, copy all the data messages that start the intrusion detection port to the intrusion detection system, detect whether these data streams are offensive by the intrusion detection system, and report to the network equipment according to the detection result. Send the characteristics of the data flow that needs to be blocked, and the network device implements the blocking of the data flow through the ACL (Access Control List) according to the characteristics of these data flows.
[0033] Those skilled in the art know that intrusion detection refers to collecting information from several key points in a computer network or computer system and analyzing it to find out whether there are behaviors violating security policies and signs of being attacked in the network or system. The combination of software and hardware for intrusion detection is IDS (Intrusion Detection System). The network i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com