Acquisition method of authentication policy, authentication method, authentication device, communication device, base station and terminal
An authenticator and policy technology, applied in the field of authentication, can solve problems such as authentication failure, unable to inform MS network authentication policy, etc., and achieve complete authentication method, complete authentication object and authentication method, and complete authentication method. rich effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
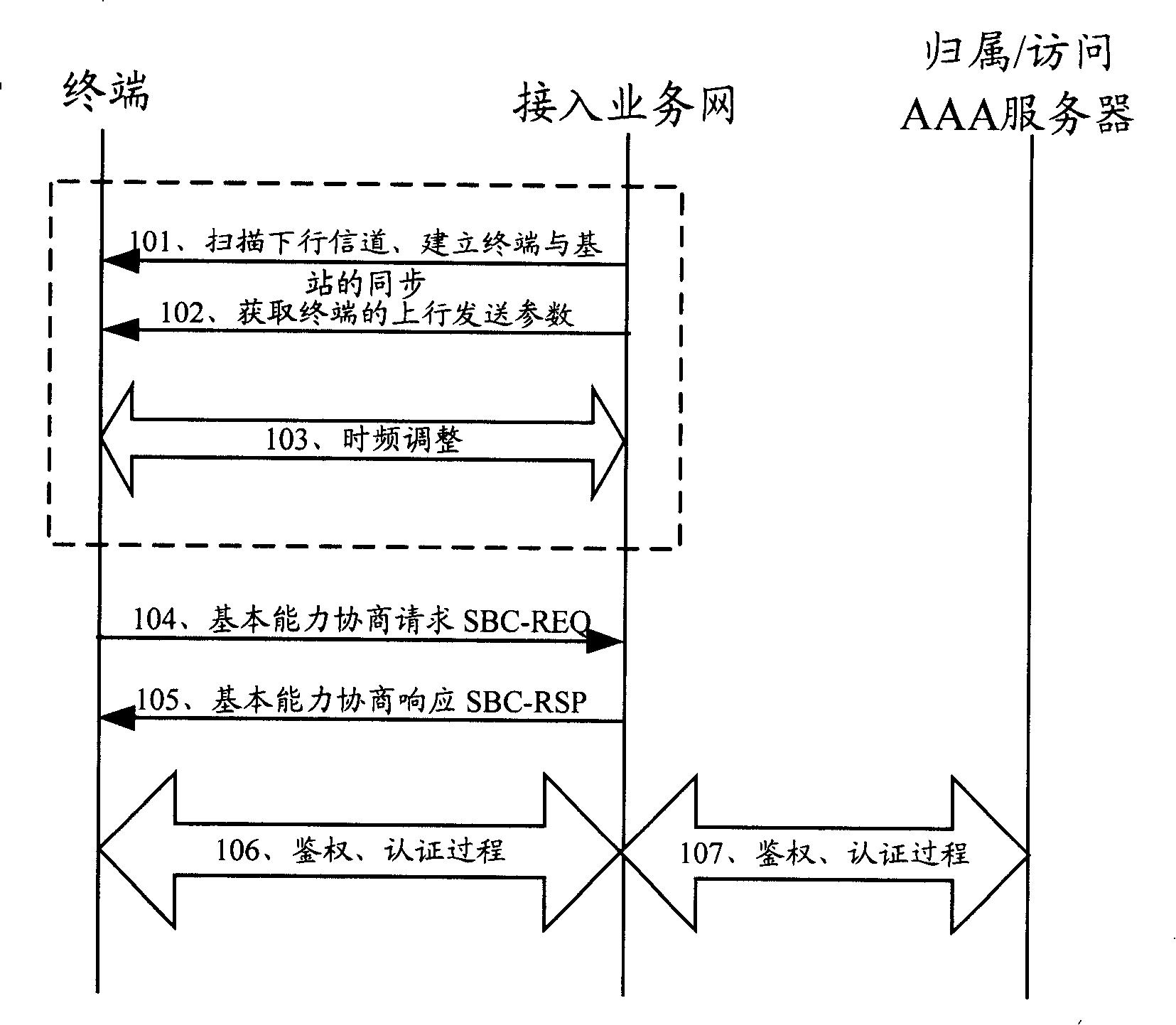
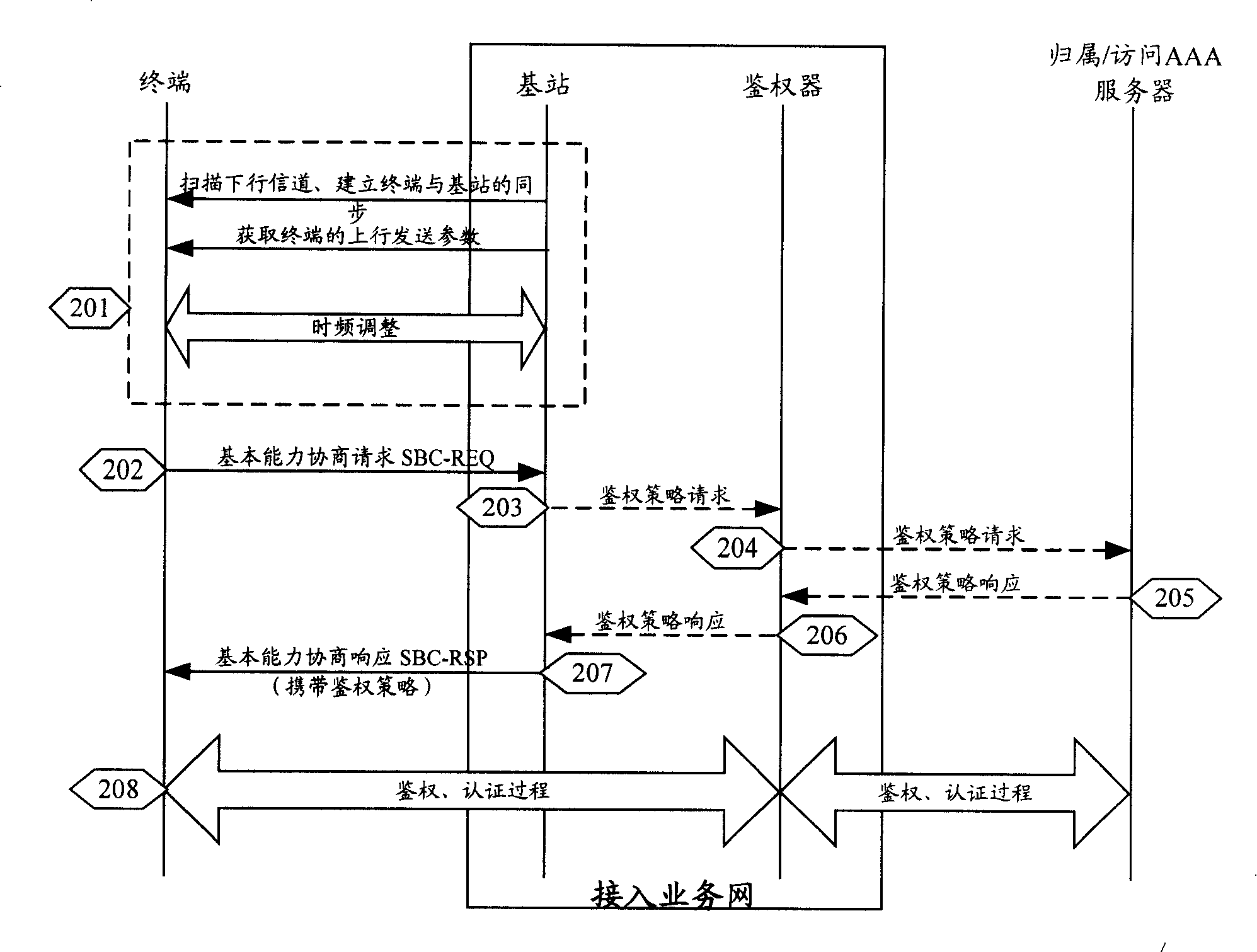
[0123]The present invention also provides a first implementation manner of a base station, where the base station 610 is located in the communication system 600 . The communication system includes a base station 610 and an authenticator 620 . The base station 610 includes an authentication policy processing unit 611, configured to add an authentication policy including an indication that an authentication object is a user and / or a device in a network discovery and selection message. The base station 610 is configured to deliver the network discovery and selection message carrying the authentication policy to the terminal during the network discovery and selection phase.
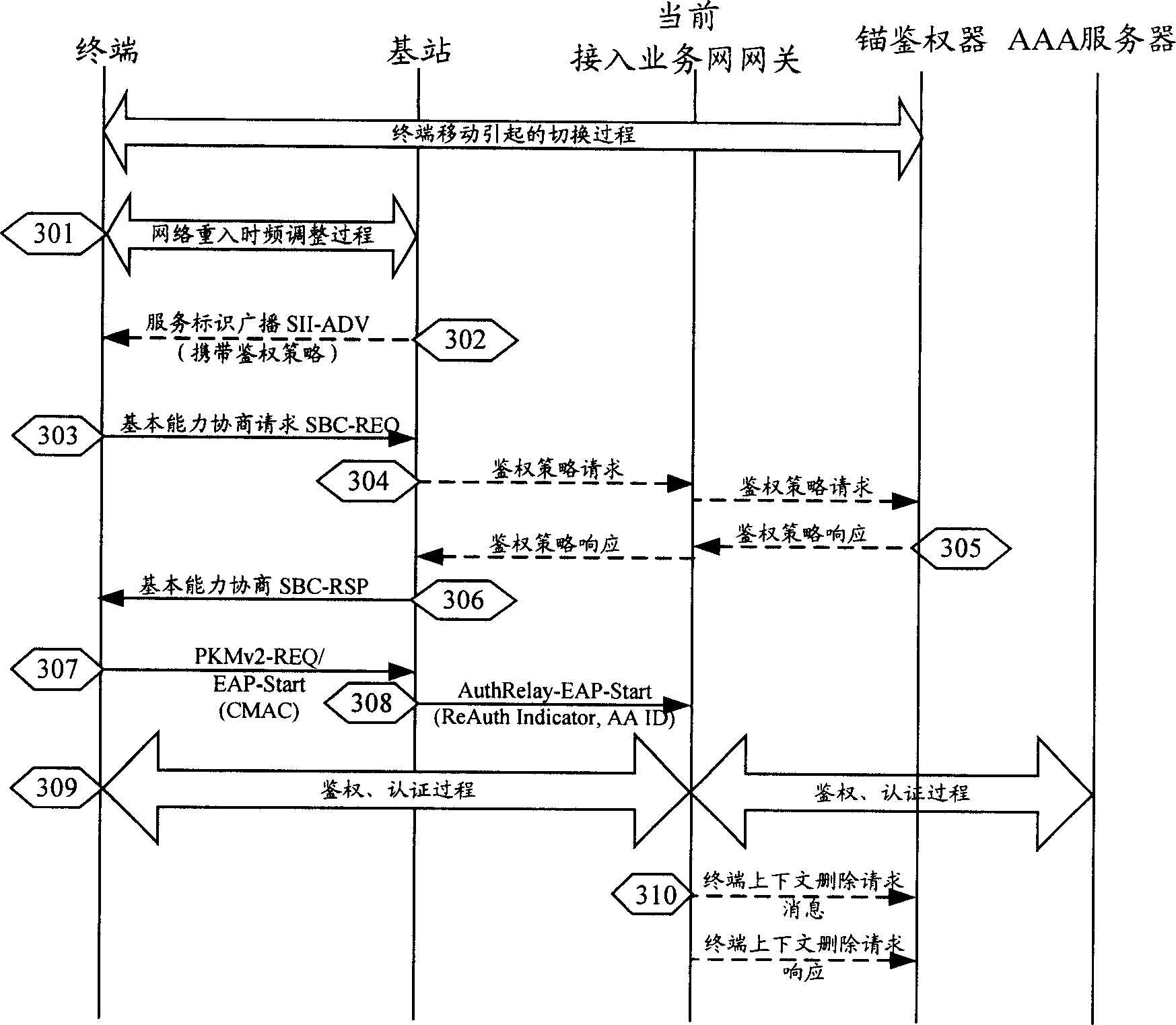
[0124] The authenticator 620 includes an authentication policy acquisition unit 621 . The authenticator 620 is configured to receive an authentication policy request carrying the authentication policy supported by the terminal and the terminal NAI from the base station 610 , and return an authentication poli...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com