Method and system for negotiating and initiating safety context
A contextual and secure technology, applied in transmission systems, digital transmission systems, and key distribution, can solve problems such as key inconsistency, duplicate numbers, and communication interruptions
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0081] The present invention will be described in detail below with reference to the accompanying drawings and in combination with embodiments.
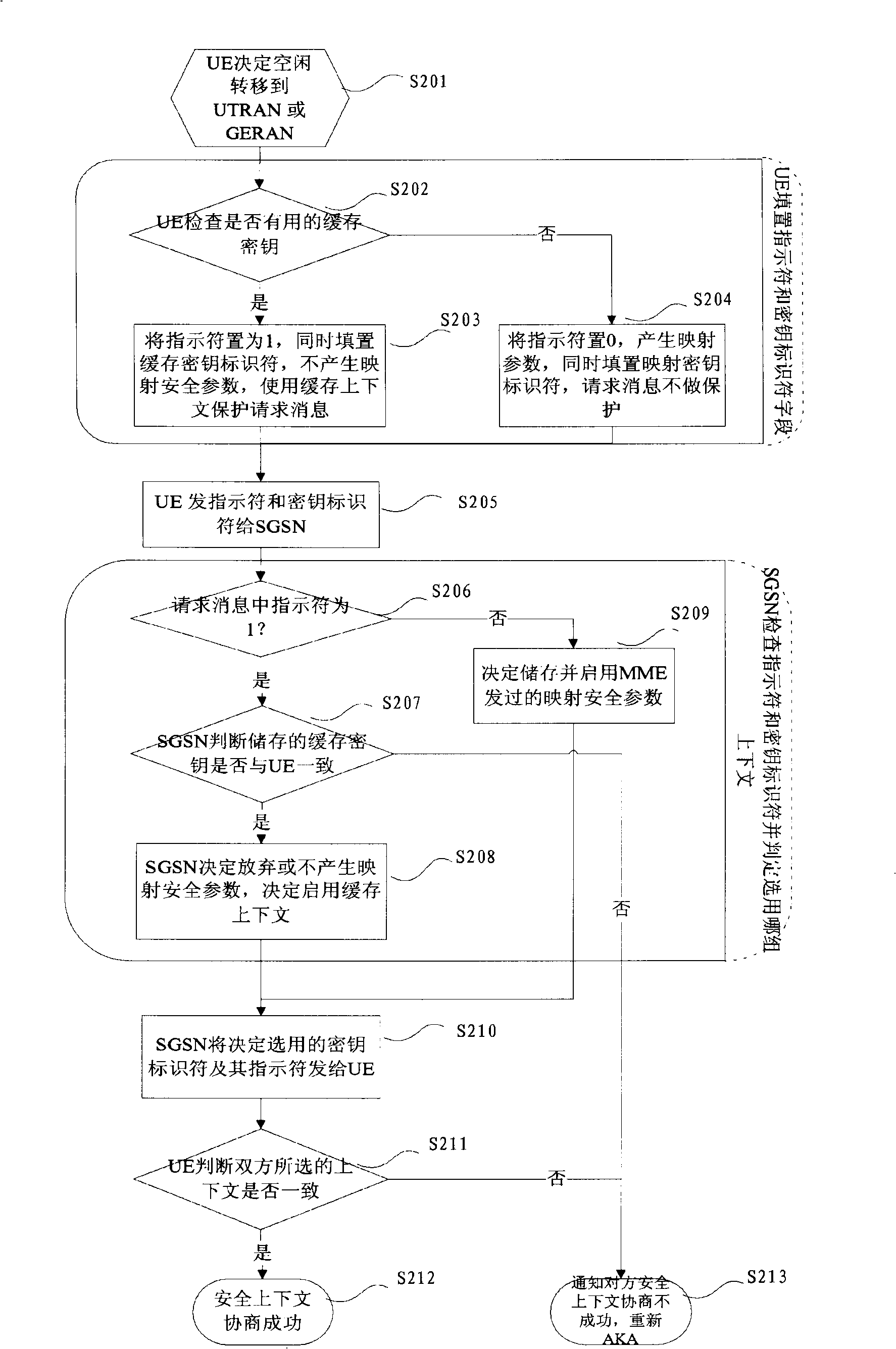
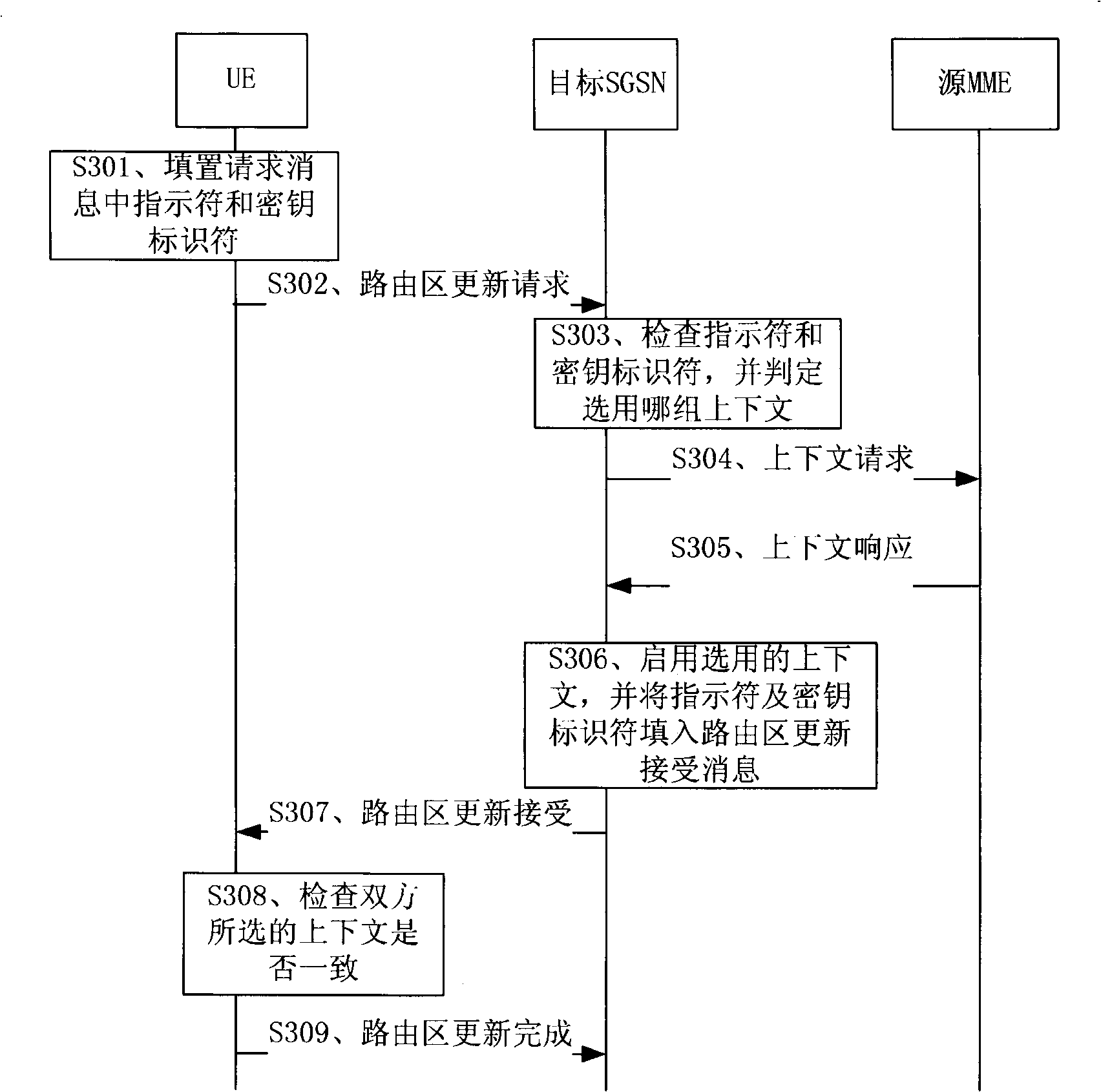
[0082] The main idea of the method for negotiating a security context in the present invention is that when the user equipment sends a routing area update request message or an attach message, the message carries a security context type indicator and a key identifier to indicate the security context type selected by the user equipment, and the SGSN After receiving, judge the security context type selected by the user equipment according to the indicator, and select the security context.
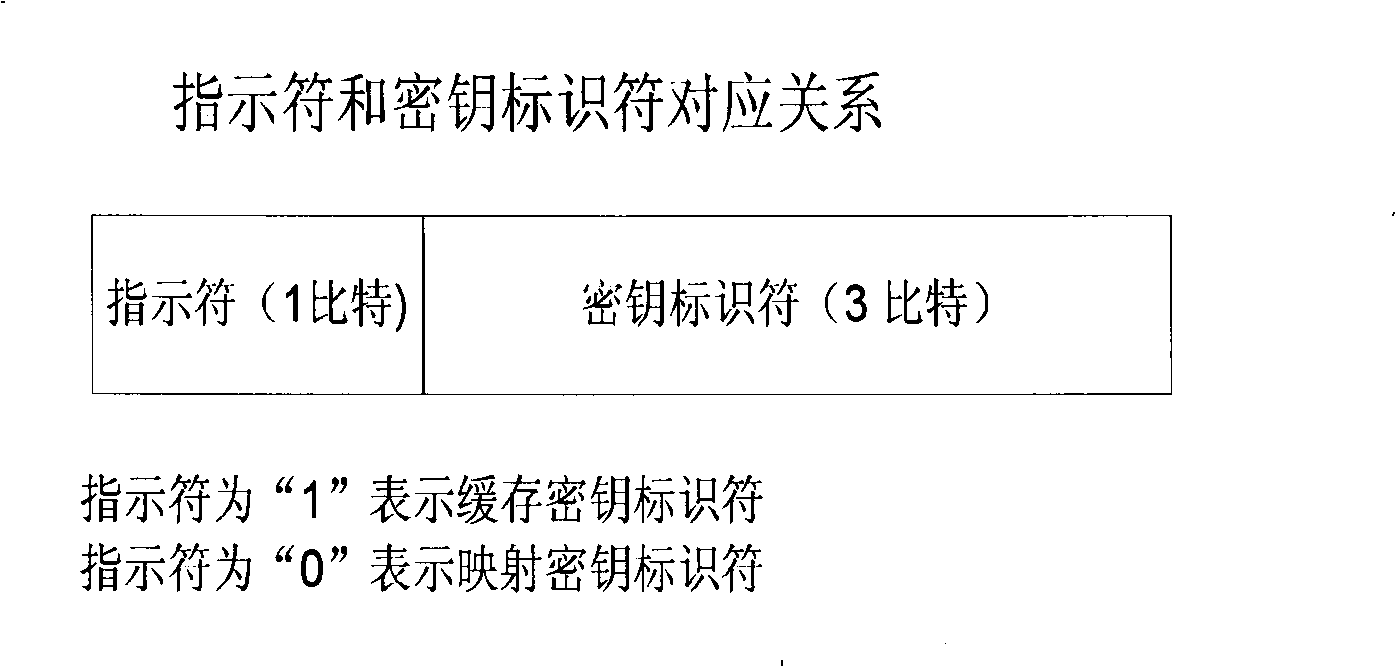
[0083] figure 1 A diagram showing the correspondence between a security context type indicator (Security Context Type Indicator, referred to as an indicator for short) and a key identifier, wherein the indicator field is used to indicate whether the user equipment selects the cache context or the mapping context, that is, the key identifier Wheth...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com