Method and apparatus for preventing malevolence program from accessing network
A technology for accessing the network, malicious programs, applied in the field of preventing malicious programs from creating access to the network through trusted network application objects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0009] Hereinafter, the present invention will be described in detail with reference to the accompanying drawings.
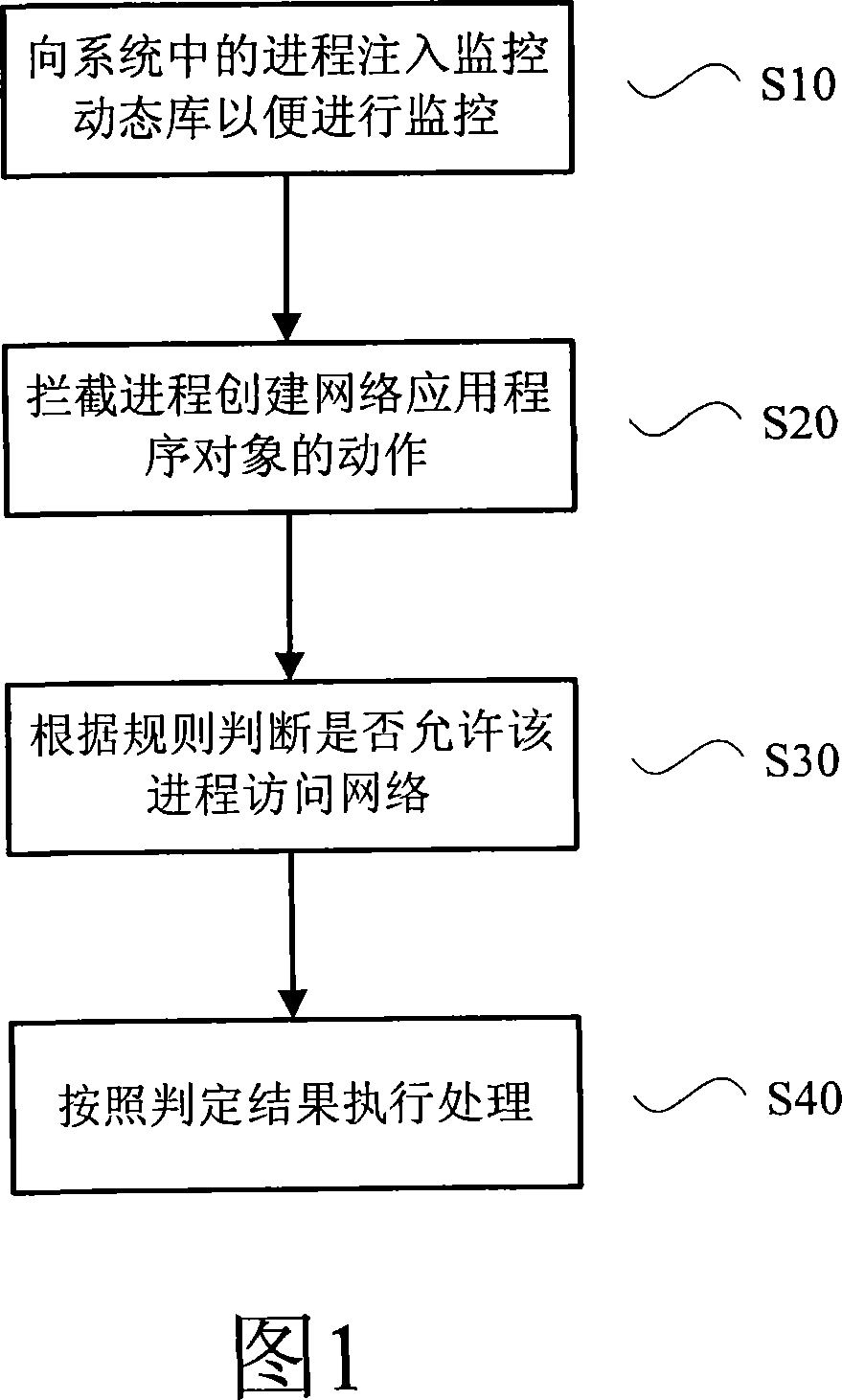
[0010] First refer to figure 1 , illustrating a flowchart of a method for preventing malicious programs from accessing a network according to the present invention, wherein:
[0011] In step S10, the monitoring dynamic library is injected into the processes in the system, so as to monitor the actions of each process in real time. It should be noted that it can be injected into all processes in the system, and can also be selected to be injected into some processes in the system according to specific requirements, which are all within the protection scope of the present invention.
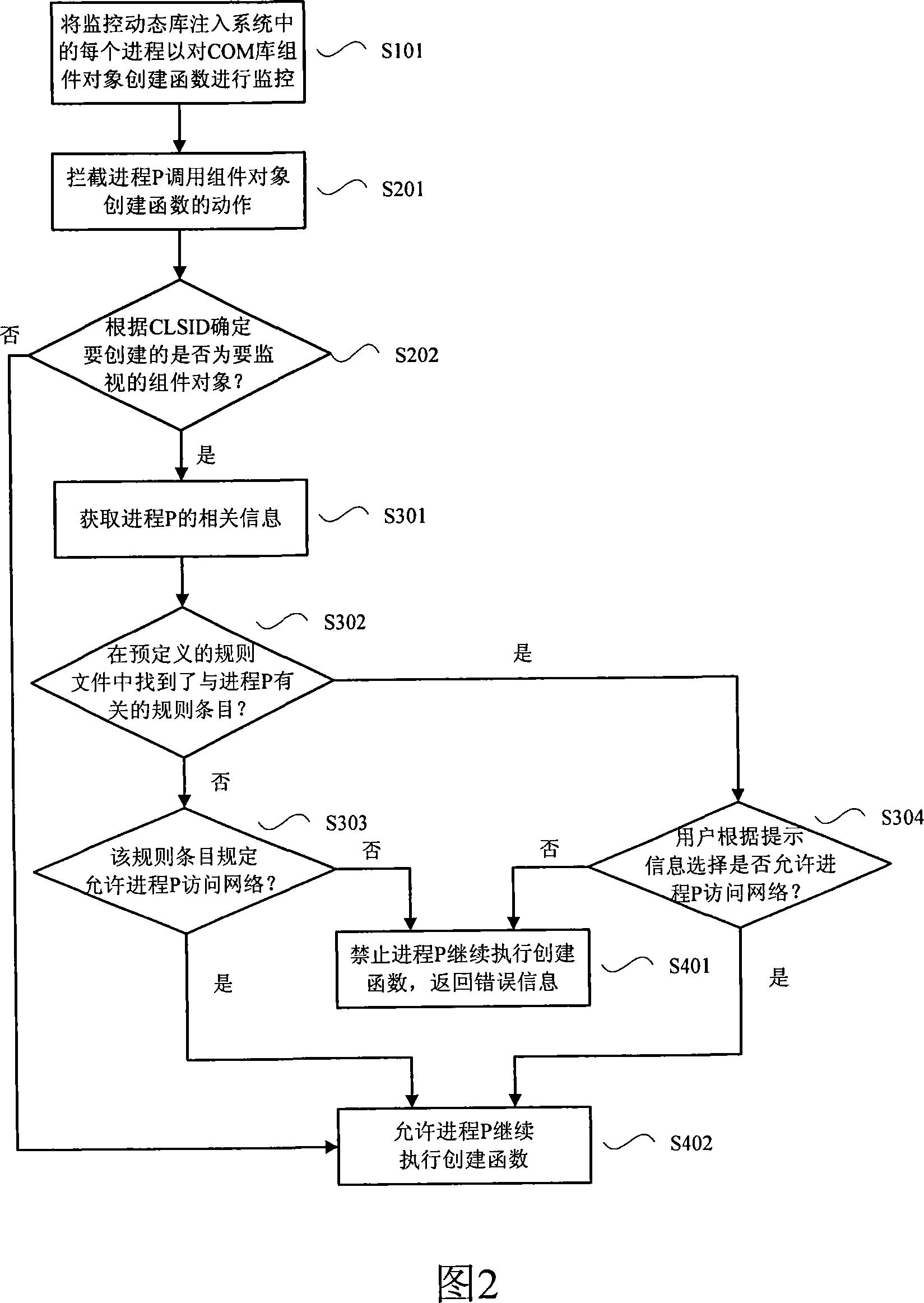
[0012] In step S20, when a certain process is found to create an object of an application program capable of accessing the network, the object creation action is intercepted. What needs special attention here is that the method of the present invention does not intercept the action ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com