Message control method and access equipment in endpoint admission defense
A control method and technology for accessing equipment, applied in the field of data communication, can solve the problem of excessive ACL resource occupation, and achieve the effect of saving ACL resources and increasing access capability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments.
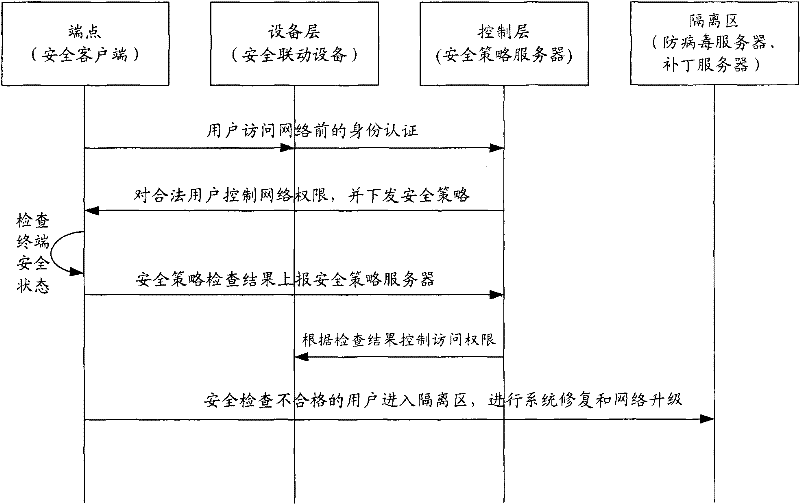
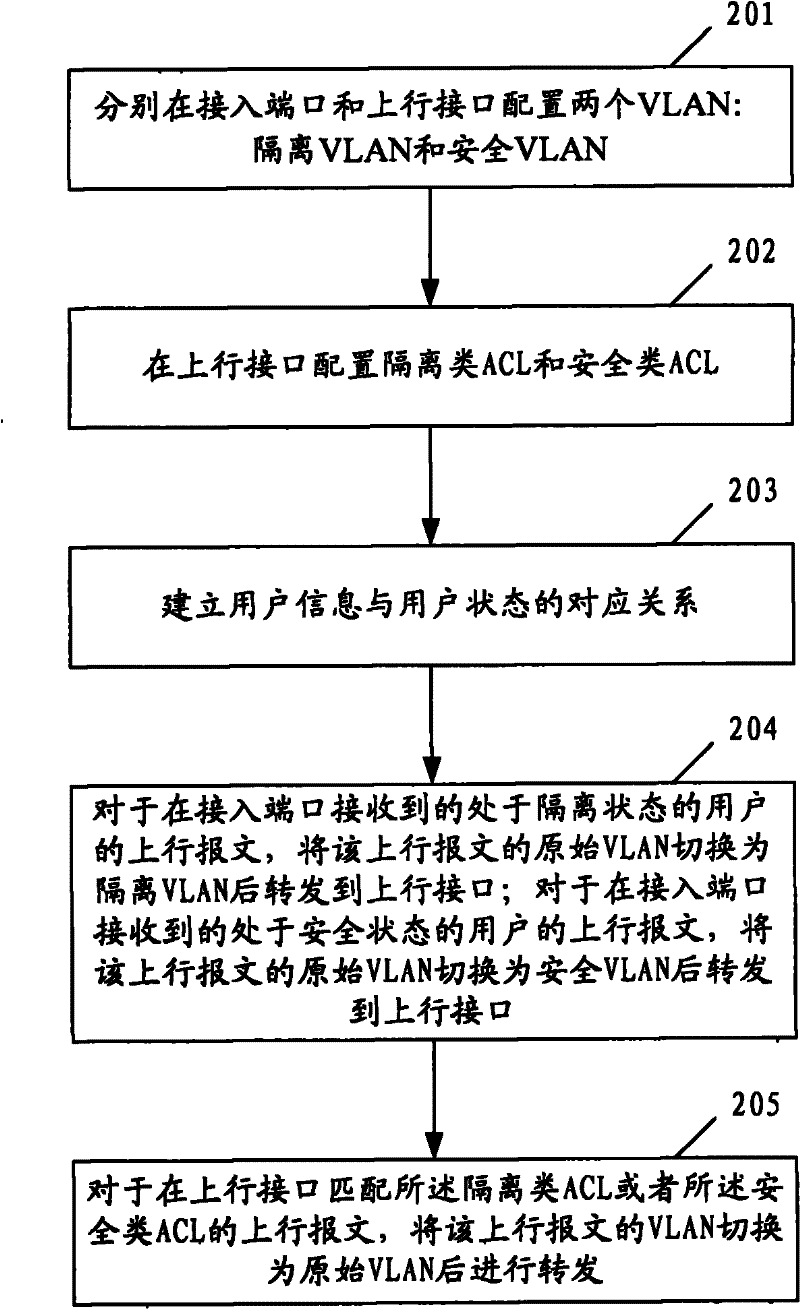
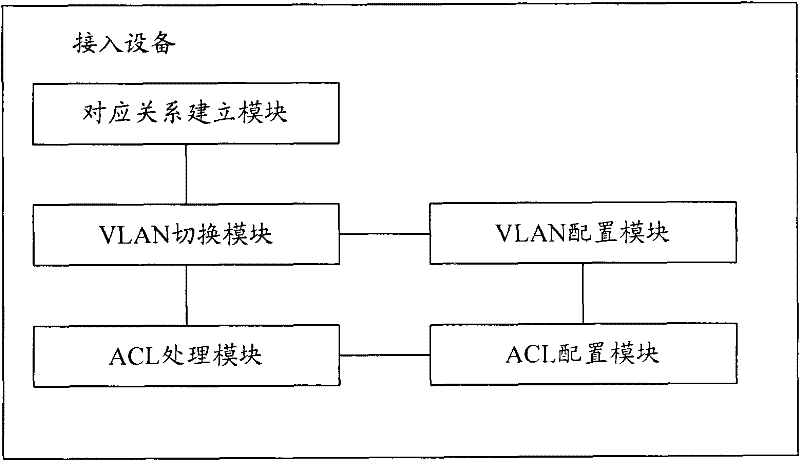
[0041] The key of the present invention is to configure isolation VLAN and security VLAN in the access device, and define isolation area and security area by issuing isolation class ACL or security class ACL for VLAN on the uplink interface; when user message is forwarded, according to The user state switches the VLAN of the packet, and matches the VLAN-based ACL on the uplink interface.
[0042] figure 2It is a flowchart of a message control method in endpoint access defense according to an embodiment of the present invention. The method is applied to an access device (that is, a security linkage device) in an EAD, and includes the following steps:
[0043] Step 201: configure two virtual local area networks (VLANs) on the access port and the upl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com