Method and device for transmitting data based on VLL (Virtual Lease Line)
A data transmission method and decapsulation technology, applied in the direction of digital transmission system, transmission system, data exchange network, etc., can solve the problems of inability to meet requirements, rapid increase, and high price
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0041] This embodiment describes the implementation of supporting multiple ACs at the local end and multiple ACs at the remote end to access the same ALL instance. In this embodiment, a VLL public network connection supports interconnection between multiple local ACs and multiple peer ACs, and the number of local ACs is the same as the number of peer ACs. One local AC is bound to one peer AC to form a fixed Point-to-point connection, while there is only one public PW on the public network side. This kind of networking is like directly aggregating multiple ordinary VLL connections on the public network side.
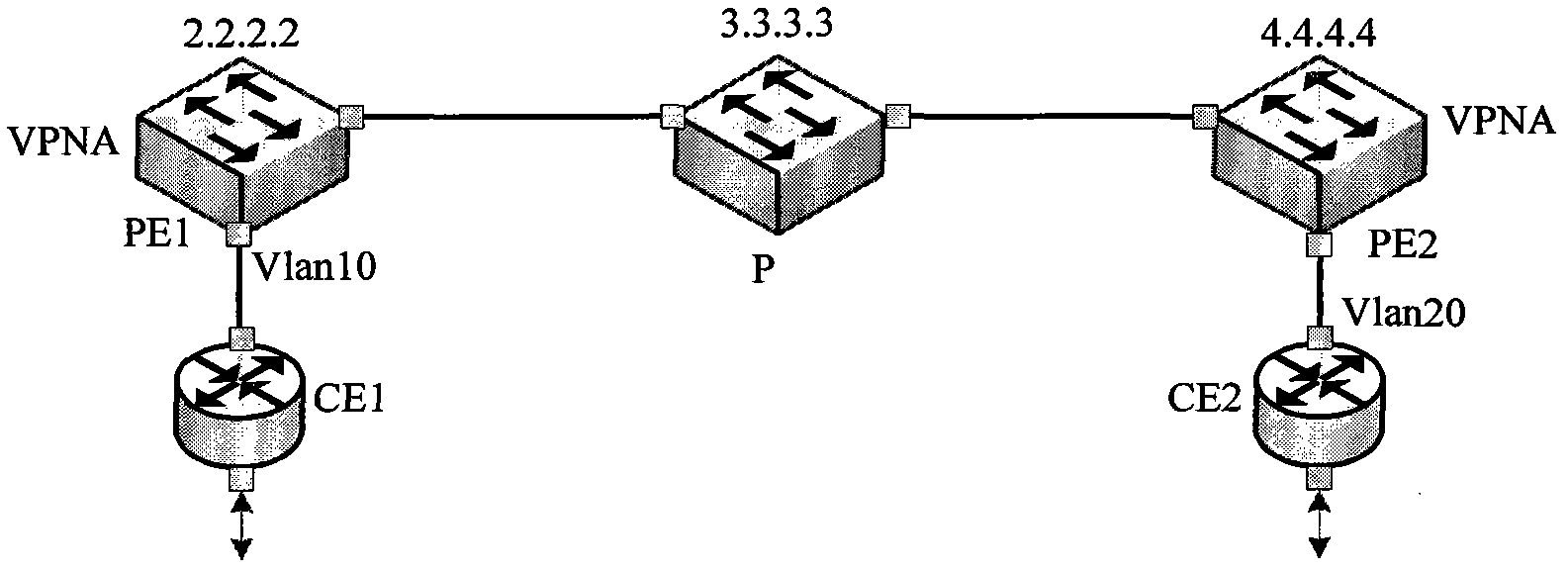
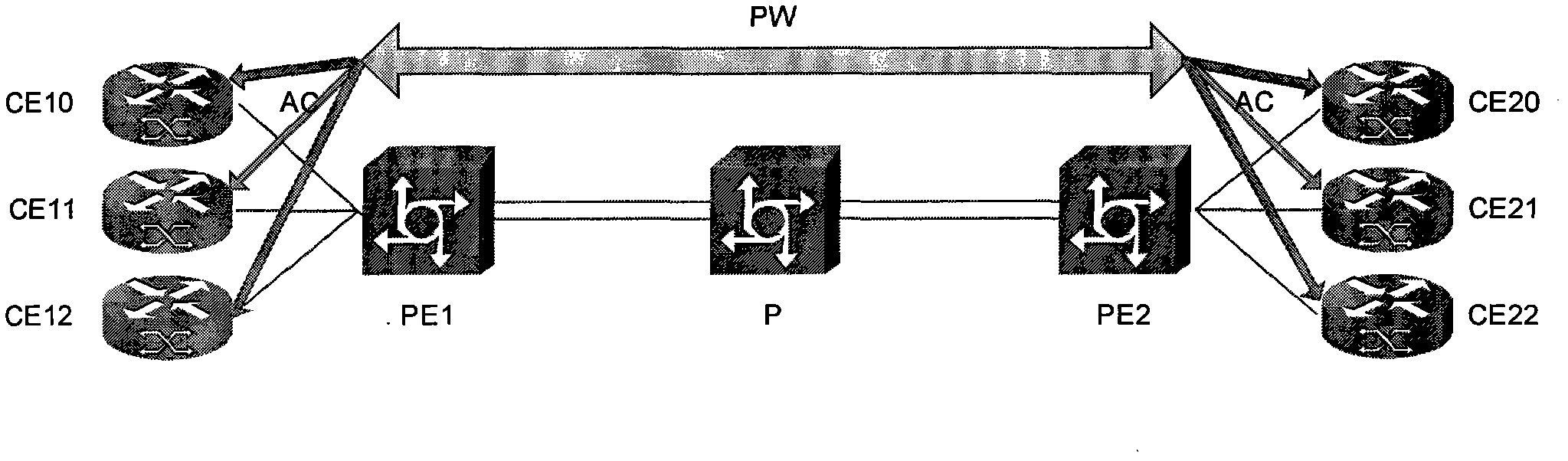
[0042] The networking architecture of this embodiment can be as follows figure 2 shown. A VLL PW connection is established between PE1 and PE2. Three user access devices CE10, CE11, and CE12 are connected to PE1, and there are three corresponding ACs: AC10, AC11, and AC12. Three user access devices are connected to PE2. CE20, CE21, and CE22, and correspondingly there a...
Embodiment 2
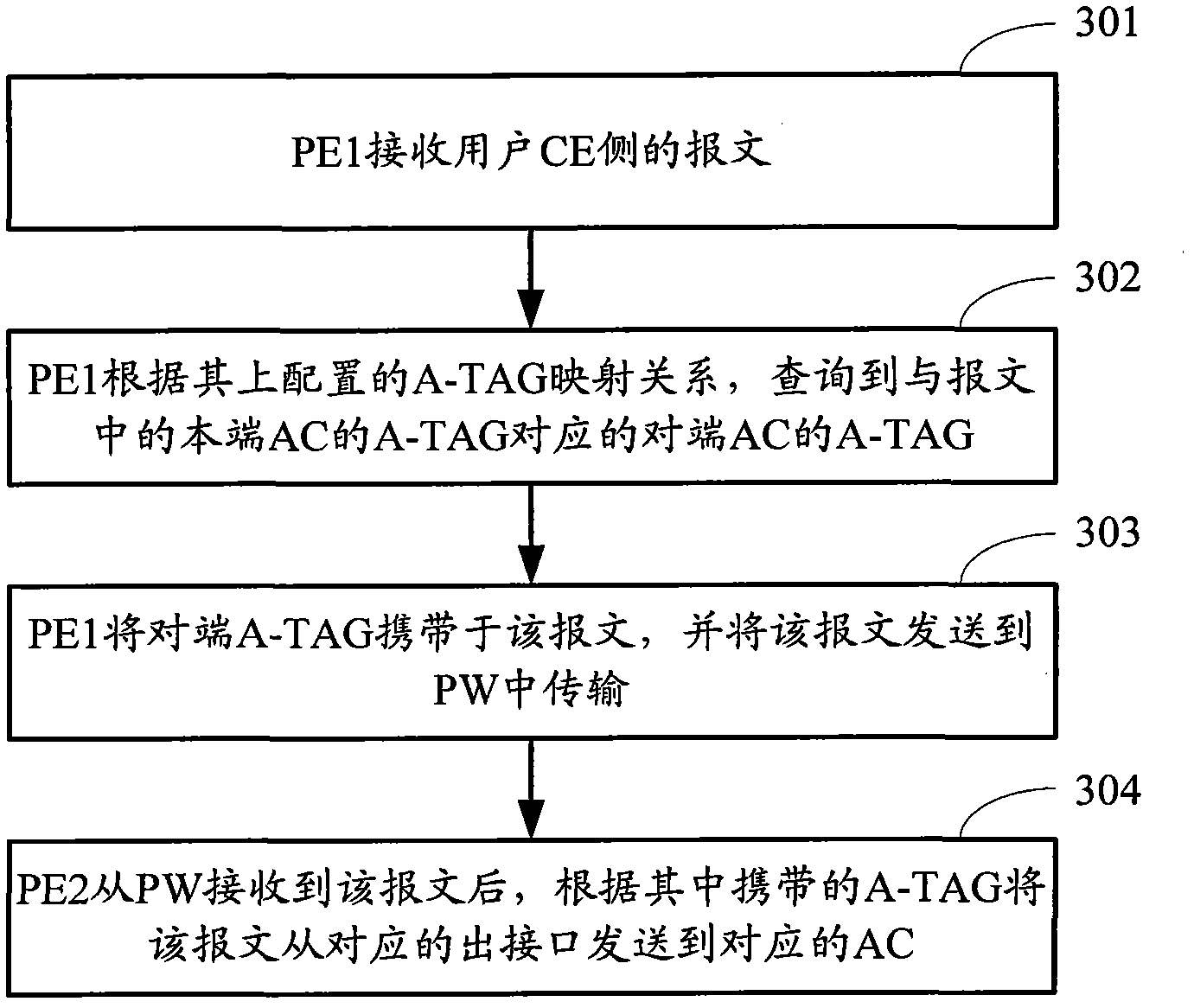
[0063] Embodiment 2 is obtained by improving Embodiment 1, aiming at figure 2 As shown in the network architecture, that is, when the number of ACs on the AC side of the PE equipment at both ends of the PW is equal, the corresponding A-TAG can be assigned to each connection from the local AC to the peer AC, so that the The A-TAG mapping relationship table is configured on the PE device. For example, for figure 2 In the shown network architecture, A-TAG_0 may be allocated for the connection between AC10 and AC20, A-TAG_1 may be allocated for the connection between AC11 and AC21, and A-TAG_2 may be allocated for the connection between AC12 and AC22. Take the case where user CE10 sends packets from AC10 to PE1. The packet transmission process mainly includes:
[0064]When a packet from the user CE10 side (the packet carries an A-TAG, and the A-TAG is A-TAG_0) enters PE1, PE1 performs necessary encapsulation processing on the packet and sends the packet to the PW, where , the...
Embodiment 3
[0067] This embodiment describes an implementation manner in which one AC at the local end and multiple ACs at the opposite end access the same VLL instance. In this embodiment, the PE device with multiple ACs sends and receives packets similarly to Embodiment 1, but on the PE device with one AC, multiple A-TAGs need to be bound to the same AC. Similarly, in order to provide more flexible access, it is necessary to establish a mapping table between LOCALA-TAG and Remote A-TAG on the AC side of each PE device, so that the PE device at the sending end of the packet can determine which address to send the packet to at the peer end through the mapping table. An AC, or the PE device at the message receiving end decides which local AC to send the message received from the peer end through the mapping table.
[0068] The networking architecture of this embodiment can be as follows Figure 4 shown. Take PE2 as an example for description. PE1 and PE2 are PE devices at both ends of t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com