Terminal information security method and device
A technology of terminal information and confidentiality method, which is applied in the field of mobile communication and can solve the problems of unfavorable protection of user's personal privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
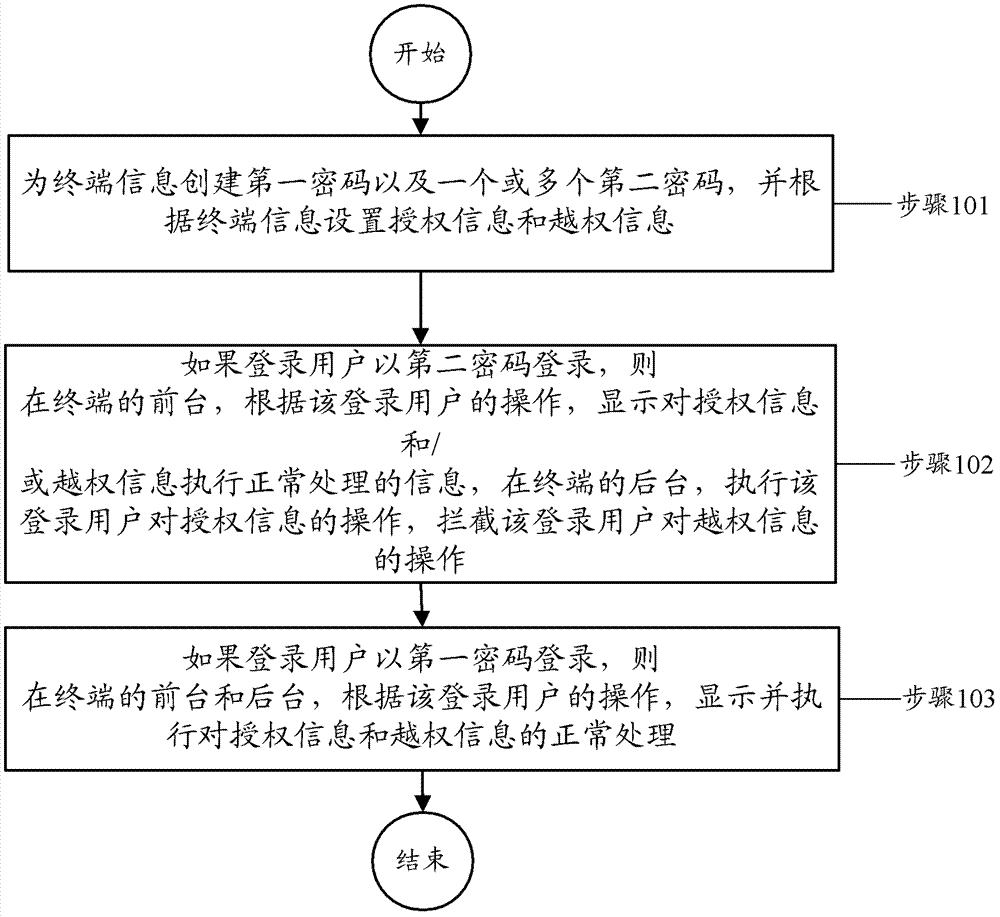
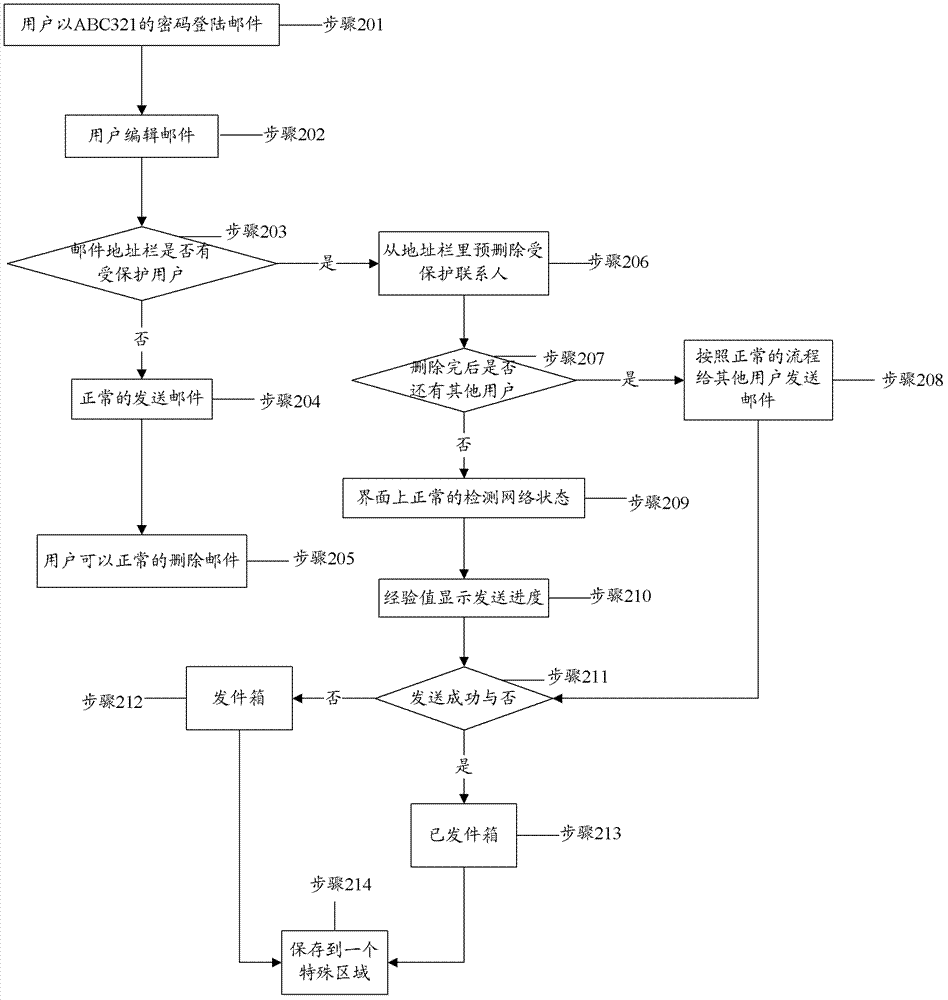
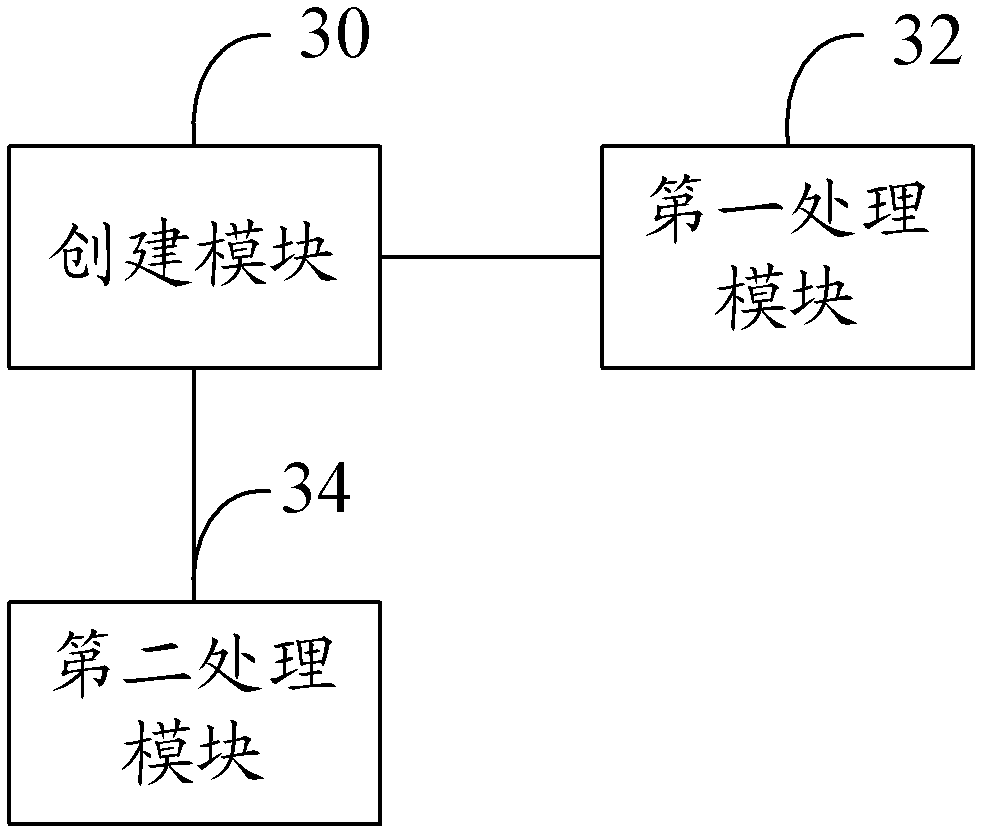
[0021] In order to solve the problem of using a separate area to store secret information in the prior art so that others can easily know that the mobile phone has stored secret information, which is not conducive to protecting the privacy of the user, the present invention provides a terminal information security method and device. The present invention implements The technical solution of the example proposes the concept of password authority, that is to say, by distinguishing whether the password entered by the user is a super password or a restricted password, different interfaces and information under corresponding authority and corresponding information messages are displayed respectively. The technical solution of the embodiment of the present invention also proposes a method for processing unauthorized information by a restricted login person under restricted password login. The present invention will be described in further detail below in conjunction with the accompan...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com