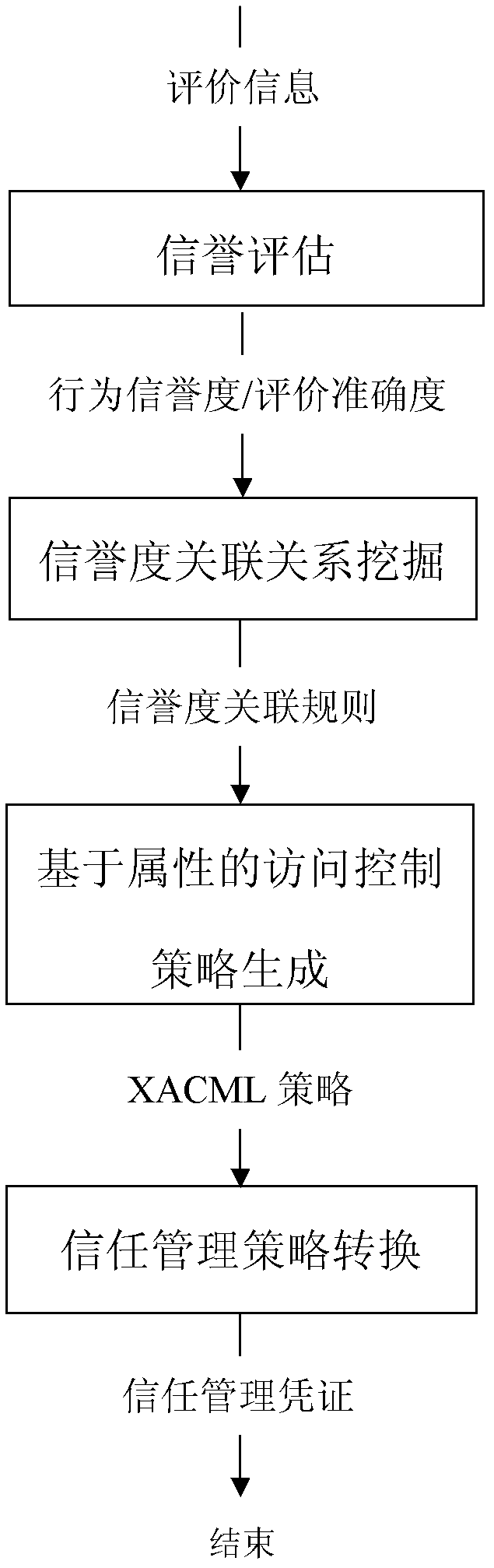
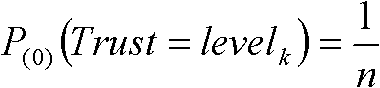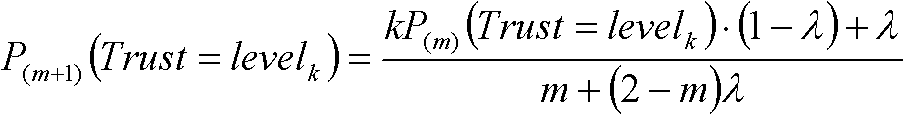Method for generating cross-domain access control strategy by rising from credit assessment to trust management
An access control policy and trust management technology, applied in the field of cross-domain access control policy generation, can solve the problem that it is difficult to dynamically formulate finer-grained policies, and achieve the effect of convenient and seamless integration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The embodiments of the present invention are described in detail below in conjunction with the accompanying drawings: the present embodiment is implemented on the premise of the technical solution of the present invention, and detailed implementation methods and specific operating procedures are provided, but the protection scope of the present invention is not limited to Examples described below.
[0033] This embodiment includes the following steps:
[0034] Step 1: Establish and implement an uncertain reputation evaluation model. For the randomness and ambiguity of reputation, this embodiment combines the cloud model proposed by Li Deyi et al. and Bayesian network for representation and evaluation of reputation.
[0035] Reputation T is a quantitative concept on domain space U=[0, n] (n is any positive integer), represented by reputation cloud T(Ex, En, He), where Ex is expected value, En is entropy, He is the super-entropy. A rating r ∈ U from other entit...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com