Computer managing method and system
A management method and management system technology, applied in the direction of digital data authentication, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
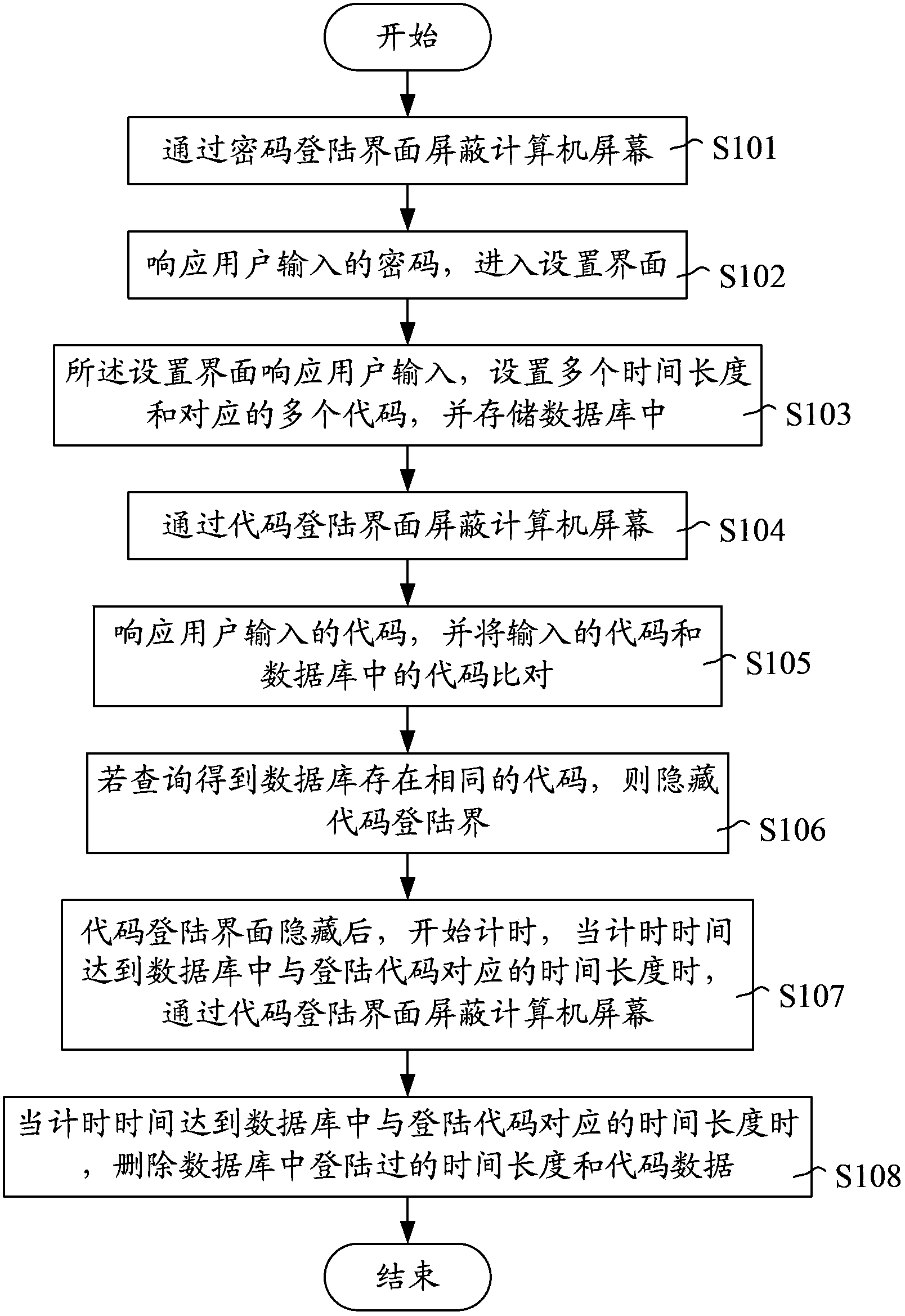
[0025] Such as figure 1 As shown, it is a flow chart of the steps of the computer management method of an embodiment, including the following steps:
[0026] Step S101, shielding the computer screen through the password login interface.
[0027] Step S102, responding to the password input by the user, and entering the setting interface.
[0028] In actual use, the parents only have the login password.
[0029] Step S103, the setting interface responds to user input, sets multiple time lengths and corresponding multiple codes, and stores them in the database.
[0030] For example, if the duration is 1 hour, the corresponding code is 123456; if the duration is 2 hours, the password is 24680; if the duration is 3 hours, the corresponding code is 13579. Parents can judge how long the child should be allowed to play according to the current situation, and then tell the corresponding code. For example, during the weekend, the time is allowed to be longer, and the code correspond...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com