An identity-based wireless sensor network key management method
A wireless sensor and network key technology, applied in the field of identity-based wireless sensor network key management, can solve difficult problems and achieve the effect of improving security and saving storage space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The technical solution of the present invention will be described in detail below with reference to the accompanying drawings.
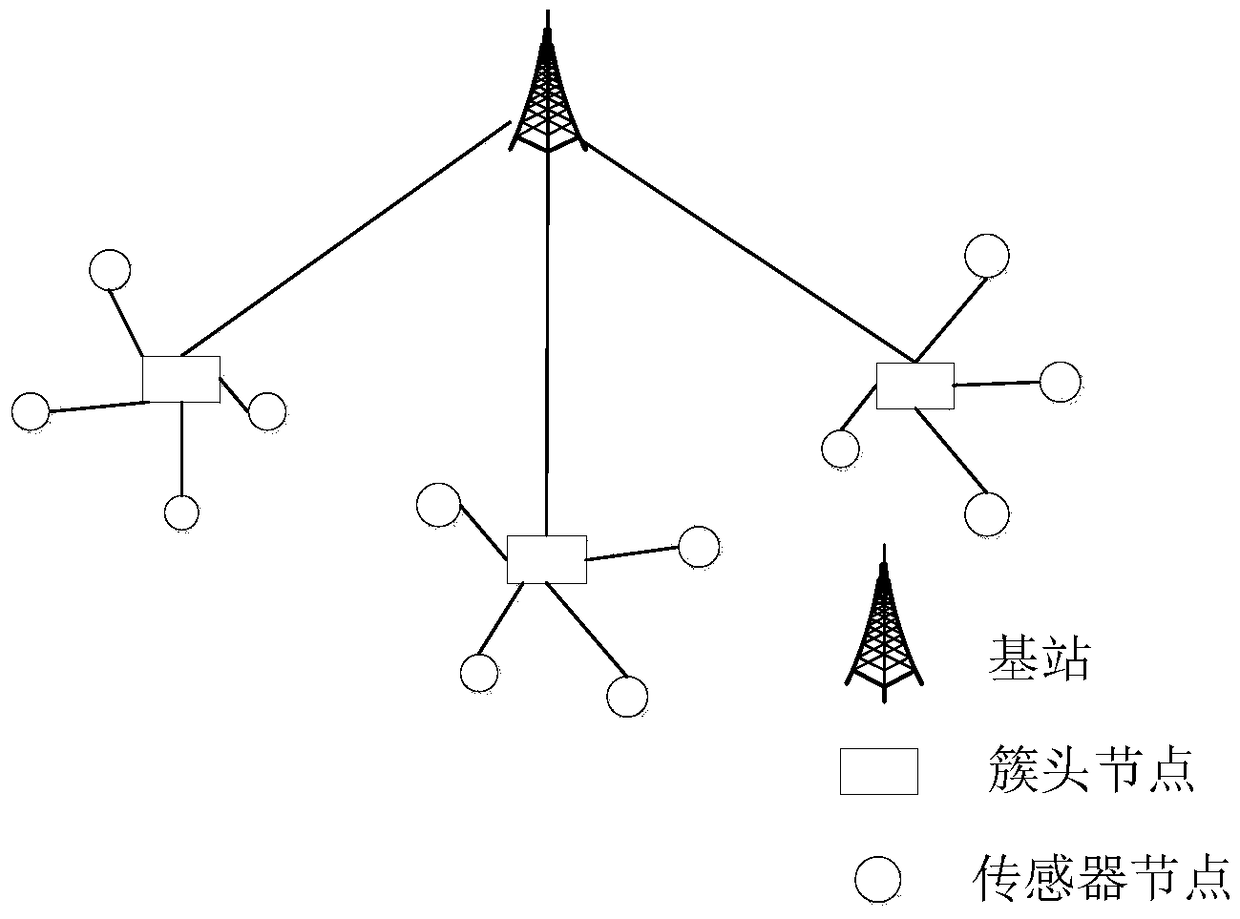
[0049] Such as figure 1 As shown, the present invention is based on a hierarchical wireless sensor network. The wireless sensor network includes a base station, a cluster head node, and a sensor node. A base station is connected to several cluster head nodes, and each cluster head node is connected to several sensor nodes. Among them, the sensor node monitors the area where it is located, uploads the collected information, and the cluster head node collects the data to the base station. The base station is the data aggregation center and the management center of the whole network, which can communicate with the outside world and is safe by default. Cluster head nodes have stronger computing and storage capabilities than sensor nodes.
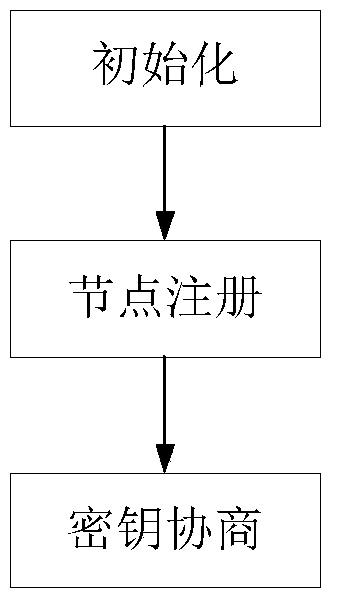
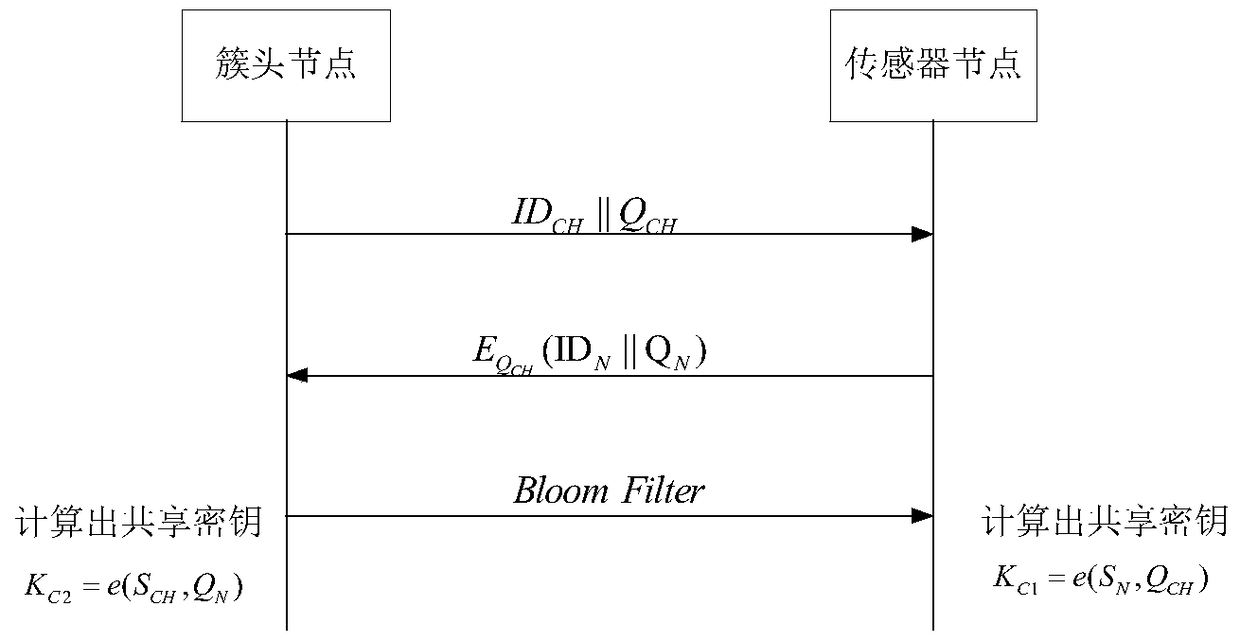
[0050] Such as figure 2 As shown, the present invention specifically includes three steps: the network pa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com