System for intercepting access request, method, apparatus and server
An access request and server technology, applied in the Internet field, can solve problems such as inability to bypass blocking, interception effect monitoring, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
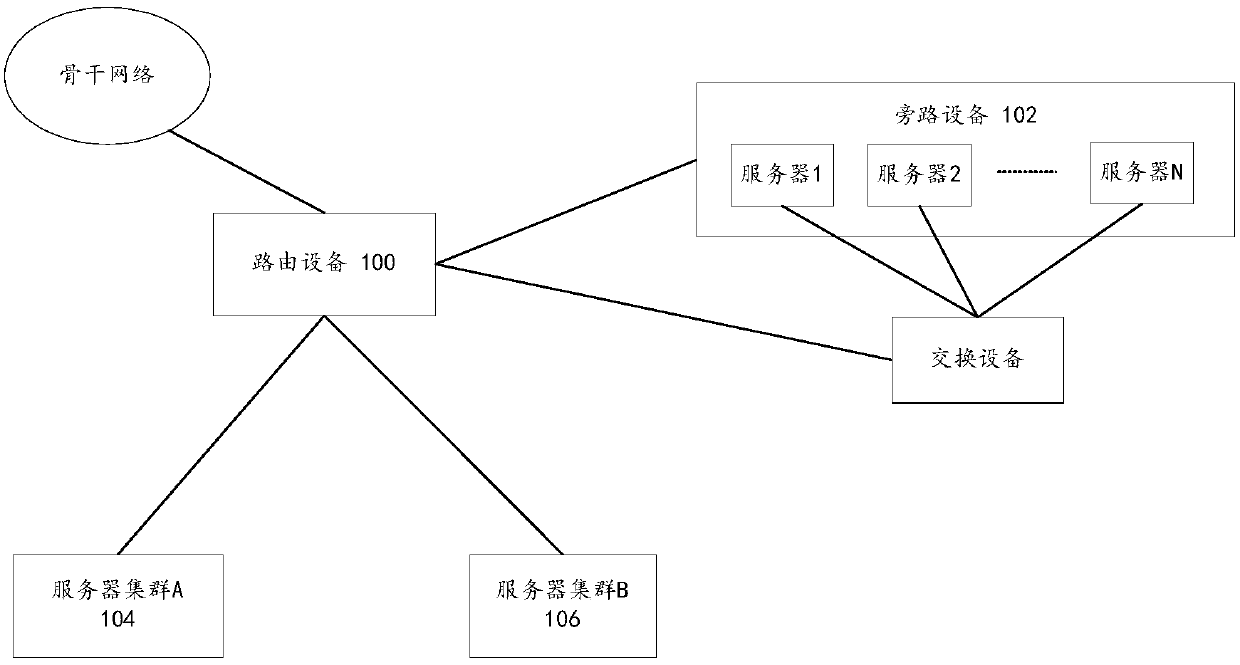
[0063] According to an embodiment of the present application, an embodiment of a system for blocking an access request is provided. figure 1 is a schematic structural diagram of a system for blocking access requests according to an embodiment of the present application. Such as figure 1 As shown, the system can include:
[0064] The routing device 100 is configured to receive an access request from the sender and forward the access request to the receiver; the sender may be a client or server located in a different area or region from the receiver, and send the access request via the backbone network. The above receiving end is server cluster A 104 and / or server cluster B 106 .
[0065] The bypass device 102 is used to mirror the access request to obtain the mirror request; when the mirror request matches the preset blocking rule, send a fake reset request to the receiving end, and monitor whether the receiving end returns the same access request to the sending end. A corre...
Embodiment 2
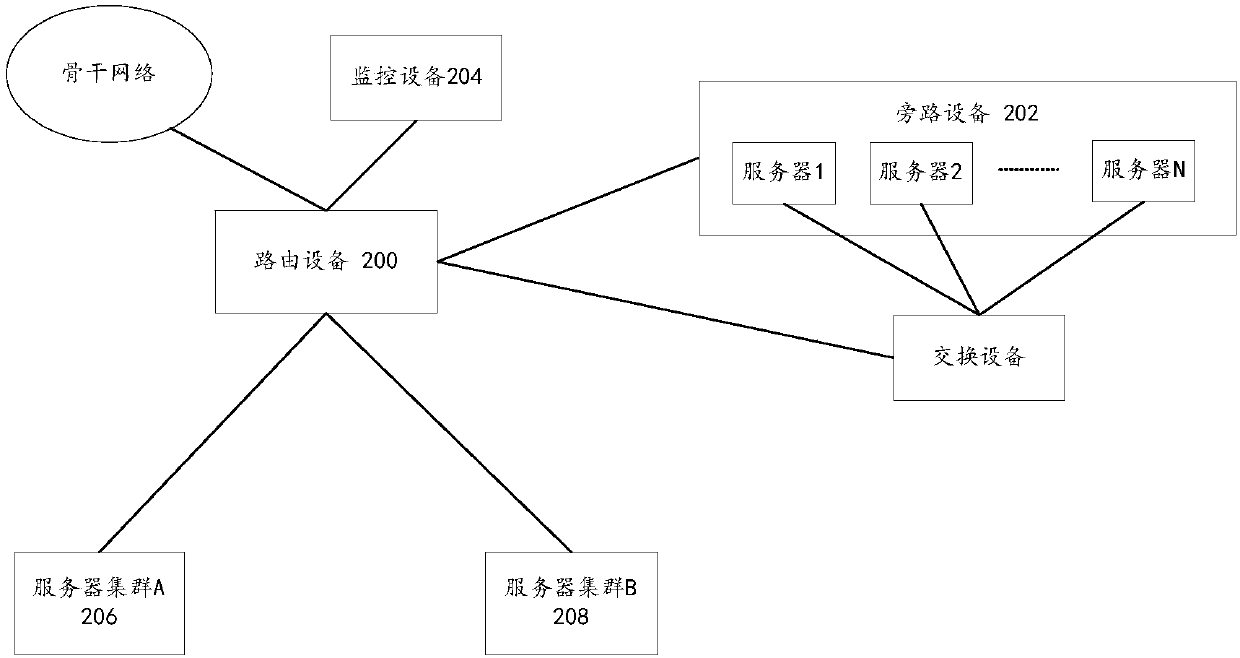
[0144] According to an embodiment of the present application, an embodiment of an apparatus for implementing the above-mentioned blocking access request is also provided, Figure 8 is a structural block diagram of an apparatus for blocking access requests according to an embodiment of the present application. Such as Figure 8 As shown, the device includes: an acquisition module 10, configured to acquire a mirroring request, wherein the mirroring request is a mirroring result of an access request sent from a sending end to a receiving end; a first determining module 20, configured to determine that the mirroring request matches a preset Blocking rules; the execution module 30 is used to send a fake reset request to the receiving end to block the access request, wherein the fake reset request is used to trigger the receiving end to close the network connection between the sending end and the receiving end; the monitoring module 40 , used to monitor whether the receiving end re...
Embodiment 3
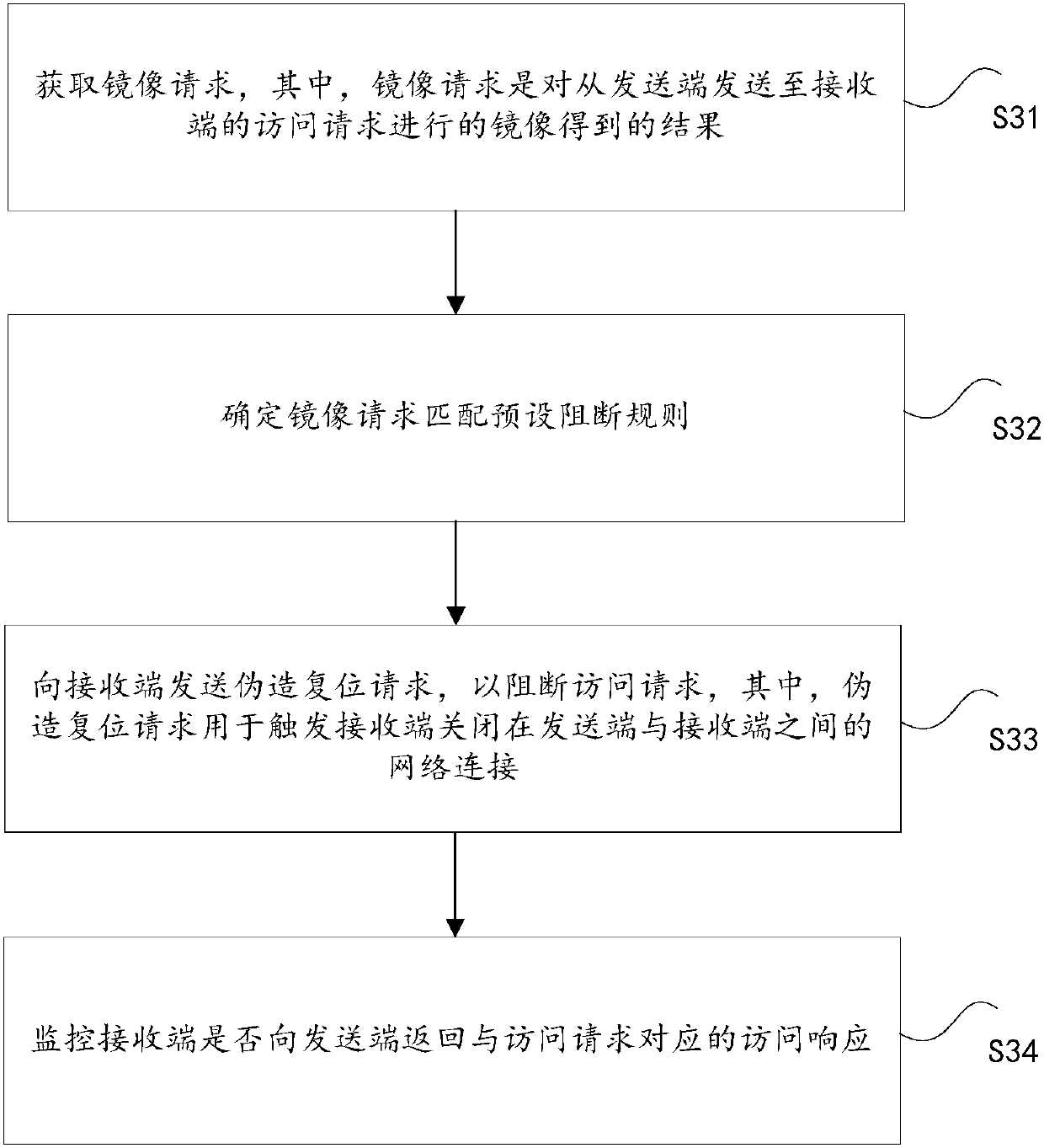
[0158] According to an embodiment of the present application, a server is also provided. The server is used to send a forged reset request to the receiving end when the obtained mirroring request matches the preset blocking rule, and monitor whether the receiving end returns an access response corresponding to the access request to the sending end, wherein the mirroring request is Obtained by mirroring the access request sent from the sender to the receiver, the fake reset request is used to trigger the receiver to close the network connection between the sender and the receiver.
[0159] Optionally, the server is also used to determine that the access request is successfully intercepted if the receiving end is not monitored to return an access response to the sending end after the receiving end's response time to the access request is reached; if it is monitored that the receiving end returns an access response to the sending end response, it is determined that the access req...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com