Secondary jpeg compressed image forensics method based on deep multi-scale network
A technology of compressing images and deep neural networks, which is applied in the field of tampering detection of secondary JPEG compressed images, and can solve the problems of low image forensics accuracy, insufficient consideration, and no solutions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
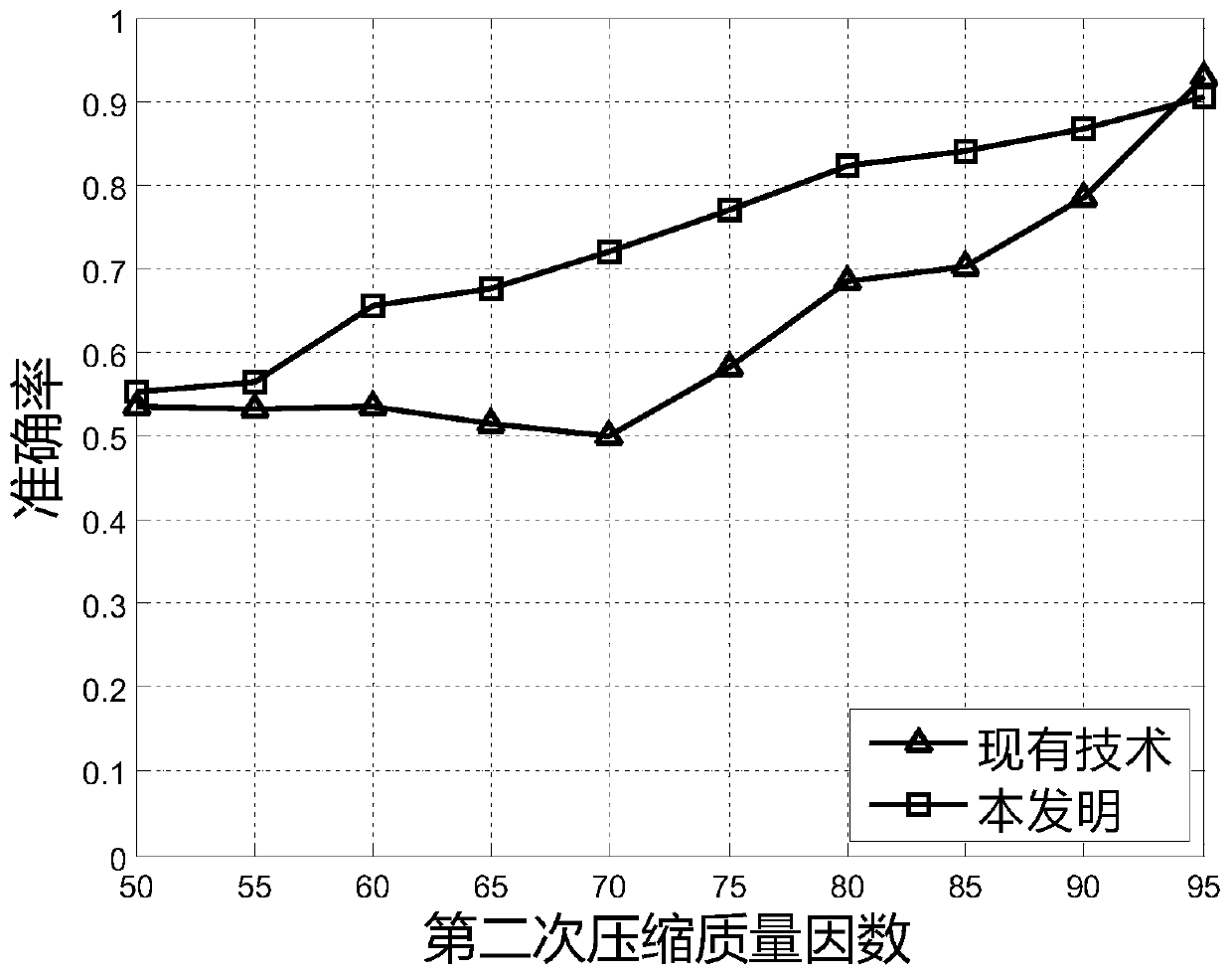
Method used
Image
Examples
Embodiment Construction
[0039] The present invention will be described in further detail below in conjunction with the accompanying drawings and specific embodiments.
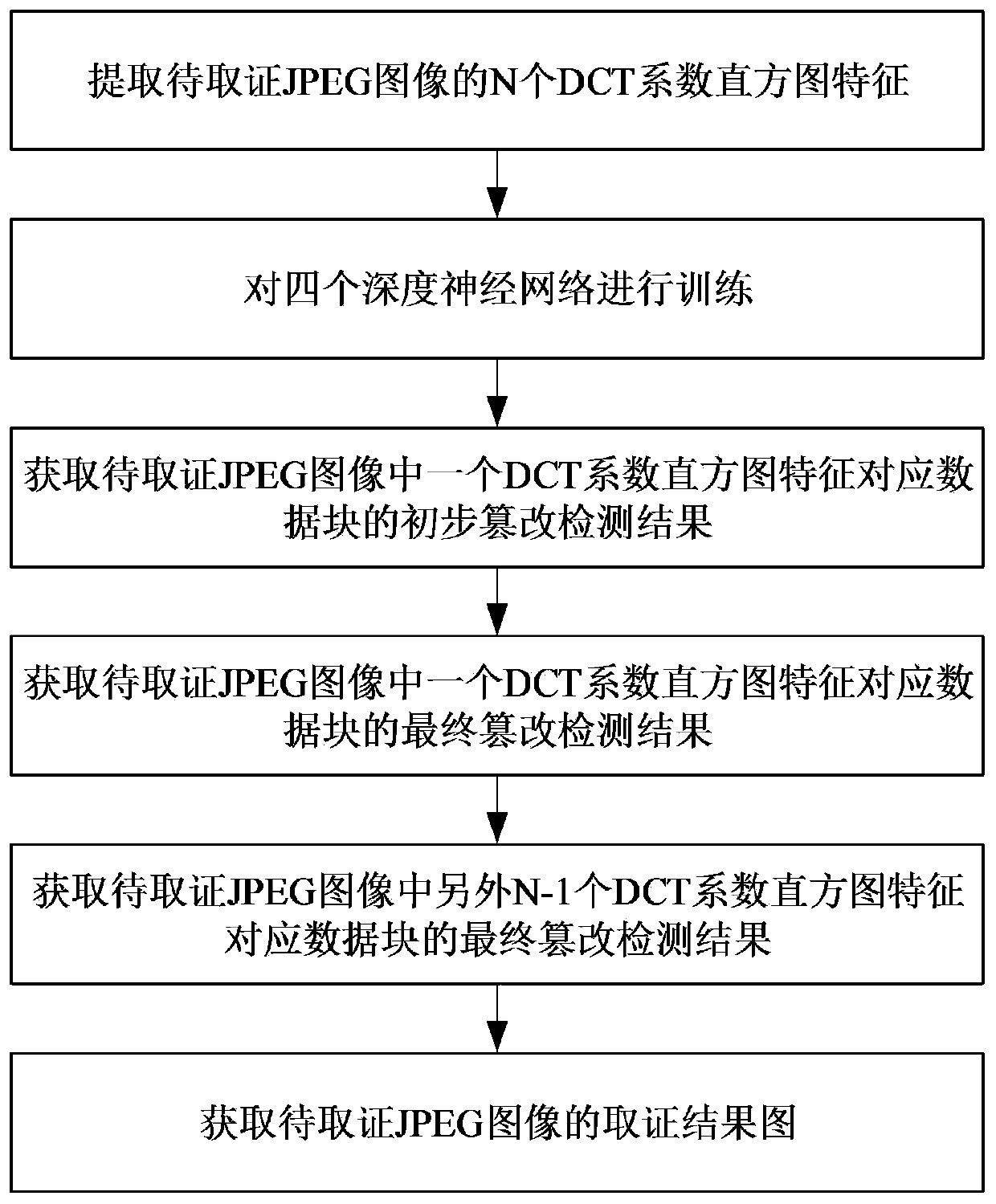
[0040] refer to figure 1 , a second JPEG compressed image forensics method based on a deep multi-scale network, including the following steps:
[0041] Step 1) Extract the N DCT coefficient histogram features F of the JPEG image to be forensic:
[0042] Step 1a) Use the JPEG image toolkit to read in a 1024×1024 JPEG image to be forensic, obtain the image data and image header file of the image to be forensic, and extract the DCT coefficients from the image header file to obtain a size of m× n=1024×1024 DCT coefficient matrix;
[0043] Step 1b) check whether the number of rows and the number of columns of the DCT coefficient matrix can be divisible by L=64, if so, perform step (1c), otherwise, fill zeros on the rightmost side of the DCT coefficient matrix column, zero-padded at the bottom OK, and carry out step (1c), because m=10...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com