A secondary authentication method suitable for voice command responses of smart devices
A voice command, smart device technology, applied in speech analysis, voice recognition, home automation network and other directions, can solve the problem that smart devices do not have authority identification, are insecure, cannot recognize unauthorized instructions, etc., and achieve smooth human-computer interaction. The effect of secondary authentication method, high security, and low power consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Embodiments of the present invention will be described below in conjunction with the accompanying drawings.
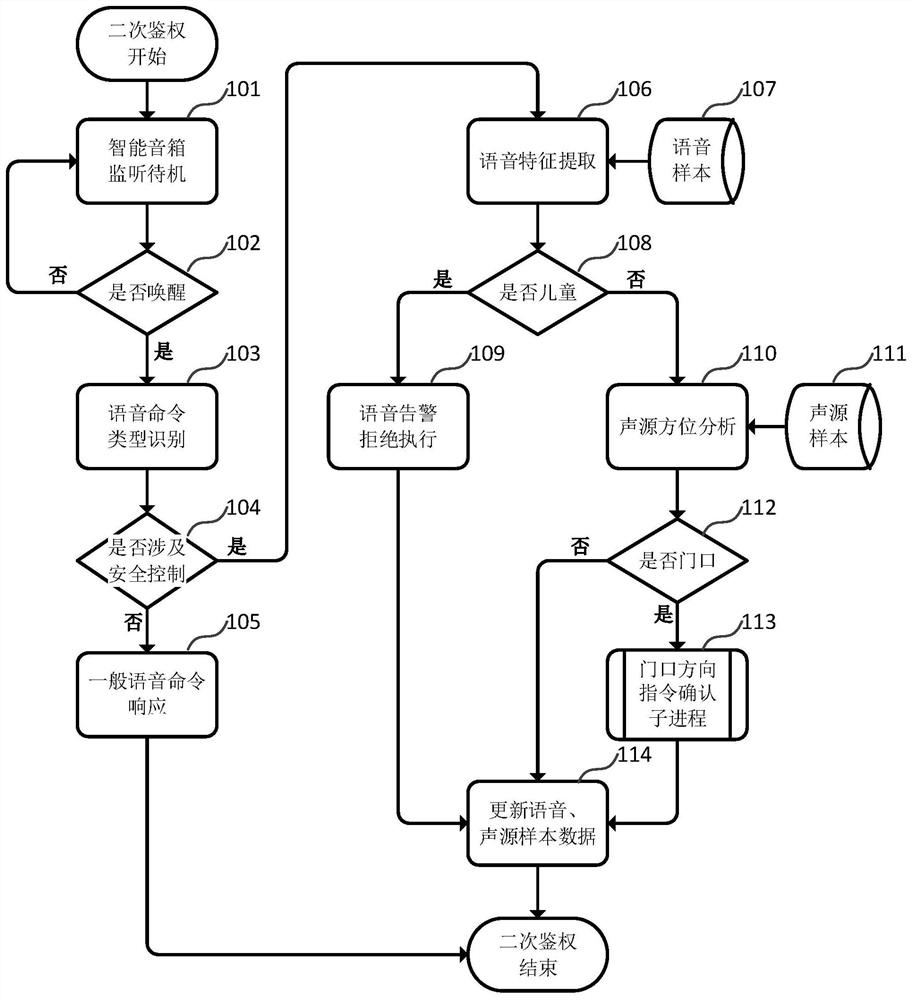
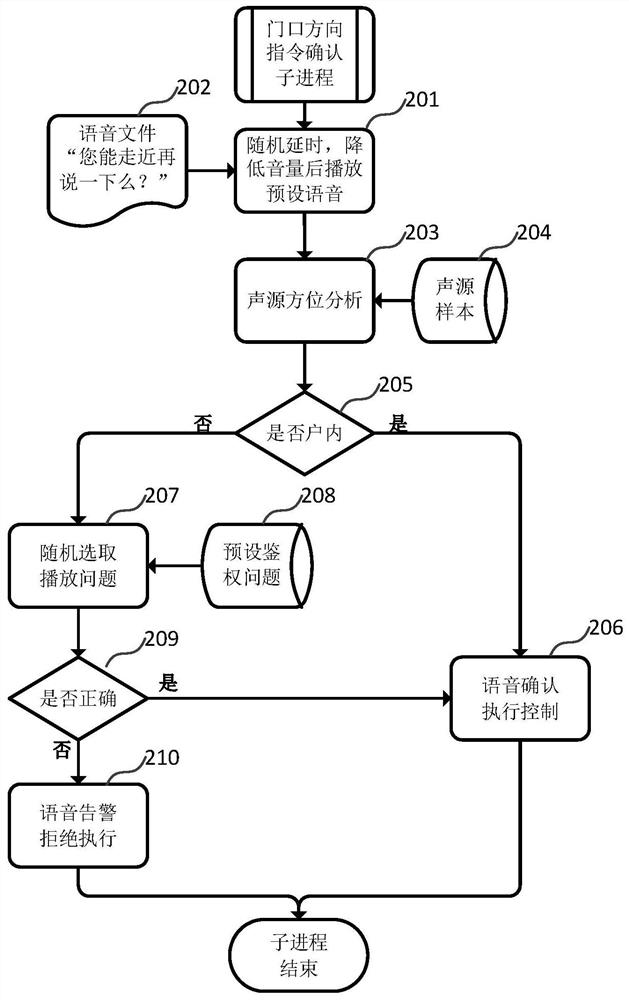
[0033] like figure 1 As shown, the present invention designs a secondary authentication method suitable for voice command responses of smart devices. In the method, the smart device recognizes the type of the monitored voice commands, and if there are no non-control commands related to security, general commands are performed. Execute the response, and if it involves safety control commands, judge the feature threshold according to the voice sample information to determine whether to refuse to execute the corresponding control commands for children, thus effectively preventing children from controlling smart home devices through voice. The smart device recognizes the location of the monitored voice command to determine whether the voice command is located in the direction of the door. For the voice command received from a direction other than the door, it direct...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com