Communication method, communication device, electronic device, and storage medium
A communication method and equipment technology, applied in the field of communication, can solve problems affecting data security, dependence on transmission data security, and affecting the security of smart terminal transmission data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
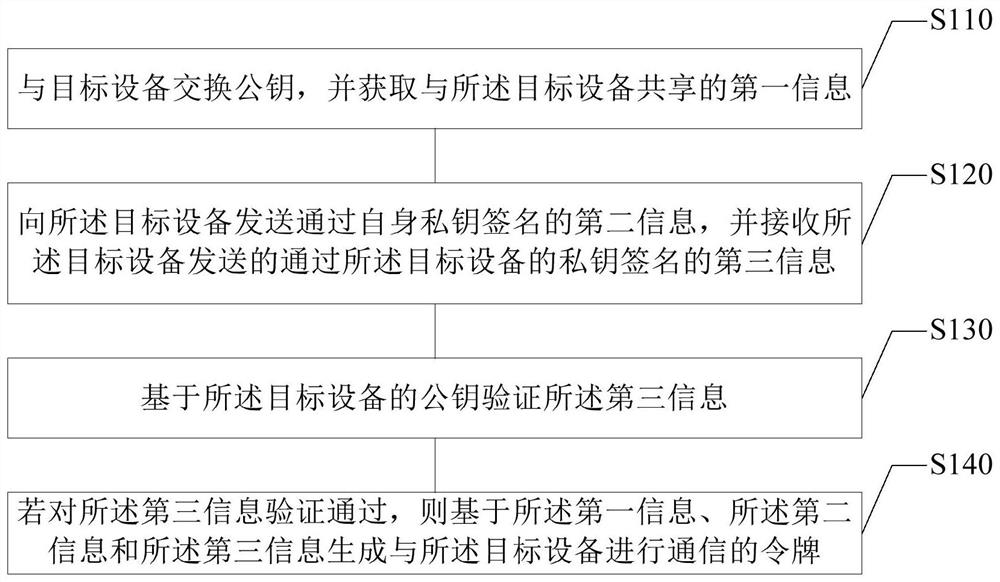
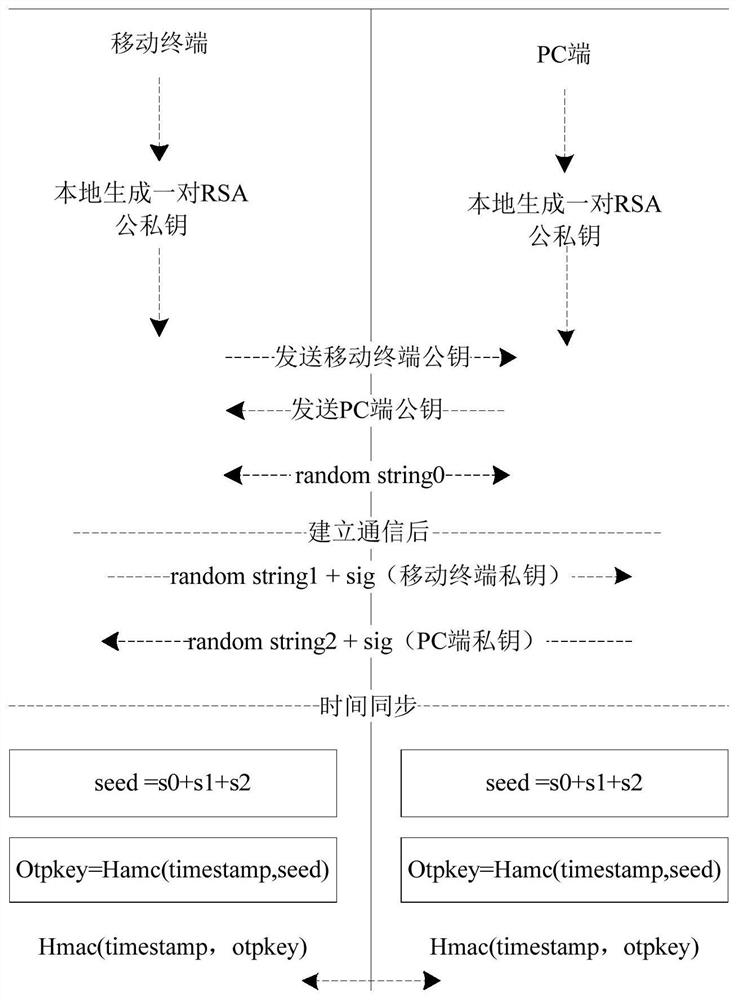
[0072]Using the acquired timestamp as a first parameter, and using the first information, the second information, and the third information as a second parameter, the token is generated through an HMAC algorithm.
[0073] For example, when the first information is a random string string0, the second information is a random string string1 signed by the private key of the mobile terminal itself, and the third message is a random string string2 signed by the private key of the target device , you can combine random strings string0, string1 and string2 into a parameter seed, as shown in the following formula (1):
[0074] seed=string0+string1+string2(1)
[0075] The obtained timestamp timestamp is used as the first parameter, and the parameter seed is used as the second parameter, and the token token is generated through the HMAC algorithm, as shown in the following formula (2):
[0076] token = hmac(timestamp, seed) (2)
[0077] In addition, in order to further enhance the comm...
Embodiment 2
[0080] Using the first information, the second information, and the third information as a parameter, and using the obtained first timestamp as another parameter, generate a dynamic password through the HMAC algorithm; use the obtained second time stamp The stamp is used as the first parameter, and the dynamic password is used as the second parameter, and the token is generated through the HMAC algorithm.
[0081] For example, when the first information is a random string string0, the second information is a random string string1 signed by the private key of the mobile terminal itself, and the third message is a random string string2 signed by the private key of the target device , the random strings string0, string1 and string2 can be combined into a parameter seed through the above formula (1), the parameter seed is used as a parameter, and the obtained first timestamp is used as another parameter to generate a dynamic password optkey through the HMAC algorithm, As shown in ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com