System for preventing smudge and shoulder surfing attacks on mobile device and user pattern authentication method
An authentication method and pattern technology, which is applied in the field of system and user pattern authentication for preventing stain and peeping attacks on mobile devices, can solve problems such as attacks, and achieve the effect of defending against stains and peeping attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
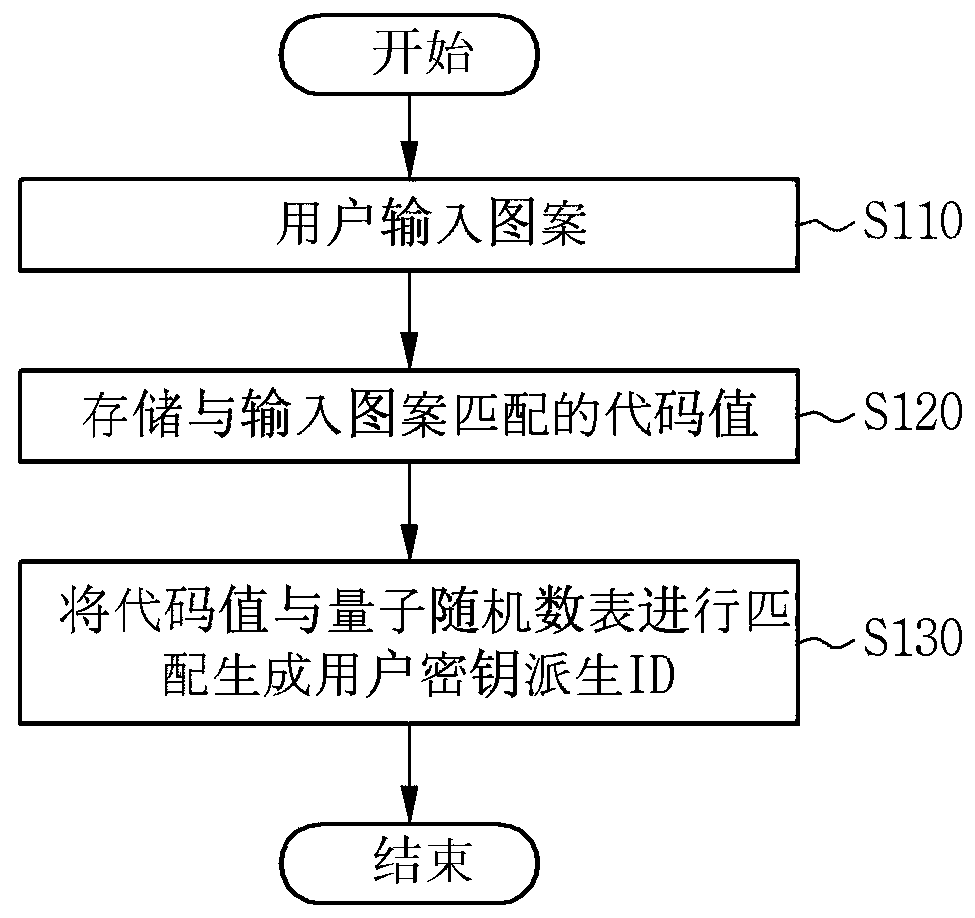
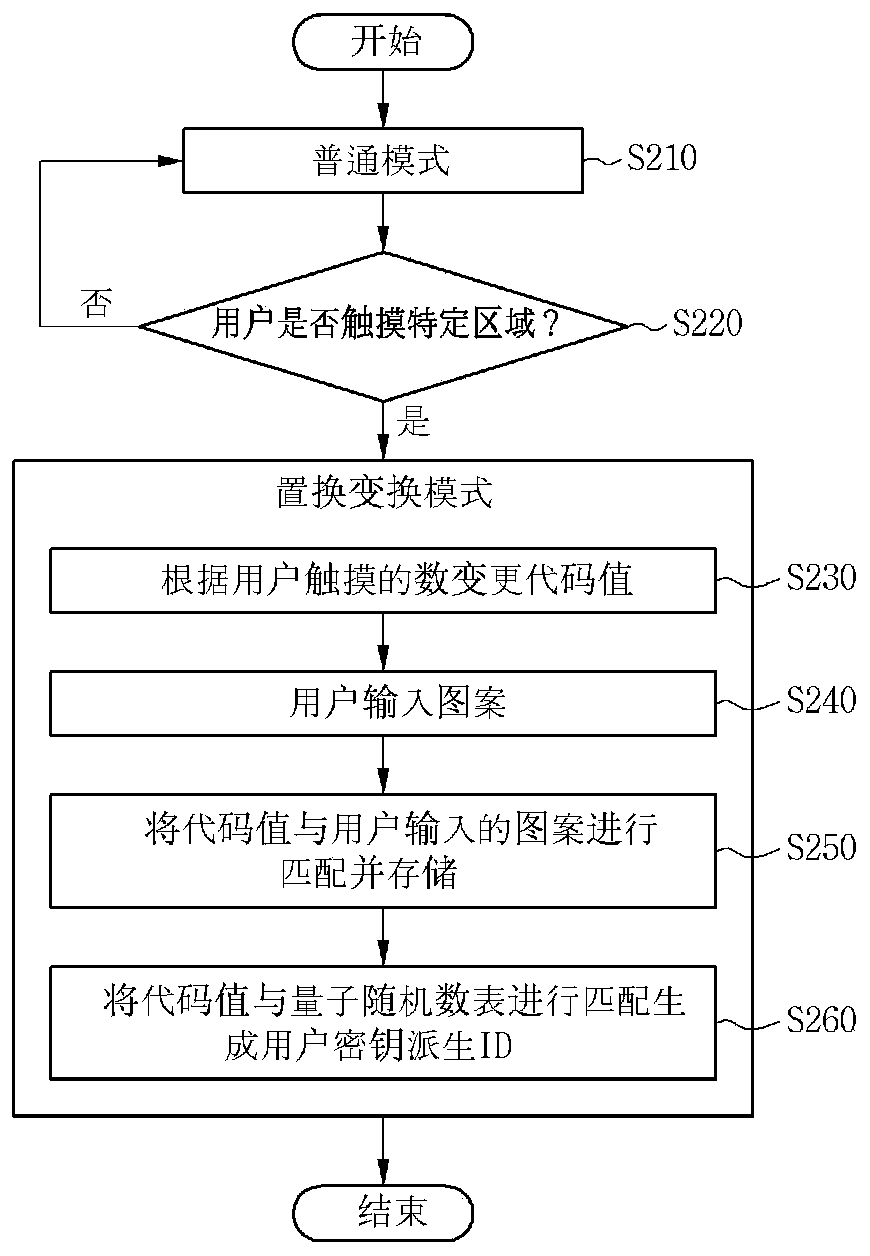
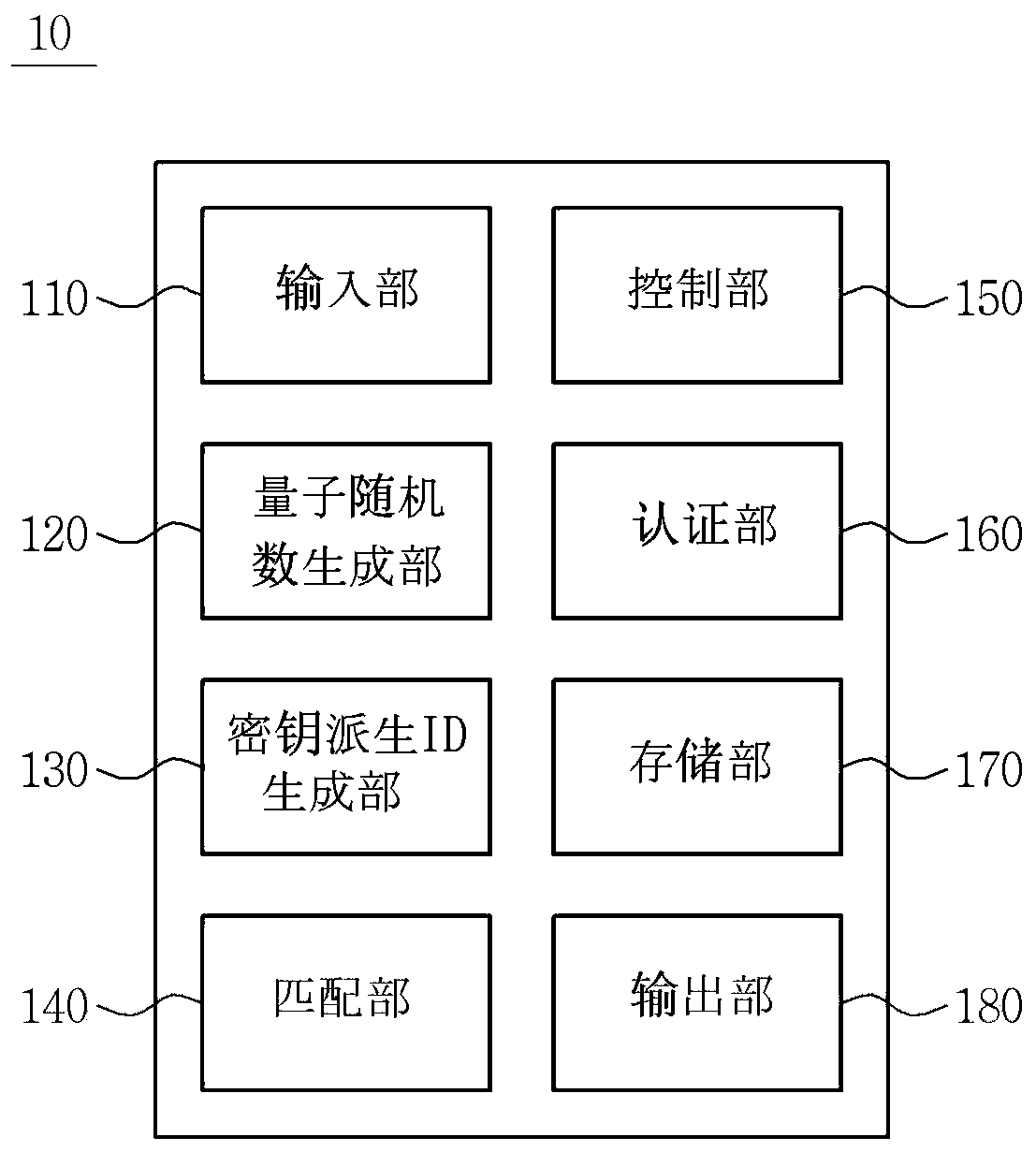
[0017] The specific structural or functional descriptions of the embodiments according to the concept of the present invention disclosed in this specification are only examples for illustrating the embodiments according to the concept of the present invention, therefore, the embodiments according to the concept of the present invention can be various Embodiments are not limited to the examples described in this specification.
[0018] Embodiments according to the concept of the present invention can be variously modified and have various forms, and therefore, the embodiments are illustrated in the drawings and described in detail in this specification. However, it is not intended to limit the embodiment of the concept of the present invention to a specific disclosed form, and includes all changes, equivalents, and substitutes included in the concept and technical scope of the present invention.
[0019] The terms used in this specification are for describing specific embodimen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com