Secret key management system and method of media stream based on IP multi-media sub-system
A multimedia subsystem and key management technology, which is applied in the field of IP multimedia subsystem, can solve the problems of increasing computing overhead and storage requirements of streaming media servers, reducing the efficiency of streaming media servers, etc., to reduce key management overhead and simplify functions , the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
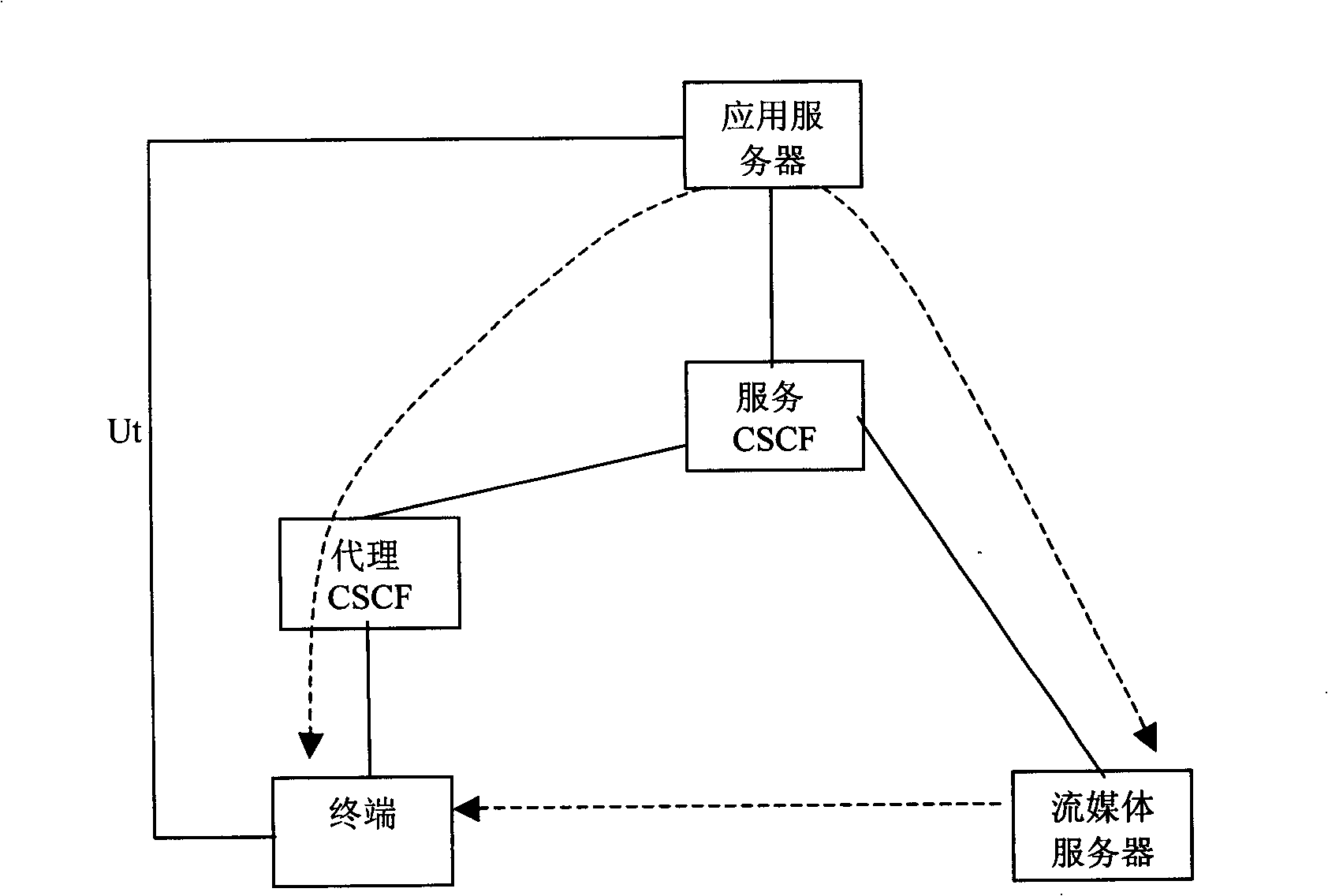
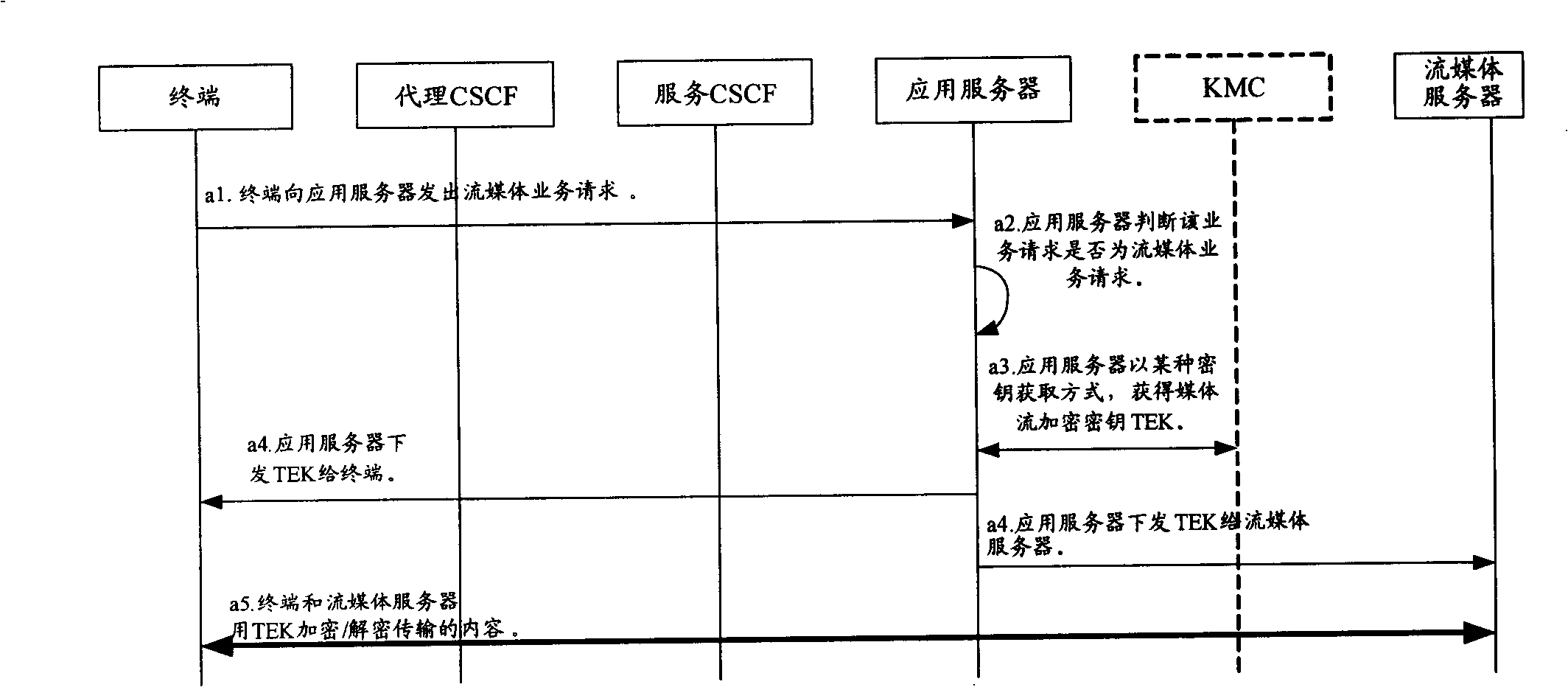
[0037] Embodiment 1: After receiving the service request from the terminal, the application server obtains a key in one of several ways to obtain a key, and sends the key as a TEK to the terminal and the streaming media server. The terminal and the streaming media server use the TEK to encrypt / decrypt the streaming media content transmitted between them.
no. 2 example
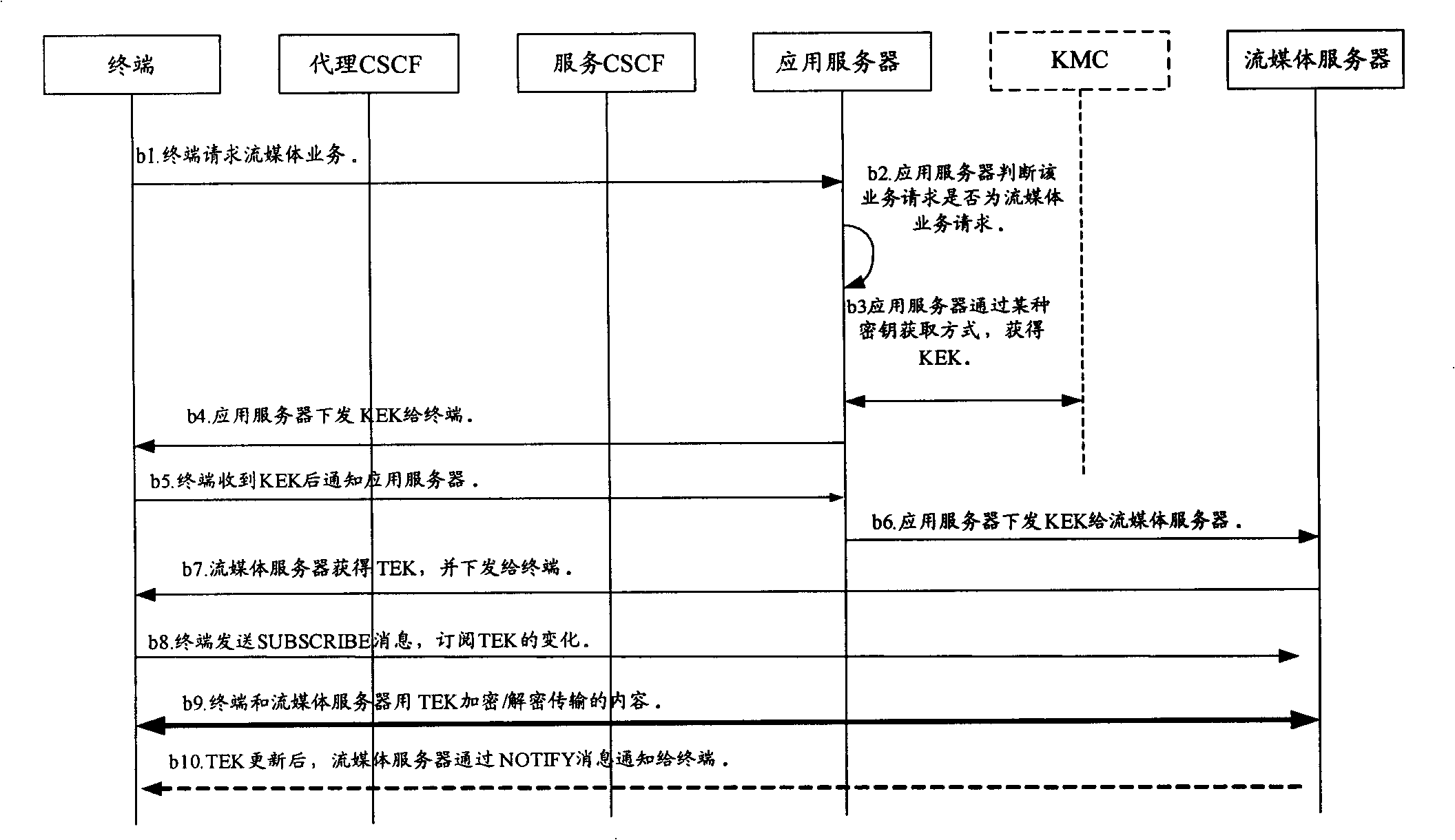
[0038] Embodiment 2: After receiving the service request sent by the terminal, the application server obtains a key in one of several ways to obtain a key, and sends the key as a KEK to the terminal and the streaming media server. The streaming media server obtains a key in one of several ways to obtain a key, uses the key as a TEK, and sends the TEK to the terminal through the protection of the KEK, and the terminal and the streaming media server use the TEK to encrypt / decrypt two The streaming media content transmitted between the parties; or after the application server sends the KEK to the terminal and the streaming media server, the terminal and the streaming media server use the KEK to negotiate the TEK. The advantage of using delivery instead of negotiation is that the streaming media server can be controlled to use the same TEK for different users using the same service, thereby reducing the encryption load of the streaming media server.
no. 3 example
[0039] Embodiment 3: After receiving the service request from the terminal, the application server obtains two keys in one of several key acquisition ways, one as KEK and the other as TEK. The application server sends the KEK to the terminal, and through the protection of the KEK, sends the TEK to the terminal. At the same time, the application server sends the TEK to the streaming media server. The terminal and the streaming media server use the TEK to encrypt / decrypt the streaming media content transmitted between them.
[0040] In the second embodiment and the third embodiment above, the application server and the terminal can also obtain the key shared by the two through GBA (General Bootstrapping Architecture, general bootstrapping architecture) or other methods and use it as a KEK.
[0041] In the above-mentioned second and third embodiments, the network side entity can save the KEK within the validity period of the service, so that when the terminal requests the service...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com