Control system and method with authentication function
A technology for control systems and authentication methods, applied in the usage of multiple keys/algorithms, user identity/authority verification, etc., and can solve problems such as inability to conform to users, password changes, and inability to randomly change
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] Regarding the control system and method with authentication function described in the present invention, further understanding can be obtained through the following detailed description of the invention and the accompanying drawings.
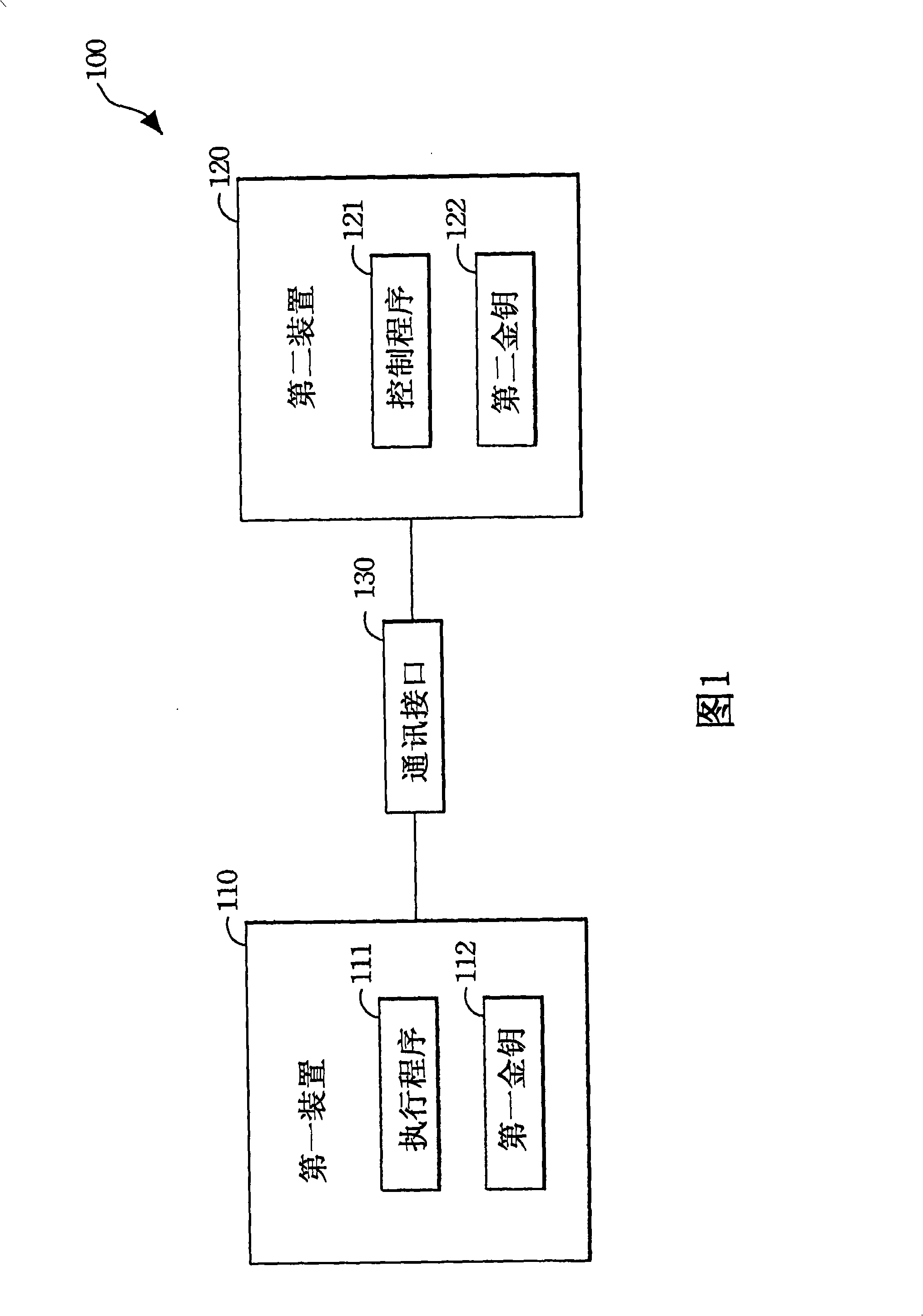
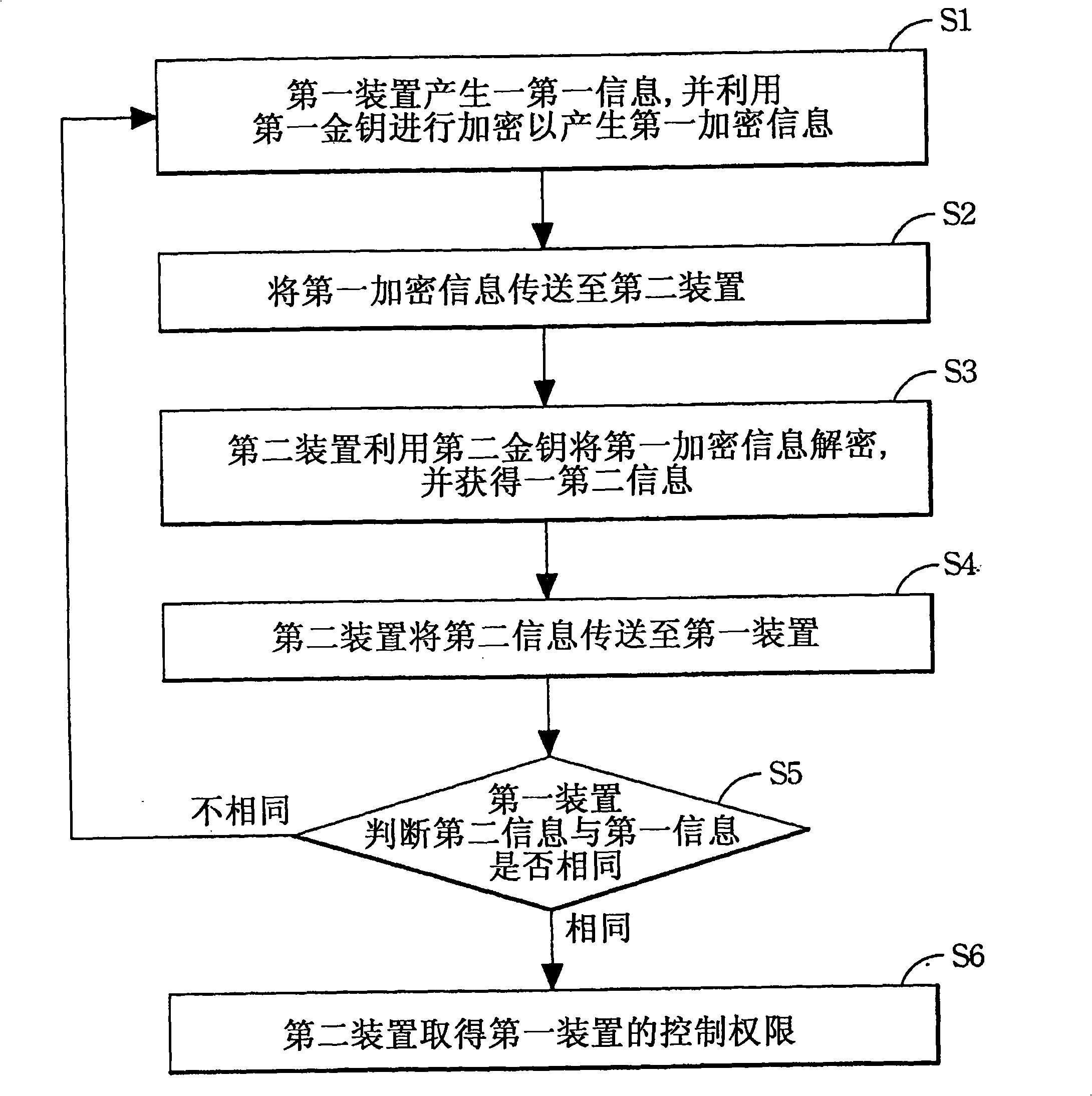
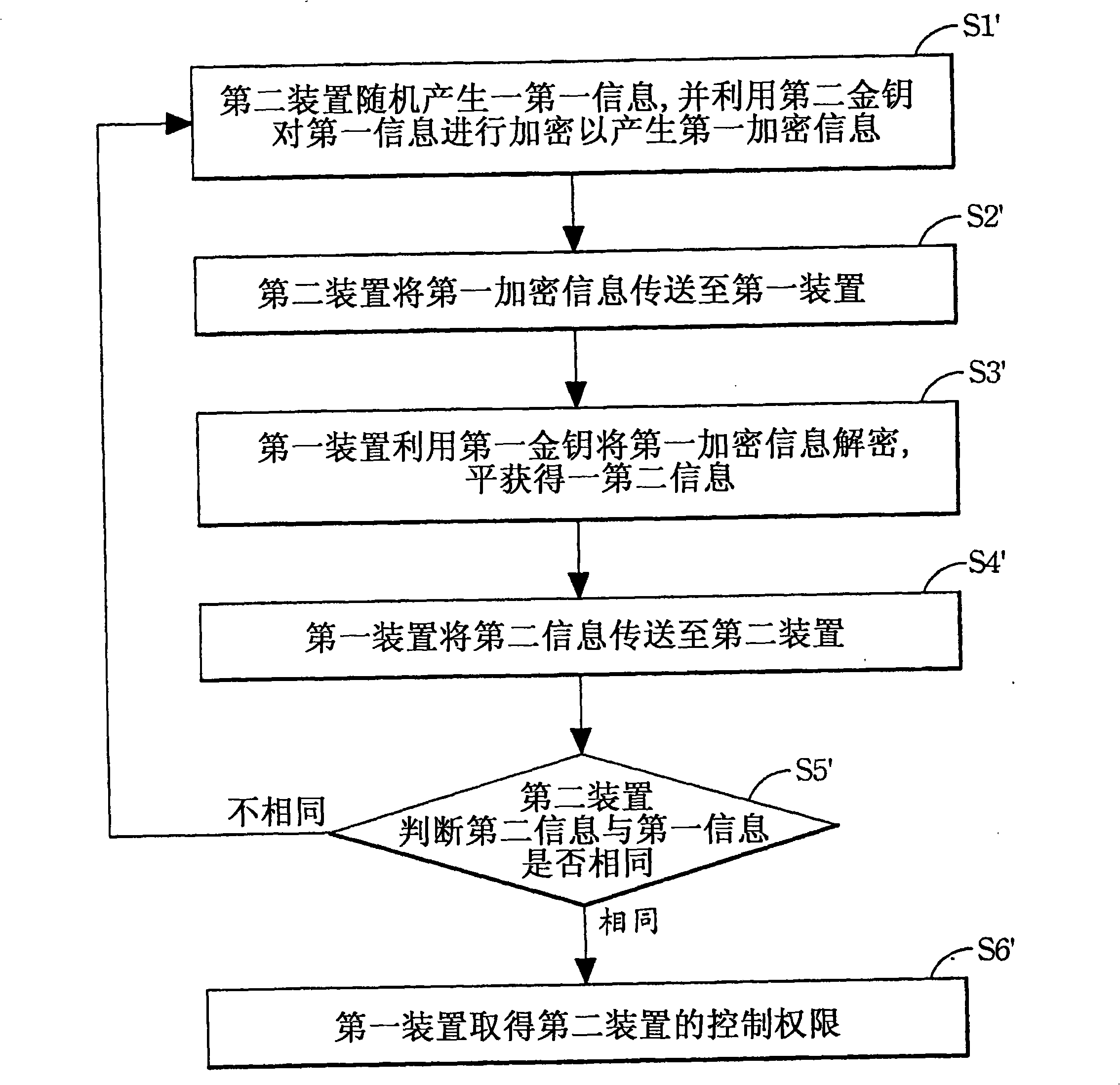
[0032] Since there are many kinds of communication interfaces of instruments at present, such as GPIB, RS232 / 482 / 485, USB, Ethernet, etc., the present invention will be applicable to all models. When these common communication interfaces are used for information transmission, the The content can be monitored, which means that these communication data are completely open, so the present invention designs an authentication device and its related method, even if the communication data is completely open, it can also achieve the effect of confidentiality. The following will describe this in detail Invented design.
[0033] First of all, please refer to FIG. 1 , which is the basic concept of the design of the present invention and also a schem...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com