Method for detecting network abnormality based on secondary negative selection
A technology that negates selection and detection methods, applied in the field of information security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0028] The specific method of the present invention will be described in detail below in conjunction with the accompanying drawings.
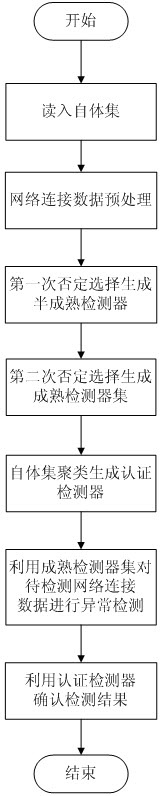
[0029] figure 1 It is a working principle diagram of the present invention.
[0030] figure 1 It is a working principle diagram of the present invention. A network anomaly detection method based on secondary negative selection proposed by the present invention first selects normal network connection data as the self-set for training, then generates a mature detection set through the secondary negative selection process to perform abnormal detection on the network connection data to be detected, and finally The detection results are confirmed by the authentication detector generated by self-set clustering. The present invention is divided into two relatively independent stages. The first stage is the process of generating mature detector sets and authenticating detectors according to the self-set, including the step of reading into the se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com