A software security analysis method and system based on immune model
A software security and analysis method technology, applied in computer security devices, instruments, computing, etc., can solve problems such as high complexity, difficulty in automatic discovery, and large result sets of static analysis methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
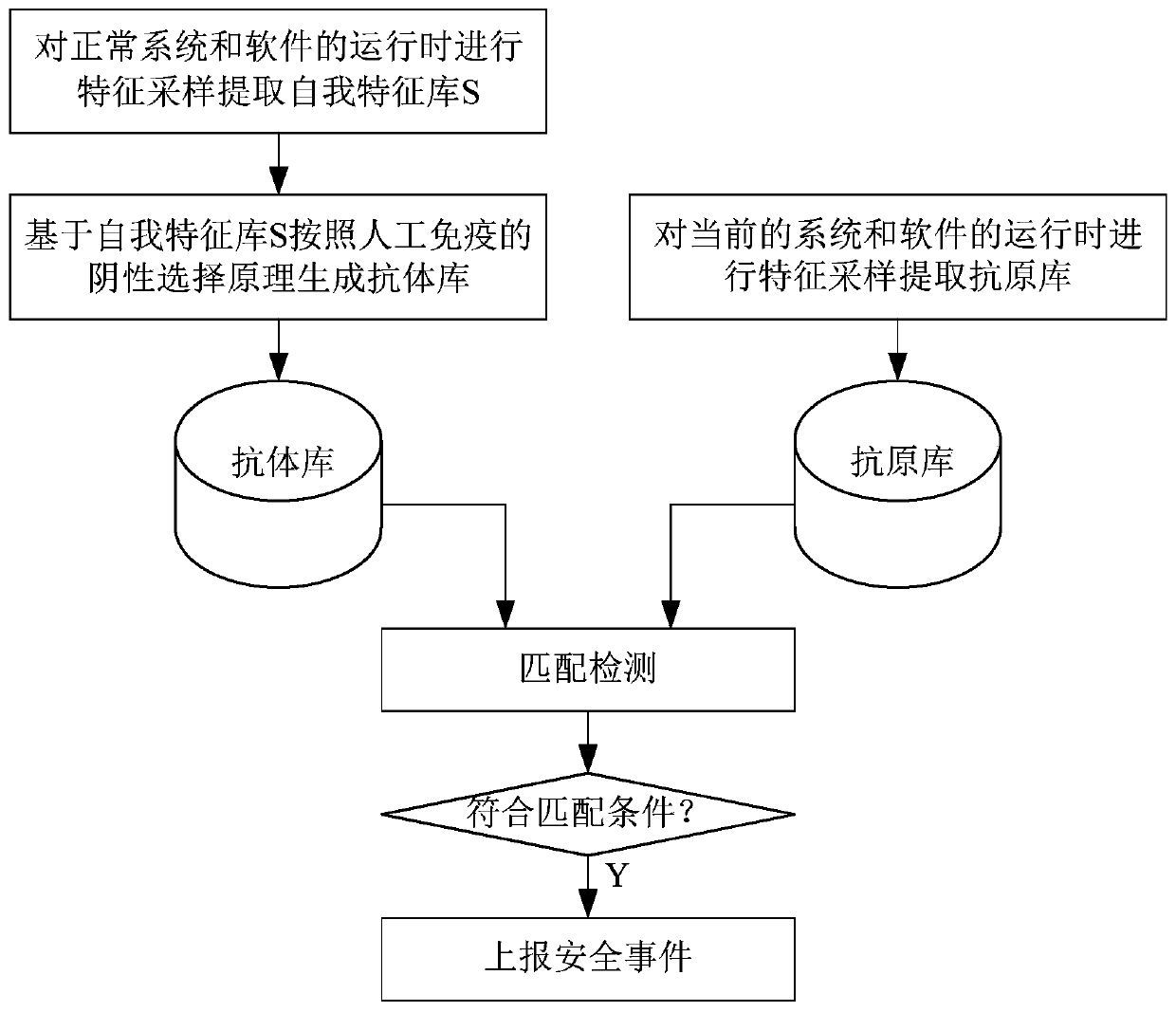
[0045] like figure 1 As shown, the implementation steps of the immune model-based software security analysis method in this embodiment include:
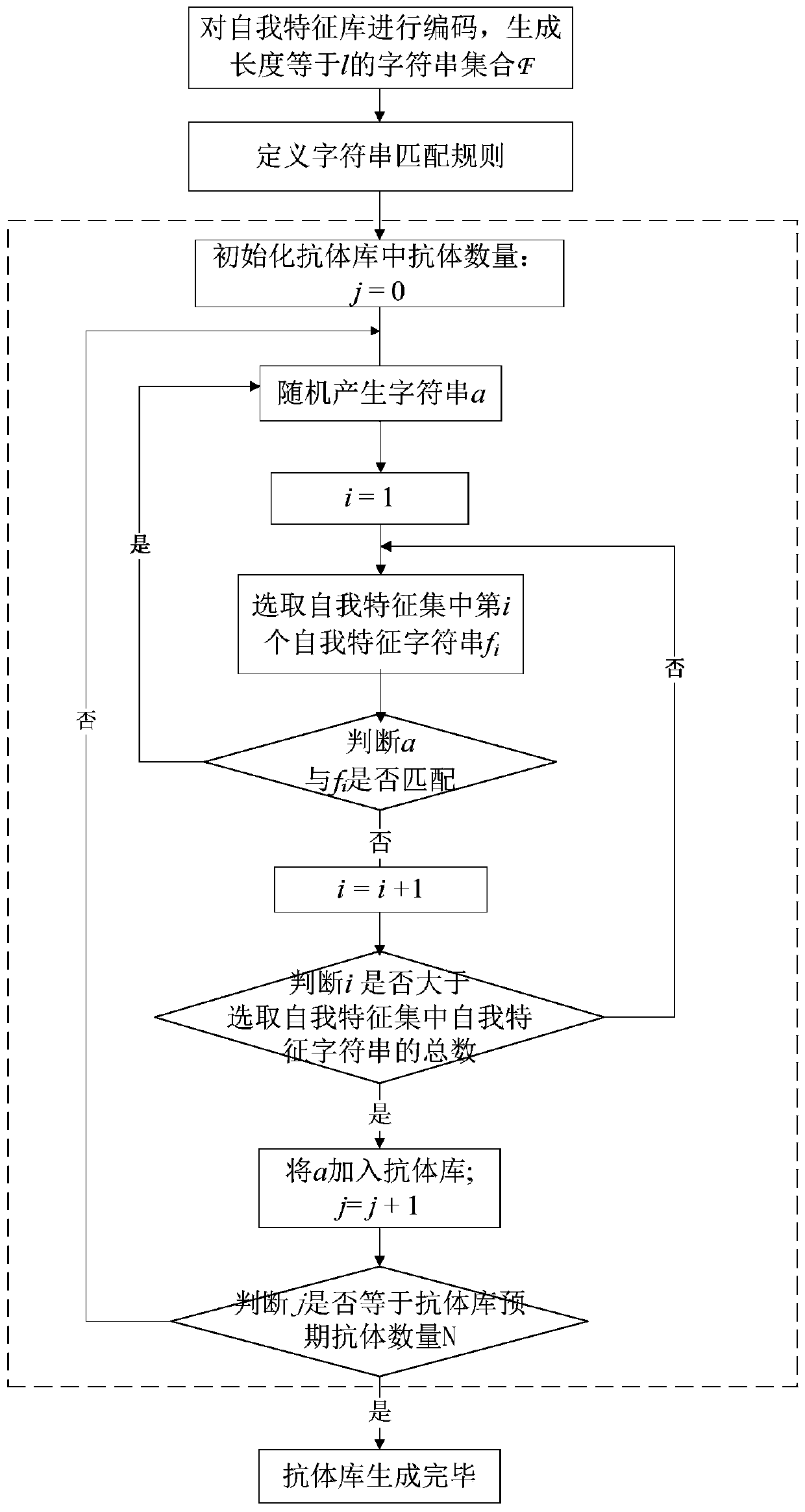
[0046] 1) Perform feature sampling on normal system and software operation in advance to extract the self-signature library S, and generate an antibody library based on the self-signature library S according to the negative selection principle of artificial immunization; jump to the next step when software security analysis is required;
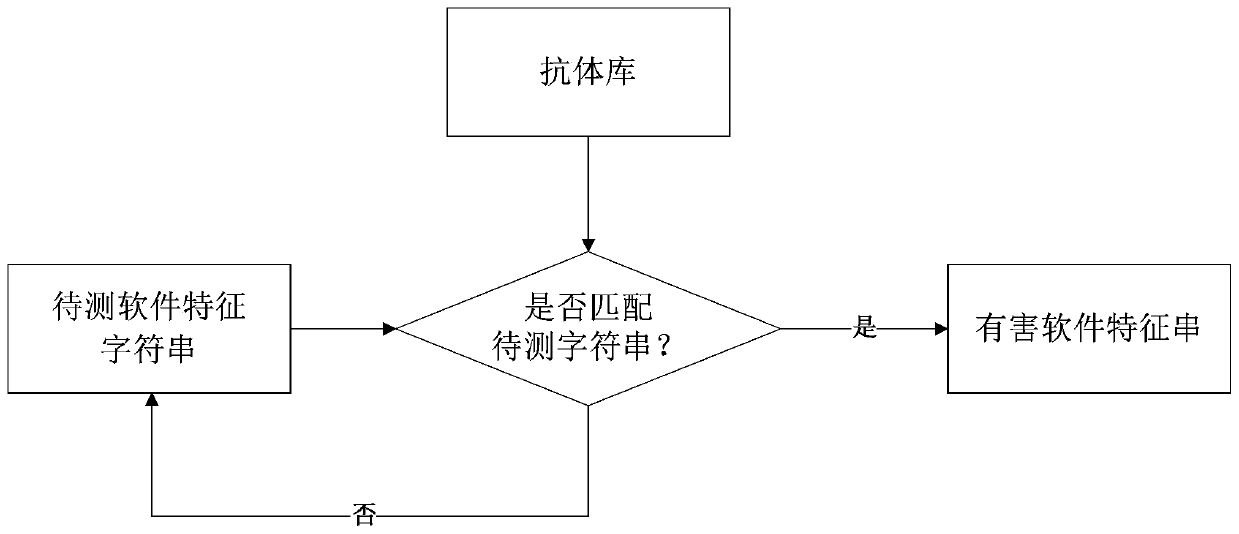
[0047] 2) Perform feature sampling on the runtime of the current system and software to extract the antigen library, match the characteristic strings in the antigen library with the antibodies in the antibody library, and report a security incident if the matching conditions are met.
[0048] Negative Selection Algorithm (Negative Selection Algorithm) is a bionic algorithm proposed with reference to the negative selection principle of the biological immune system, and is one of the core algorithms ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com