Authentication server device, authentication server device-use program and authentication method
A technology for authenticating servers and authenticating requests, applied in digital data authentication, computer security devices, instruments, etc., can solve the problems of inability to input characters, the server cannot correctly authenticate the operation of people, and cannot recognize characters, etc., and achieves the effect of suppressing the load.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 approach
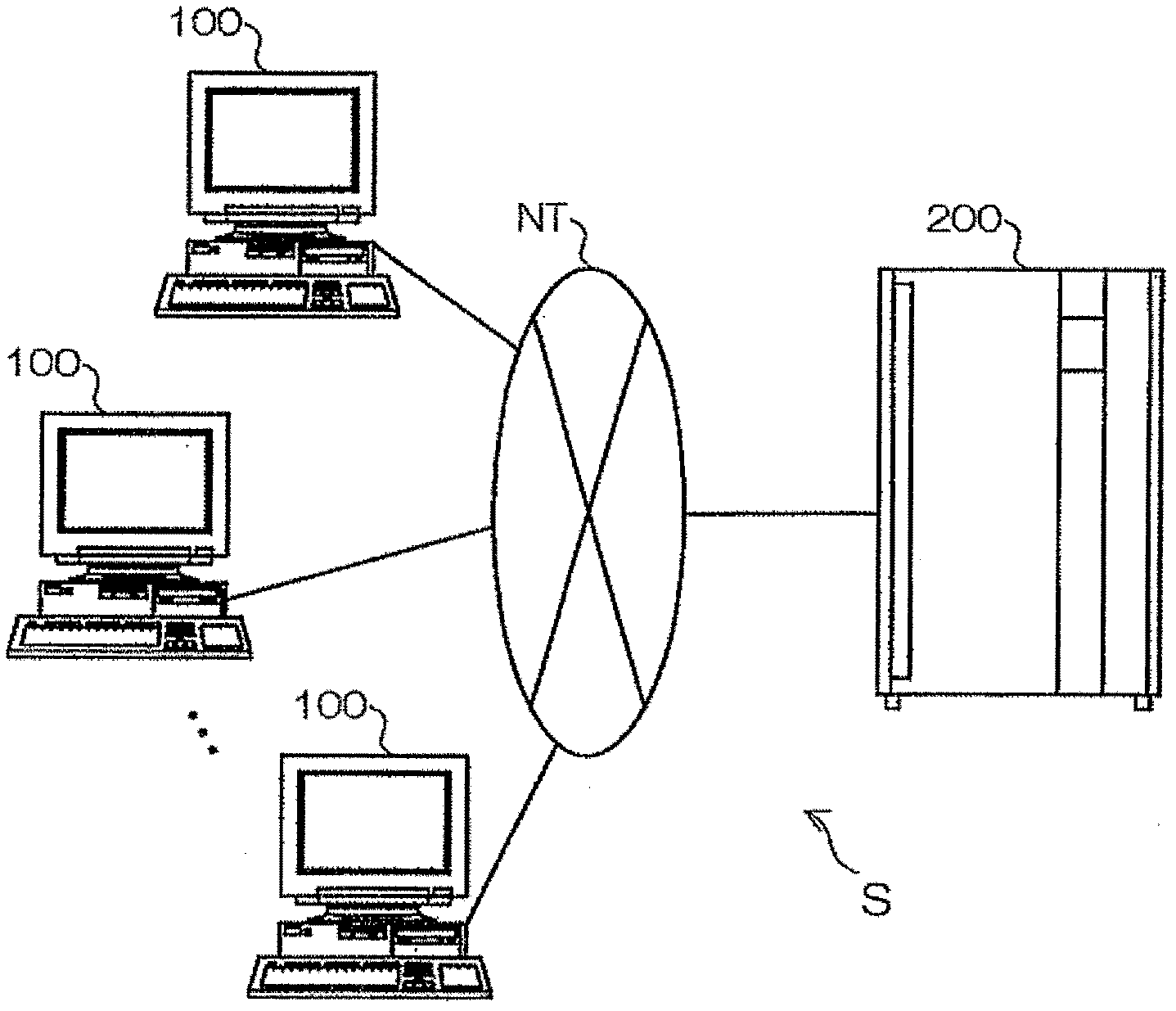
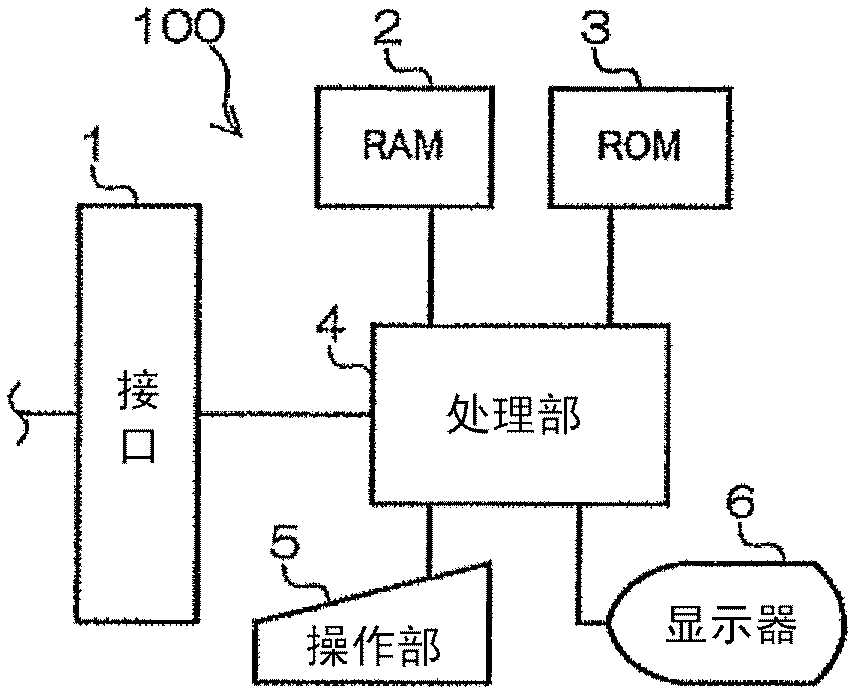
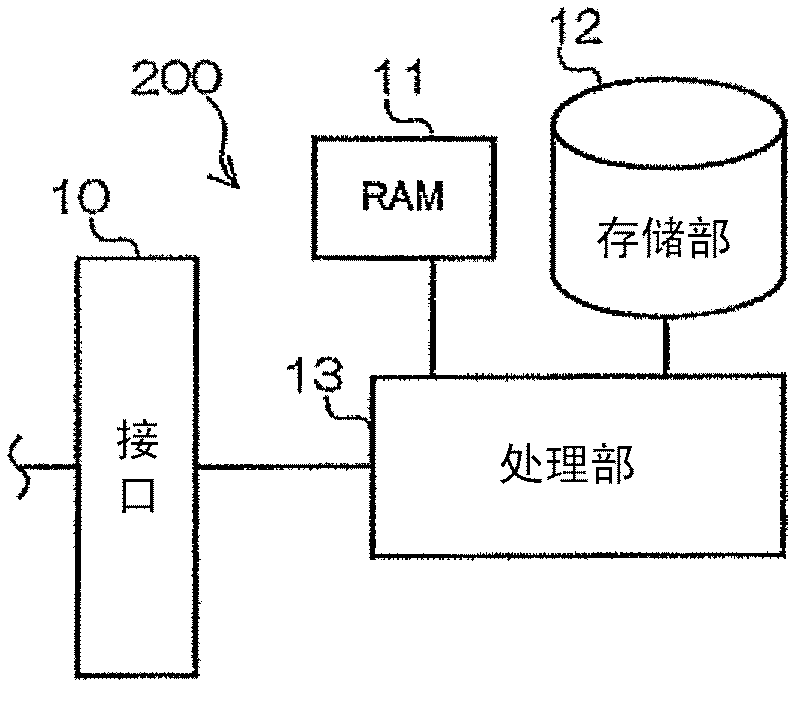
[0041] First, by attaching Figure 1 to Figure 10 A first embodiment of the present invention will be described. in addition, figure 1 is a block diagram showing a general configuration of the authentication system of the first embodiment; figure 2 It is a block diagram showing the detailed configuration of the user terminal of the first embodiment. in addition, image 3 is a block diagram showing a detailed configuration of the server of the first embodiment; Figure 4 It is a figure which exemplifies the storage content of the memory|storage part of 1st Embodiment. in addition, Figure 5 to Figure 8 are flowcharts respectively showing the authentication processing of the first embodiment, Figure 9 is a flowchart showing the details of authentication processing, Figure 10 It is a diagram showing an example of an operation screen displayed on a user terminal during the authentication process.
[0042] Such as figure 1 As shown, the authentication system S of the fi...
no. 2 approach
[0076] Next, pass Figure 11 A second embodiment which is another embodiment of the present invention will be described. in addition, Figure 11 It is a diagram showing an example of an operation screen displayed on a user terminal. In addition, since the hardware configuration of the authentication system of the second embodiment is basically the same as that of the authentication system S of the first embodiment, in the following description, the same as that used in the description of the authentication system S of the first embodiment will be used. The second embodiment will be described with reference to the part number.
[0077] In the above-mentioned first embodiment, according to the operation instruction 61 (refer to Figure 10 ) to operate cursor P and select objects 62 to 66 (refer to Figure 10 ), and then perform the authentication operation. In contrast, in the second embodiment to be described below, the object itself displayed on the display 6 is moved acc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com