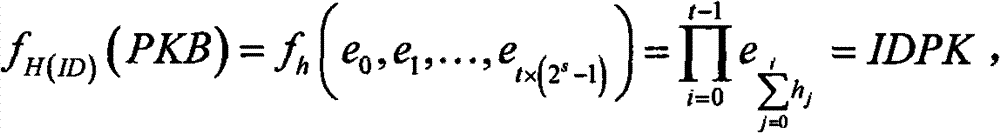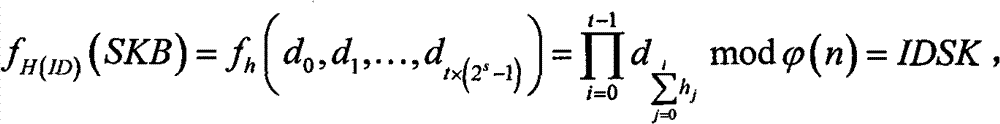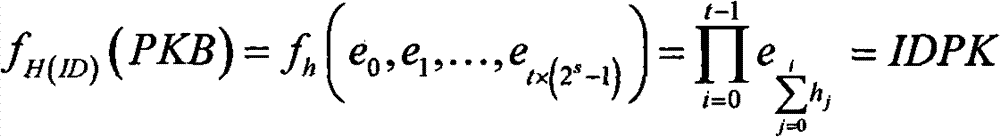Identifier-based certificate authentication system CFL
An identification and certificate technology, applied in the field of information security, can solve the problem of private keys without private rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0044] 1. CFL workflow based on exponential product public key cryptography algorithm
[0045] User's operation
[0046] 1) The user generates his own real identification ID
[0047] 2) The user generates a set of random public and private key pairs (RAPK, RASK) according to the work password algorithm independently selected
[0048] 3) The user submits the ID and RAPK to the key management center KMC
[0049] Operation of Key Management Center KMC
[0050] 4) KMC reviews the ID submitted by the user to ensure its authenticity and uniqueness
[0051] 5) Input the ID into H to obtain the control information h input by the multi-linear function
[0052] 6) According to h and the private key basis, the following multi-linear function is transformed:
[0053]
[0054] Generate the identity private key IDSK
[0055]7) Use the signature algorithm SIGN and IDSK as the key to sign the certificate with RAPK as the core content, and get: sign=SIGN IDSK (RAPK)
[0056] 8) Issu...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com