An anti-copy software protection and operation device and method
A software protection device and software protection technology, applied in the direction of program/content distribution protection, digital data authentication, etc., can solve the problems of data interception and cracking, flooding, etc., and achieve the effect of solving copyright protection and preventing wanton copying and dissemination
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0066] Embodiment 1: Application Model 1 (copyright protection):
[0067] Implementation principle:
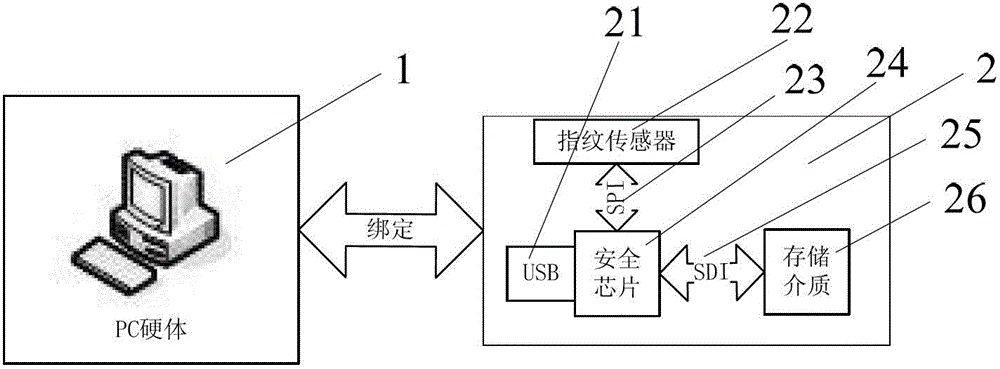
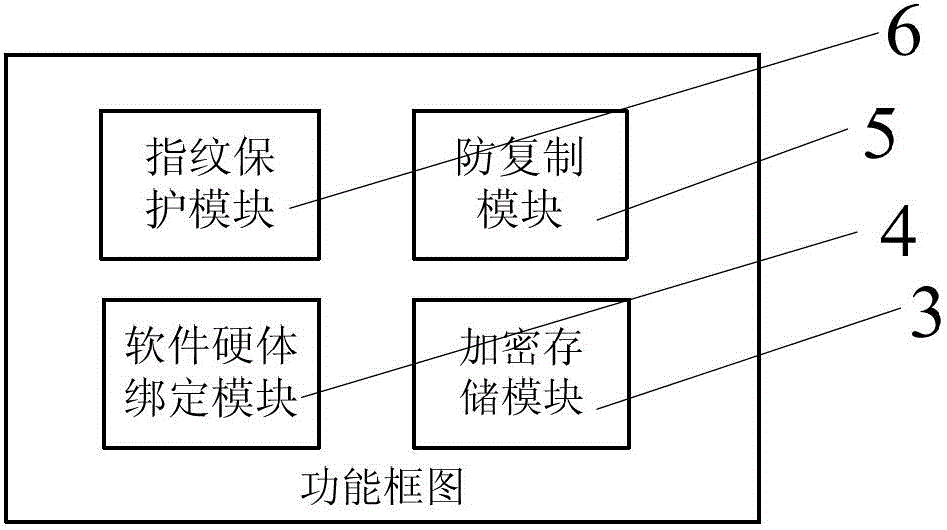
[0068] 1. Use the software protection device 2 to generate the symmetric encrypted storage key KEY1. For the operation method, please refer to the first part of the working principle of the module "Working principle of the encrypted storage module 3";
[0069] 2. Use the software protection device 2 to generate a public / private key pair (PriKey / PubKey), and bind it to relevant data that needs to be protected by copyright, such as PC software, audio-visual products, etc. For details of the operation method, see the second part of the working principle of the module " The working principle of the software and hardware binding module 4";
[0070] 3. The software protection device 2 is connected to the PC and virtualized as an optical drive device;
[0071] 4. Convert the functional software and related data to be protected into an ISO image file, burn it in the software protect...
Embodiment 2
[0080] Example 2: Application Model 2 (multi-partition secure storage):
[0081] Implementation principle:
[0082] 1. Use the software protection device 2 to generate the symmetric encrypted storage key KEY1. For the operation method, please refer to the first part of the working principle of the module "Working principle of the encrypted storage module 3";
[0083] 2. Use the software protection device 2 to generate a public / private key pair (PriKey / PubKey), and bind the fingerprint encryption U disk management software. For the operation method, please refer to the second part of the working principle of the module "Working principle of software and hardware binding module 4" ;
[0084] 3. The software protection device 2 is connected to the PC to virtualize an optical drive device, an encrypted storage U disk device, and an ordinary device;
[0085] 4. Convert relevant functions and management software (anti-copy code, fingerprint encryption U disk management software, e...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com