An android malicious code detection method based on category analysis
A malicious code detection, classification technology
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The technical solution of the present invention will be described in detail below in conjunction with the accompanying drawings.
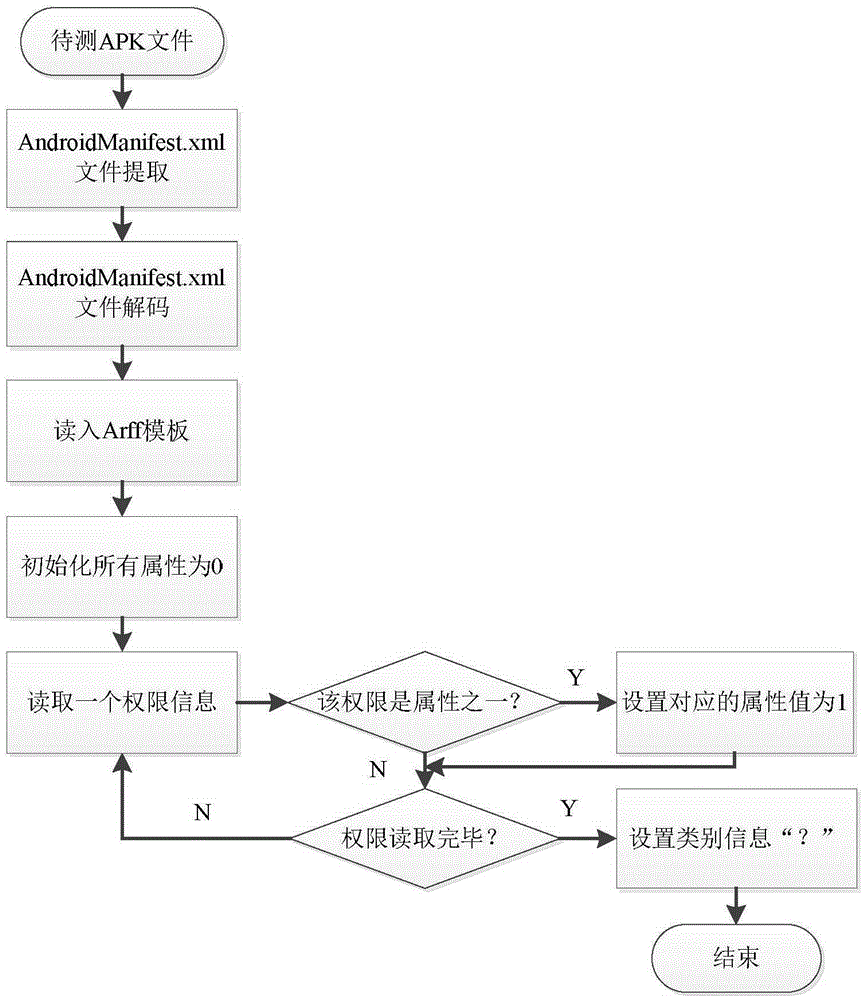
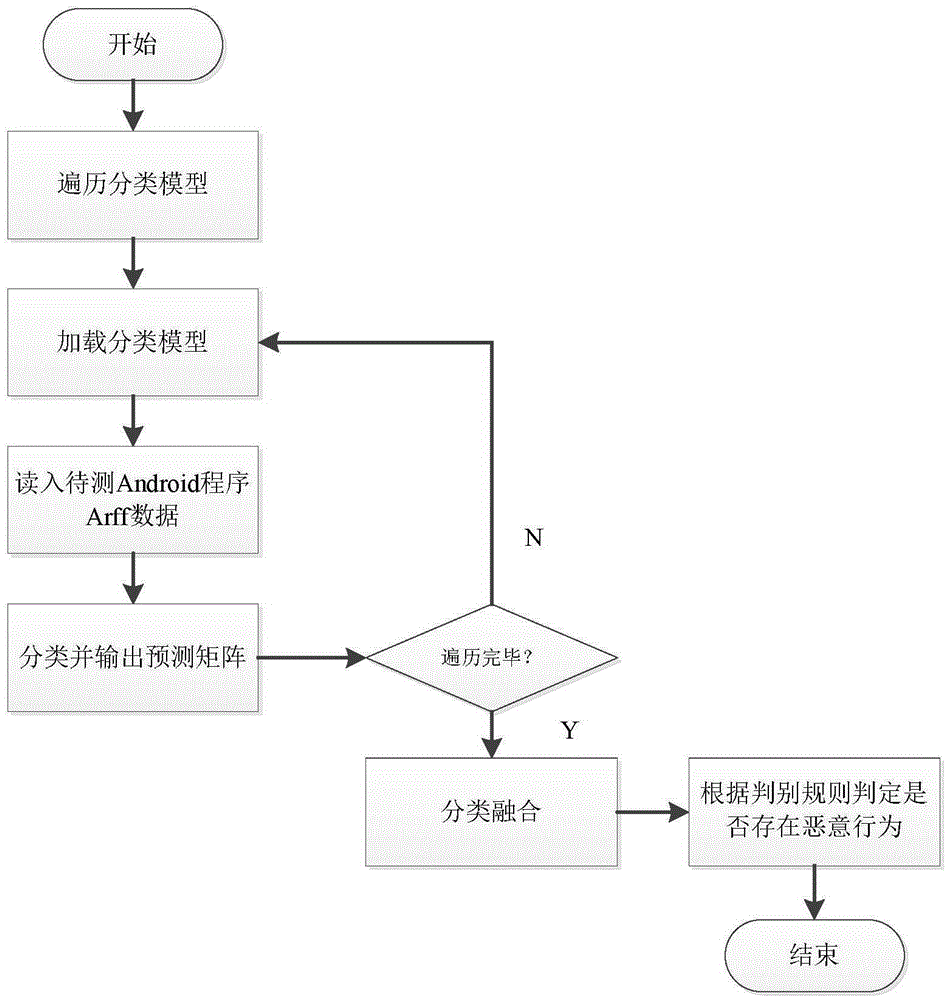
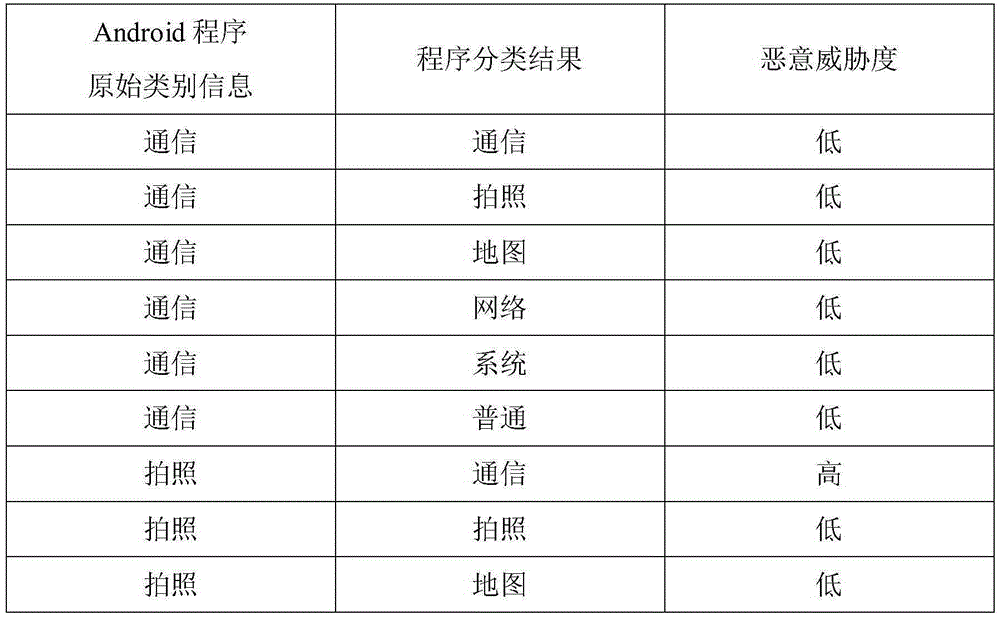
[0025] The overall idea of the present invention is to adopt a category classification method based on permission information, extract permission information from the Android program to be detected, input it into the classification model for classification, compare the classification result with the declared category, and judge whether there is malicious behavior according to the discrimination rules .
[0026] refer to figure 1 , 2 , in a specific embodiment, the present invention comprises the following steps:
[0027] The first step is to collect a predetermined amount of M Android programs and divide them into six categories: communication, camera, map, network, system, and general. Those skilled in the art should understand that the value of the predetermined amount M should be large enough to meet the needs of sample analysis. In...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com