Method for automatically extracting and analyzing firewall logs based on XML rule model
An automatic extraction and analysis method technology, applied in hardware monitoring and other directions, can solve the problems of unable to analyze abnormal behavior information, no abnormal log analysis function, and inconvenient unified analysis of firewalls
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The following describes the specific implementation method of the technical solution proposed by the present invention based on the firewall log.
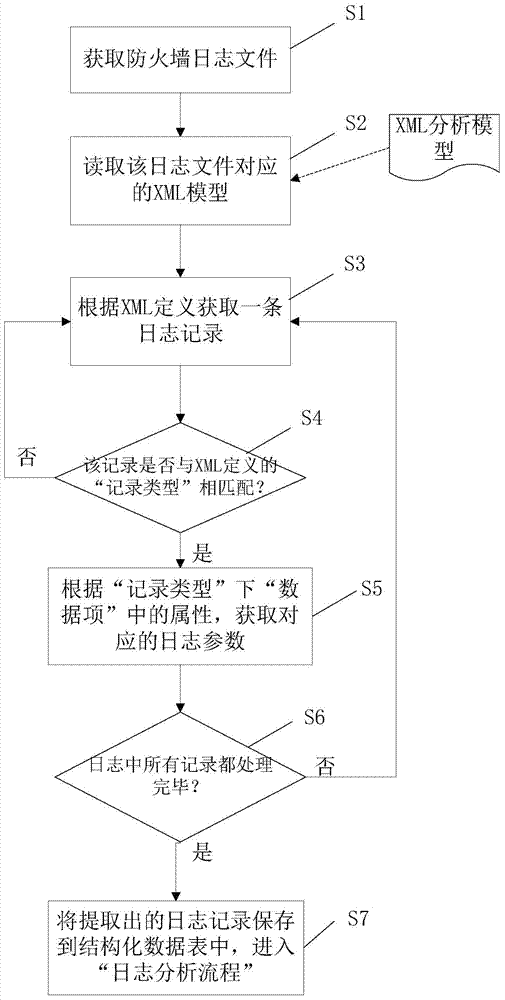
[0041] Such as figure 1 As shown, the firewall log extraction method implemented by the present invention first obtains the firewall log file regularly, step S1. Read the XML model corresponding to the log file according to the XML analysis model, step S2.
[0042] Obtain a log record from the log file according to the XML model definition, step S3. It is judged whether the characteristic value of the log record matches the "record type" defined by XML, step S4. If it does not match, go to S3. If they match, advance the corresponding log parameters according to the attributes in the "data item" under the "record type", step S5.
[0043] It is judged whether all records in the log file have been processed, step S6. If not finished, go to S3. If all the records have been processed, save all the extracted log records in the struc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com