Key vehicle law violation forbidding intrusion management system and method
A technology for managing systems and vehicles, applied in the direction of traffic flow detection, etc., can solve the problems of high installation cost of on-board equipment, dependence on on-board equipment and manual law enforcement, etc., to achieve a high degree of freedom and prevent illegal intrusions.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0030] Preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
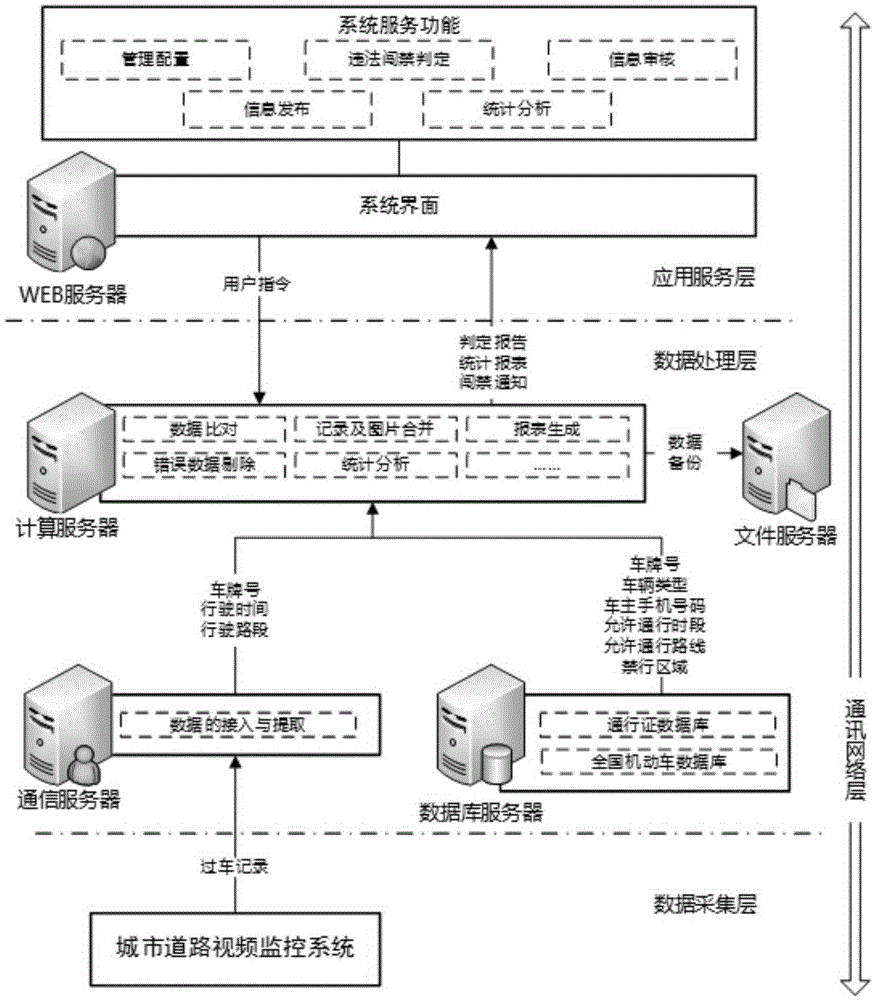
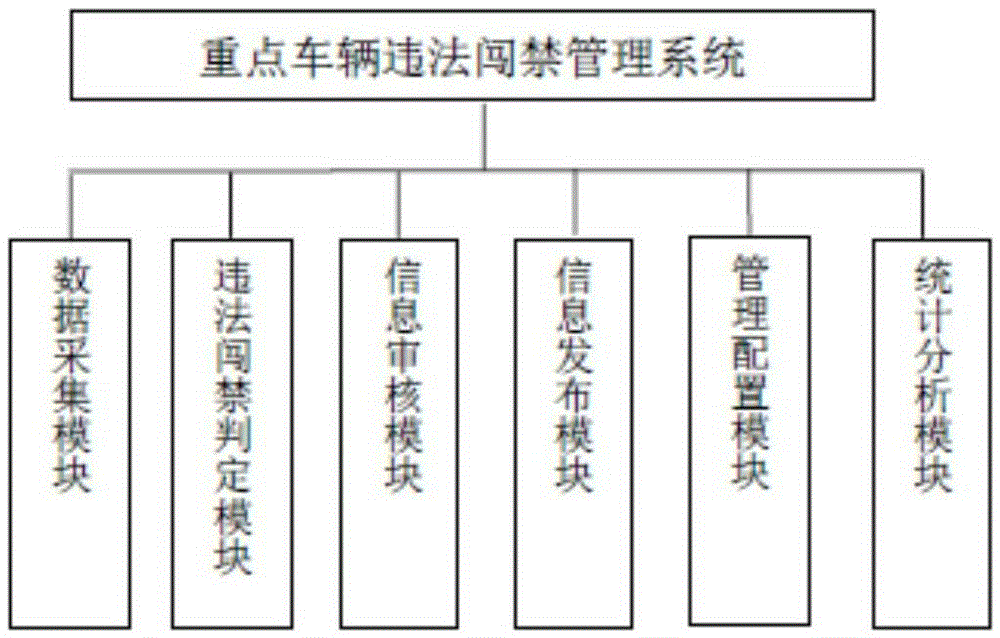
[0031] A key vehicle illegal entry management system, including a data acquisition module, a management configuration module, an illegal entry judgment module, an information review module, an information release module, and a statistical analysis module, such as figure 1 and figure 2 .
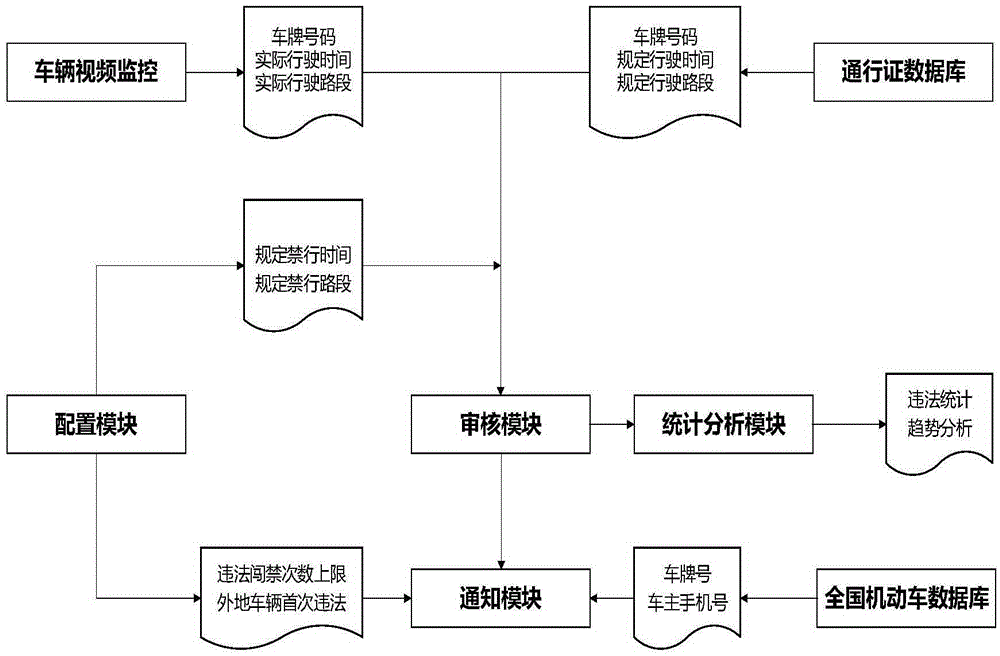
[0032] Data acquisition module: obtain the driving data of key vehicles and the corresponding pass data of the key vehicles, and transmit the driving data and pass data to the illegal entry and entry judgment module.
[0033] Illegal entry and entry determination module: According to the driving data and pass data of key vehicles obtained by the data acquisition module, the driving data is compared with the pass data, and the vehicle that has illegal entry and exit is automatically identified, and a preliminary judgment report is generated.
[0034] Infor...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com