Network attack defense method based on dns intelligent analysis system
A network attack and intelligent analysis technology, applied in transmission systems, electrical components, etc., can solve the problems of slow effective time, increased data cleaning costs, manual analysis, etc., and achieve the effect of reducing resource consumption
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
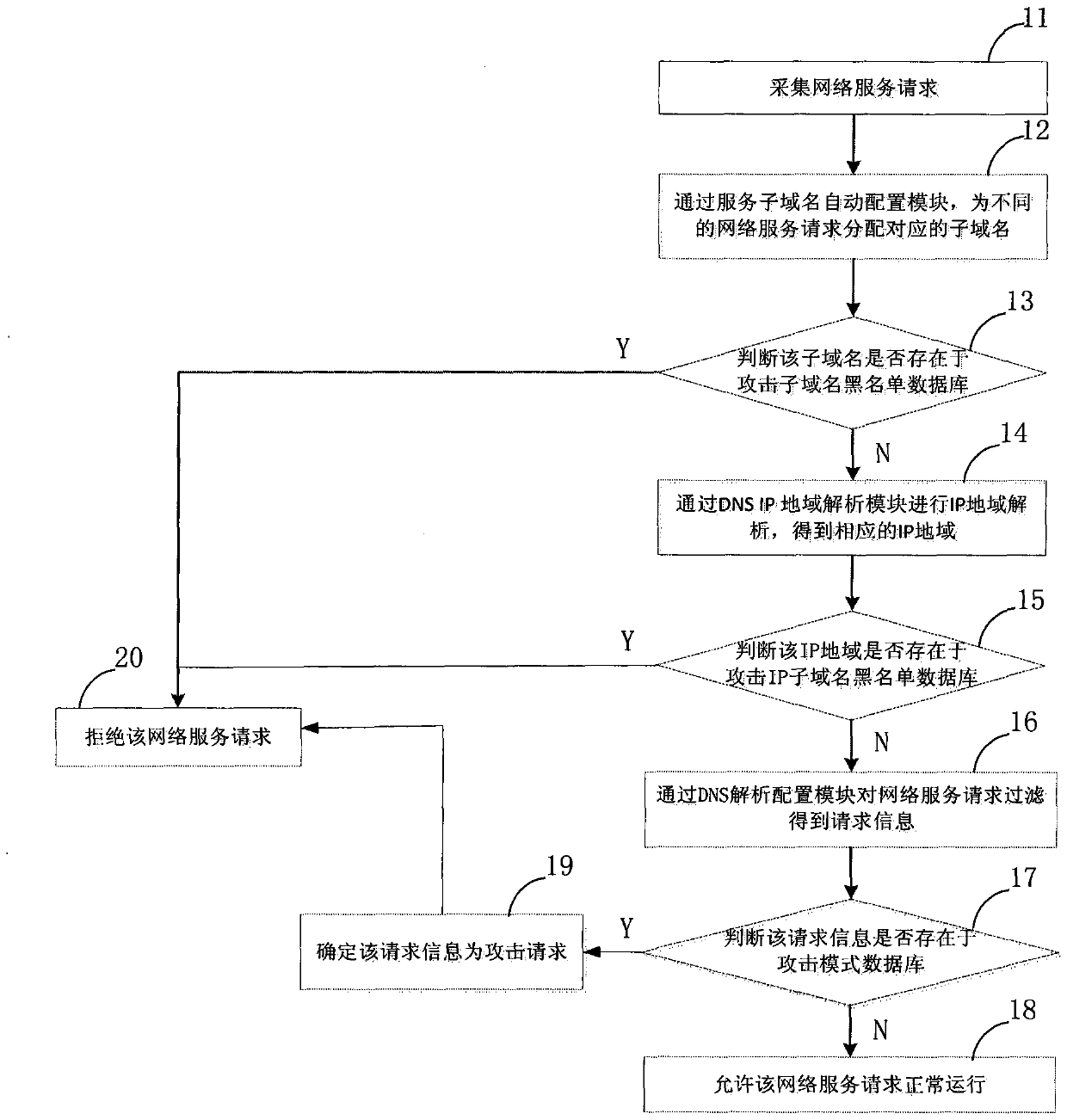
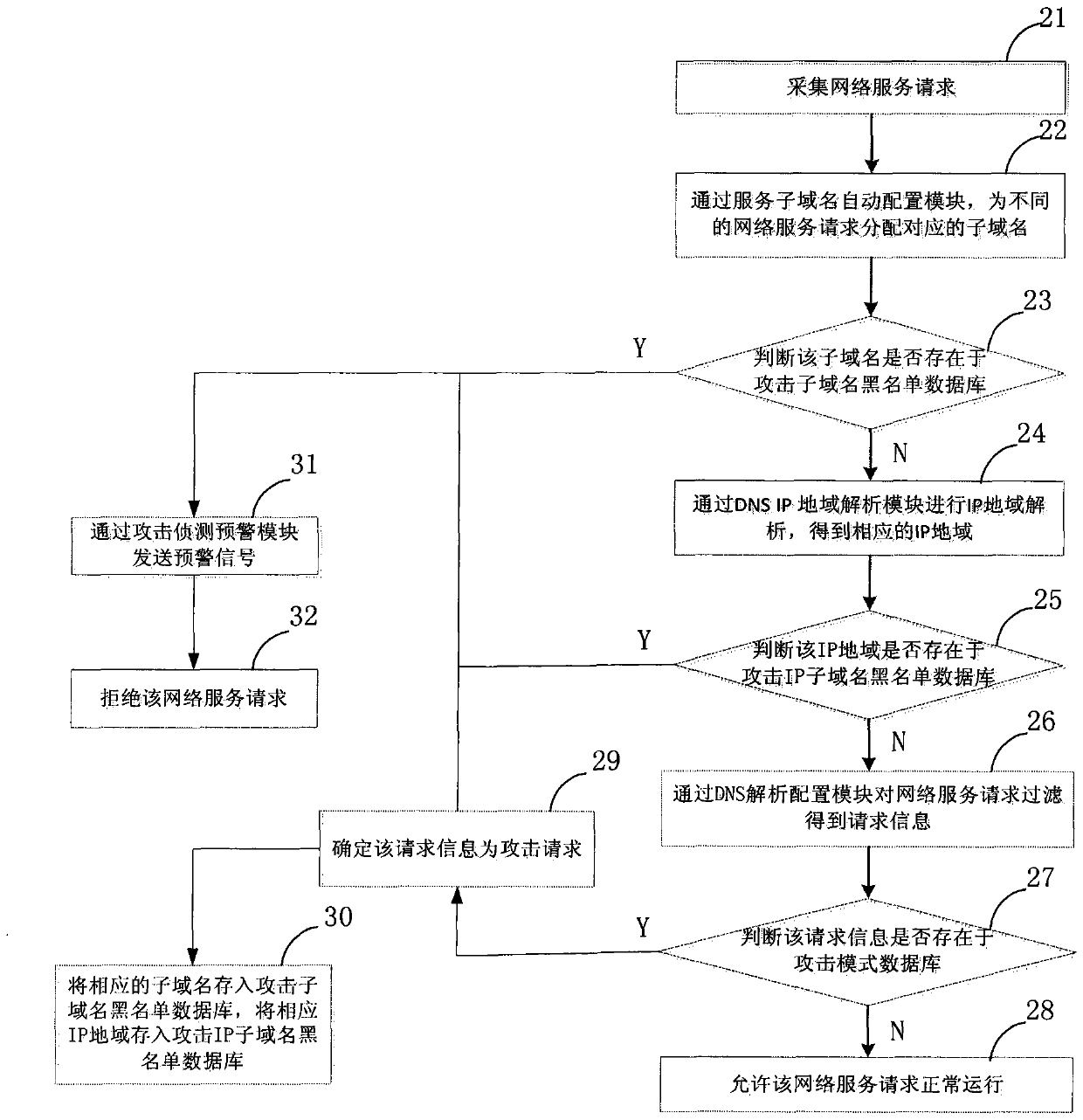
[0024] Attached below figure 1 And attached figure 2 The network attack defense method based on the DNS intelligent resolution system of the present invention is described in detail.
[0025] Such as figure 1 As shown, the network attack defense method based on the DNS intelligent resolution system includes the following steps:
[0026] Step 11: collecting network service requests;
[0027] Step 12: through the service sub-domain name automatic configuration module, assign corresponding sub-domain names to different network service requests;
[0028] Step 13: Determine whether the subdomain name exists in the attacking subdomain name blacklist database, and if so, perform step 20; otherwise, proceed to the next step;
[0029] Step 14: Perform IP region analysis on the network service request through the DNS IP region analysis module to obtain the corresponding IP region;
[0030] Step 15: Determine whether the IP region exists in the attacking IP subdomain name blacklist...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com