Repetitive log filtering method for terminal
A filtering method and log technology, applied in the field of network security, can solve the problems of wasting engineers, redundant data, and complicated log files, and achieve the effect of improving efficiency and reducing expenses
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Example Embodiment
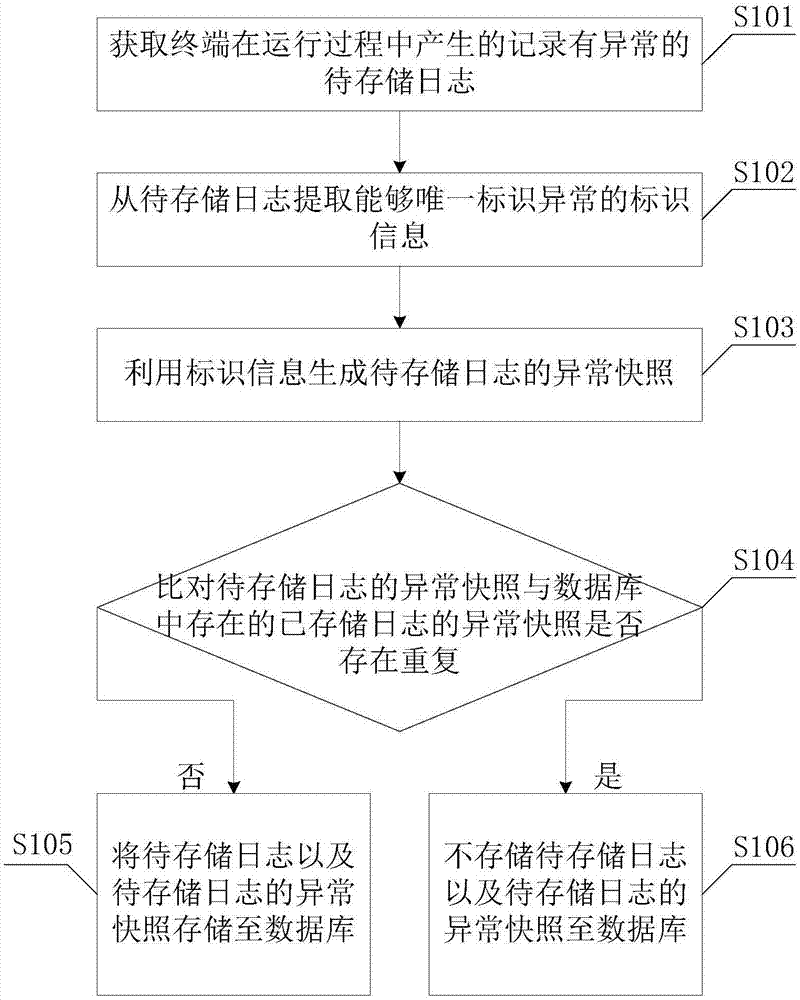
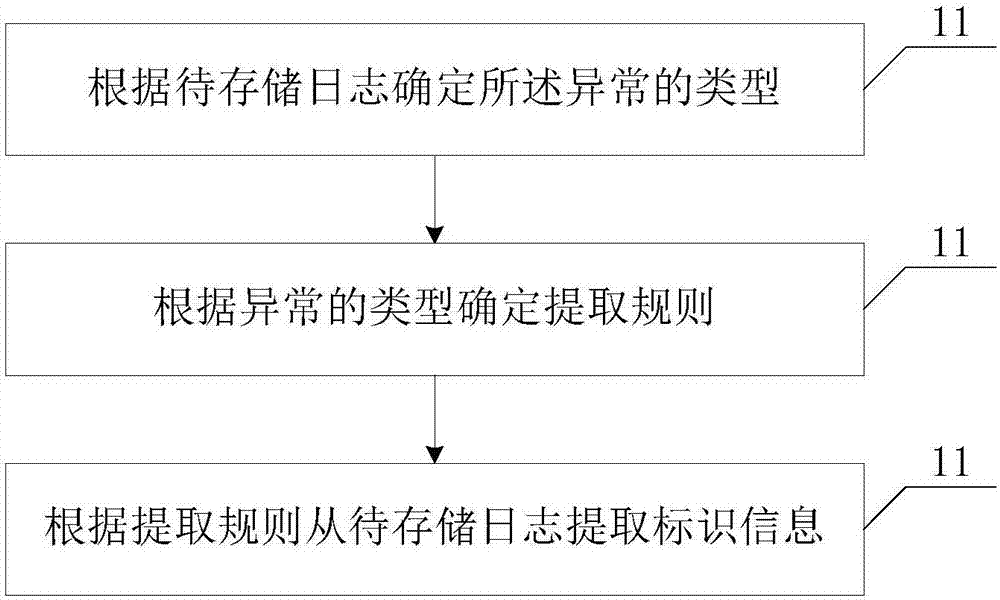
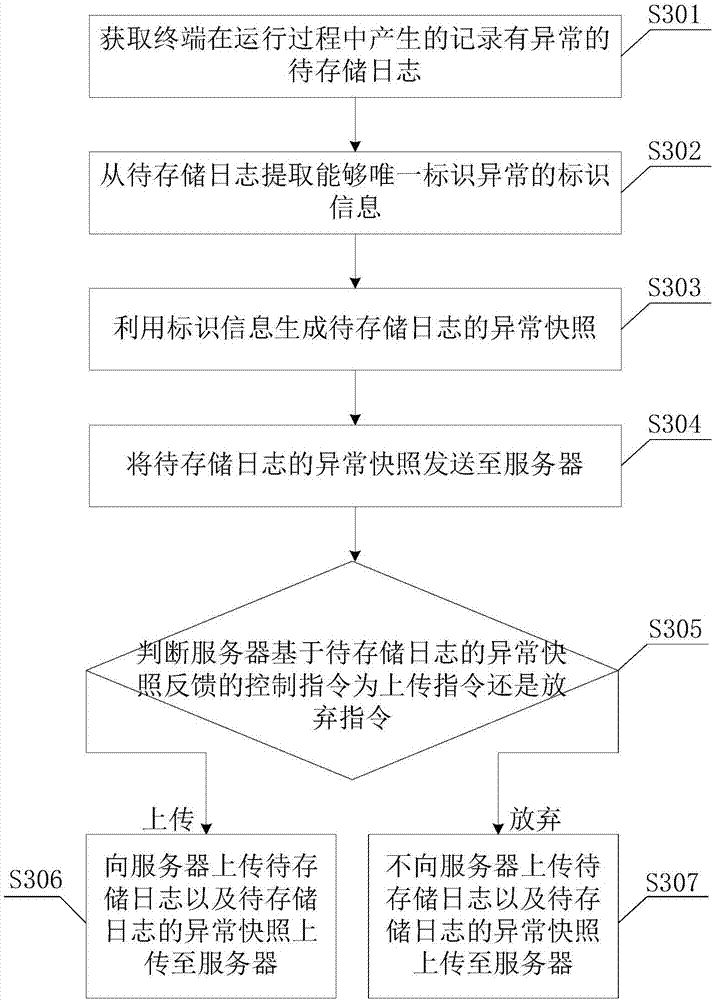
[0032] See figure 2 , figure 2 It is a schematic flowchart of the second embodiment of the repeated log filtering method of the terminal of the present invention. This embodiment is a specific embodiment in which the identification information that can uniquely identify the abnormality is extracted from the log to be stored, and the method includes the following steps:
[0033] S201: Determine the type of abnormality according to the log to be stored.
[0034] Specifically, the type of abnormality determined by the log to be stored can be specifically classified into application layer exception (JaveException), local layer exception (Native Exception), and application not responding exception (Application not Responsing).
[0035] S202: Determine the extraction rule according to the type of the abnormality.
[0036] Specifically, the exception extraction rule of the application layer is as follows: two judgments are made for each line of the exception information, firstly whether it...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap