A network video supervision method, device, equipment and readable storage medium
A network video and video technology, applied in the video field, can solve the problems of illegal, bad video, bad video source tracking, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
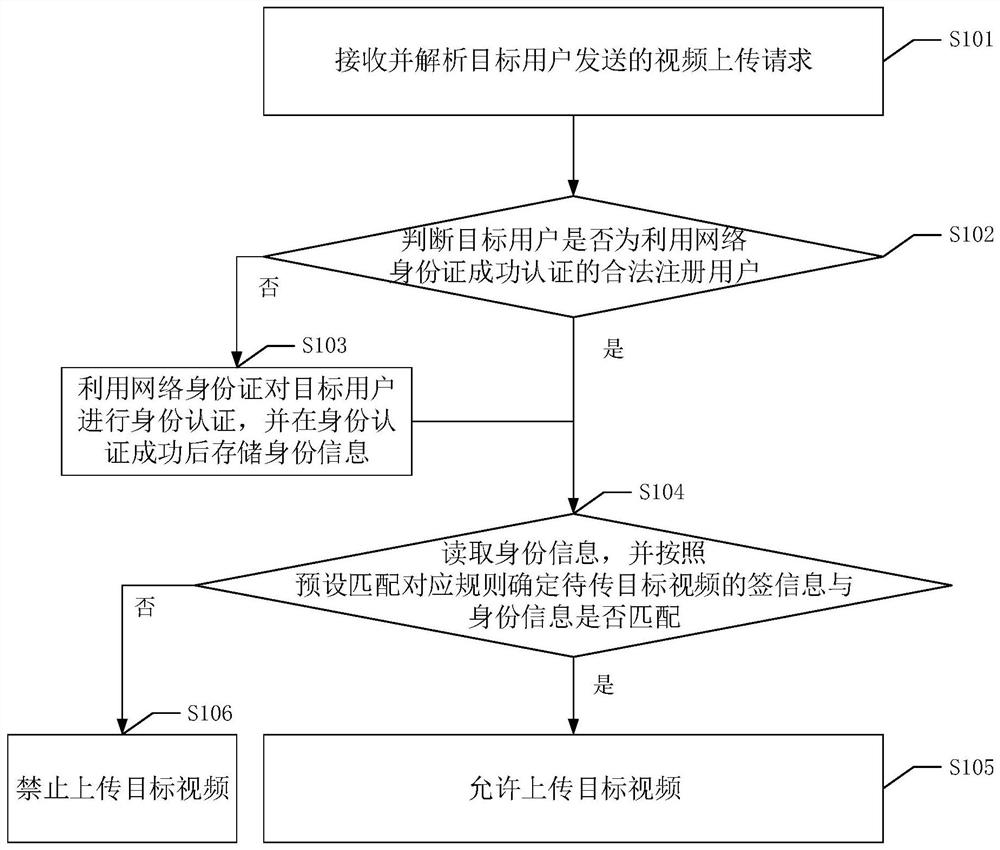
[0096] Please refer to figure 1 , figure 1 It is a flow chart of the first network video supervision method in the embodiment of the present application. This method can be applied to video network platforms. The method includes the following steps:
[0097] S101. Receive and analyze a video upload request sent by a target user.
[0098] Wherein, the target user may be any user in the video network platform. The target user can send a video upload request to the video network platform through a client of the target video network platform such as an APP, a web page, or a computer terminal, wherein the video upload request can specifically include the target video requested to be uploaded and the tag information corresponding to the target video. Among them, the label information can specifically be the category information to which the target video belongs, such as information such as entertainment, funny, surprise, horror, etc.; of course, the label information can also spec...
Embodiment 2
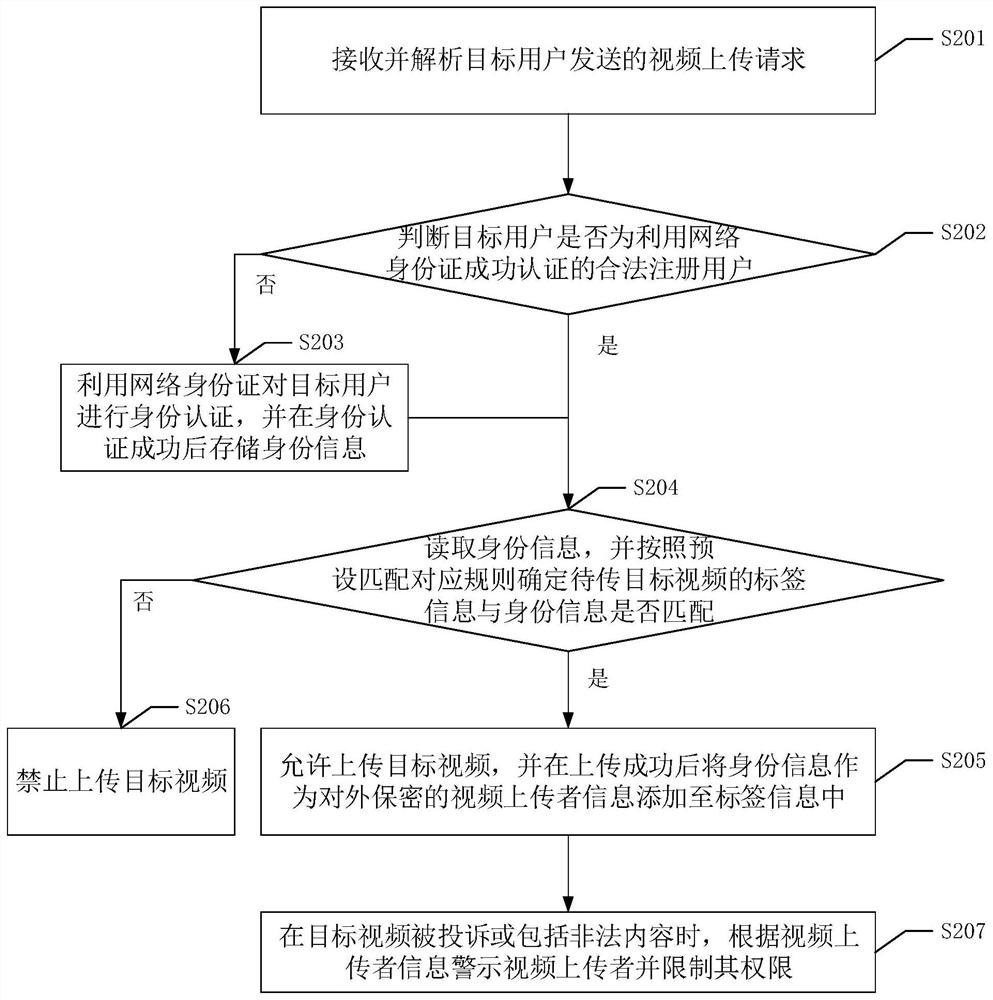
[0116] Please refer to figure 2 , figure 2 It is a flow chart of the second network video monitoring method in the embodiment of the present application. This method can be applied to video network platforms. The method includes the following steps:
[0117] S201. Receive and analyze a video upload request sent by a target user.
[0118] S202. Determine whether the target user is a legally registered user successfully authenticated by using the network ID card.
[0119] After determining whether the target user is a legitimate registered user, different operations can be performed according to different judgment results. Specifically, when the judgment result is no, the operation of step S203 is performed, and when the judgment result is yes, the operation of step S204 is performed.
[0120] S203. Use the network ID card to authenticate the target user, and store the identity information after the identity authentication is successful.
[0121] S204. Read the identity in...
Embodiment 3
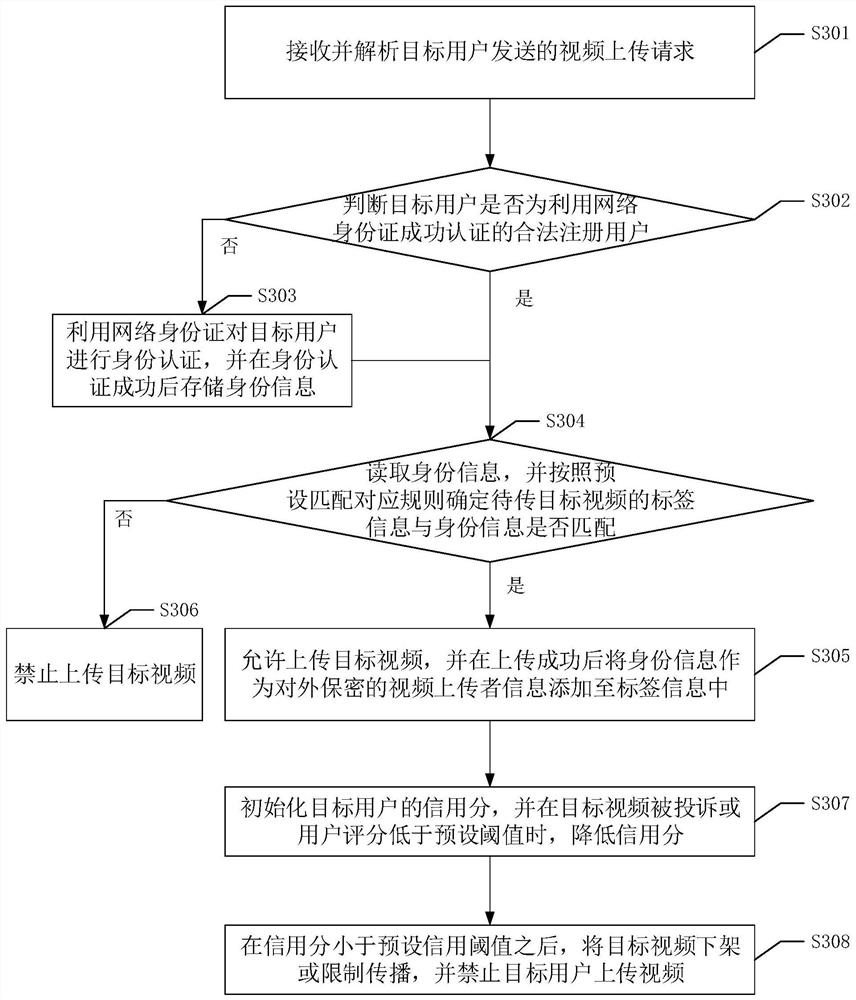
[0128] Please refer to image 3 , image 3 It is a flow chart of the third network video supervision method in the embodiment of the present application. This method can be applied to video network platforms. The method includes the following steps:
[0129] S301. Receive and analyze a video upload request sent by a target user.
[0130] S302. Determine whether the target user is a legally registered user successfully authenticated by using the network ID card.
[0131] After determining whether the target user is a legitimate registered user, different operations can be performed according to different judgment results. Specifically, when the judgment result is no, the operation of step S303 is performed, and when the judgment result is yes, the operation of step S304 is performed.
[0132] S303. Use the network ID card to authenticate the target user, and store the identity information after the identity authentication is successful.
[0133] S304. Read the identity info...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com