A blockchain-based data encryption protection method and system
A data encryption and block chain technology, applied in the field of data processing, can solve the problems of reducing authentication security, easy to be illegally stolen, data abnormality, etc., and achieve the effect of ensuring safety and reliability and improving safety and reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
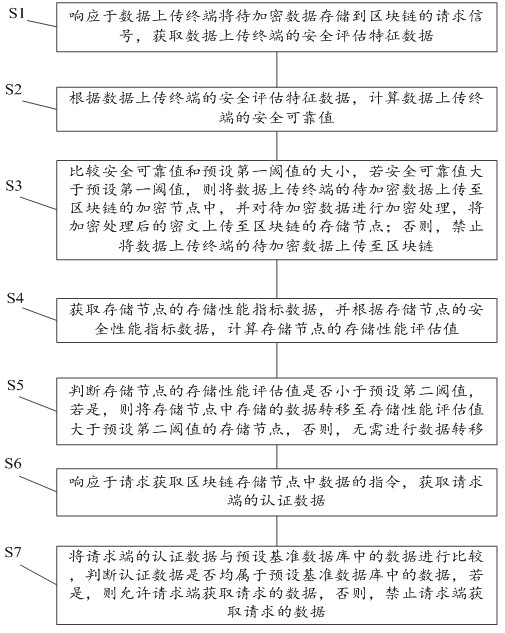
[0045] like figure 1 As shown, the present application provides a blockchain-based data encryption and protection method, which includes the following steps:
[0046] Step S1, in response to a request signal from the data uploading terminal to store the data to be encrypted in the blockchain, obtain the security assessment feature data of the data uploading terminal.
[0047] Specifically, the data upload terminal generates the data to be encrypted, packages the to-be-encrypted data to generate a data abstract or file name, and requests the encryption node on the blockchain to upload the data and stores it. After the encryption node of the blockchain receives the request signal to obtain the security assessment feature data of the data upload terminal.
[0048] As a specific embodiment of the present invention, the security assessment feature data of the data upload terminal includes: attribute feature data of the data upload terminal: IP address, MAC address, user name, reques...
Embodiment 2
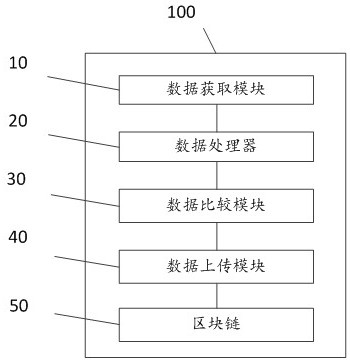
[0079] like image 3 As shown, the present application also provides a blockchain-based data encryption protection system 100, which includes:
[0080] The data acquisition module 10 is configured to store the data to be encrypted in the storage node of the blockchain in response to the request of the data uploading terminal, and obtain the security assessment feature data of the data uploading terminal;
[0081] The data processor 20 is configured to calculate the safety and reliability value of the data uploading terminal according to the safety evaluation characteristic data of the data uploading terminal;
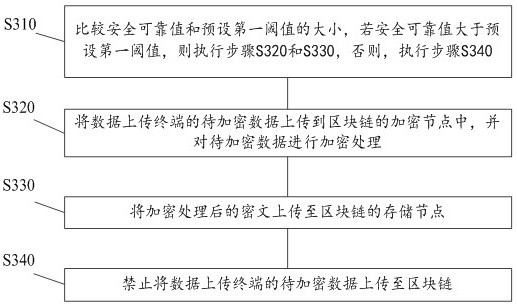
[0082] The data comparison module 30 is used to compare the safety and reliability value with the preset first threshold value. If the safety and reliability value is greater than the preset first threshold value, upload the to-be-encrypted data of the data uploading terminal to the encryption node of the blockchain 50 , and encrypt the data to be encrypted; otherwise, i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com