Framework for coordination between endpoint security and network security services
A security service and security technology, applied in computer security devices, instruments, computing, etc., can solve problems such as application program and operating system program or code attack, consumption of computer resources, computer operation deterioration or interruption, etc., to prevent proliferation or impact. , Prevent the leakage of sensitive information, and minimize the effect of time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
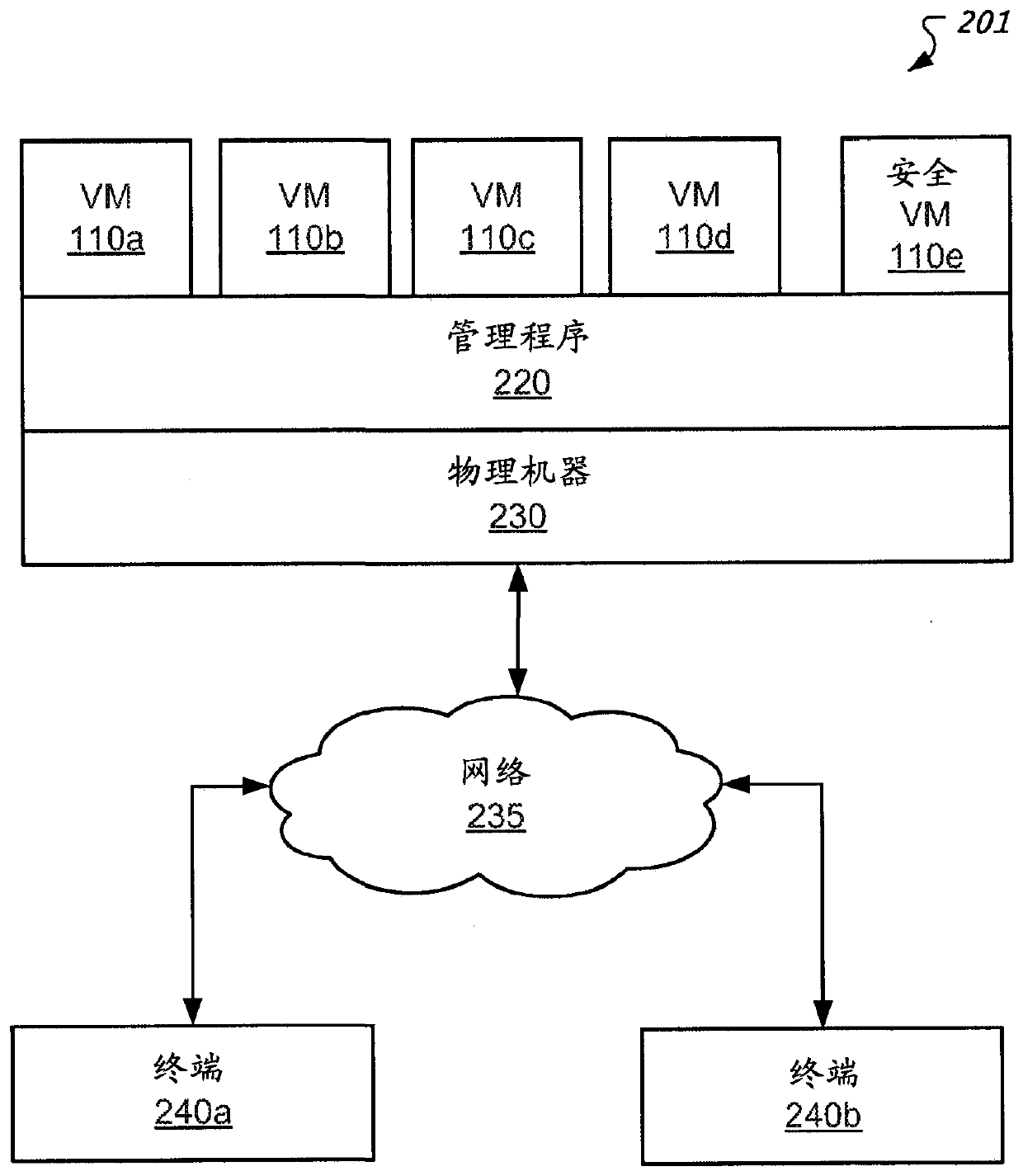
[0018] This document describes a framework for enabling synergistic orchestration between different endpoint security services (eg, antivirus software) and network security services (eg, network firewalls). Such a framework may enable rapid and automated responses to security policy violations within a virtual machine environment, while enabling customers to select the best of breed endpoint and network security services, including those offered by different vendors.
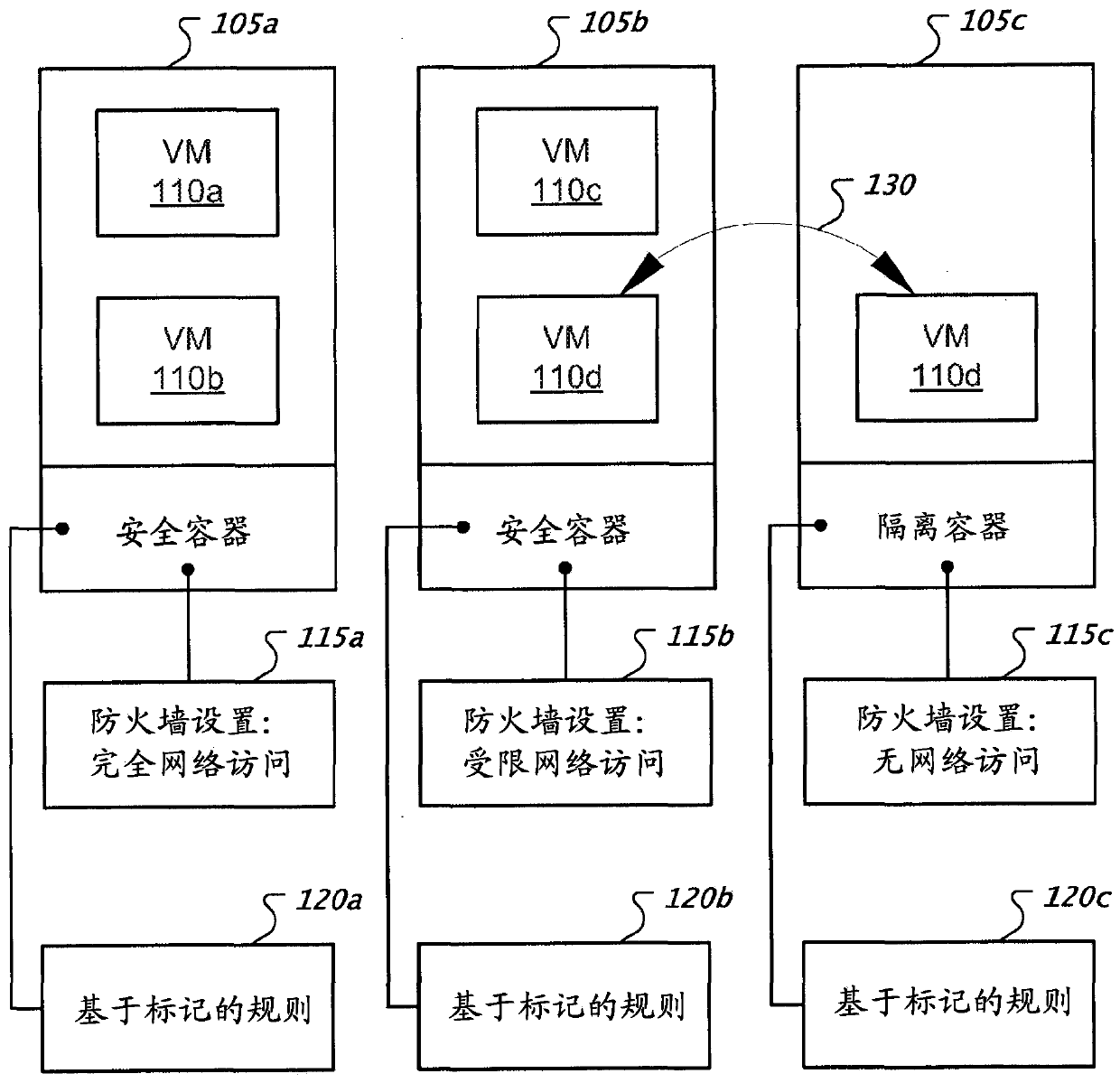
[0019] figure 1 An example of virtual machines being assigned to secure containers and being transferred between secure containers is shown. A physical machine, such as a data processing apparatus, may execute virtual machines 110a-d according to respectively assigned secure containers 105a-c. Security containers 105a-c are virtual machine operating environments that may specify policies such as firewall settings 115a-c, operational settings for one or more security services, and tag-based rules 120a-c. In som...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com