System and method for secure access to network devices based on one-time access credentials
A network device, a one-time technology, applied in transmission systems, digital transmission systems, secure communication devices, etc., can solve problems such as high risk, difficulty in locating the actual user and responsible person of the account, and inability to fully grasp the management and control rights of each network device , to achieve the effect of ensuring safety, safety and reliability for one-time use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail below in conjunction with the accompanying drawings.
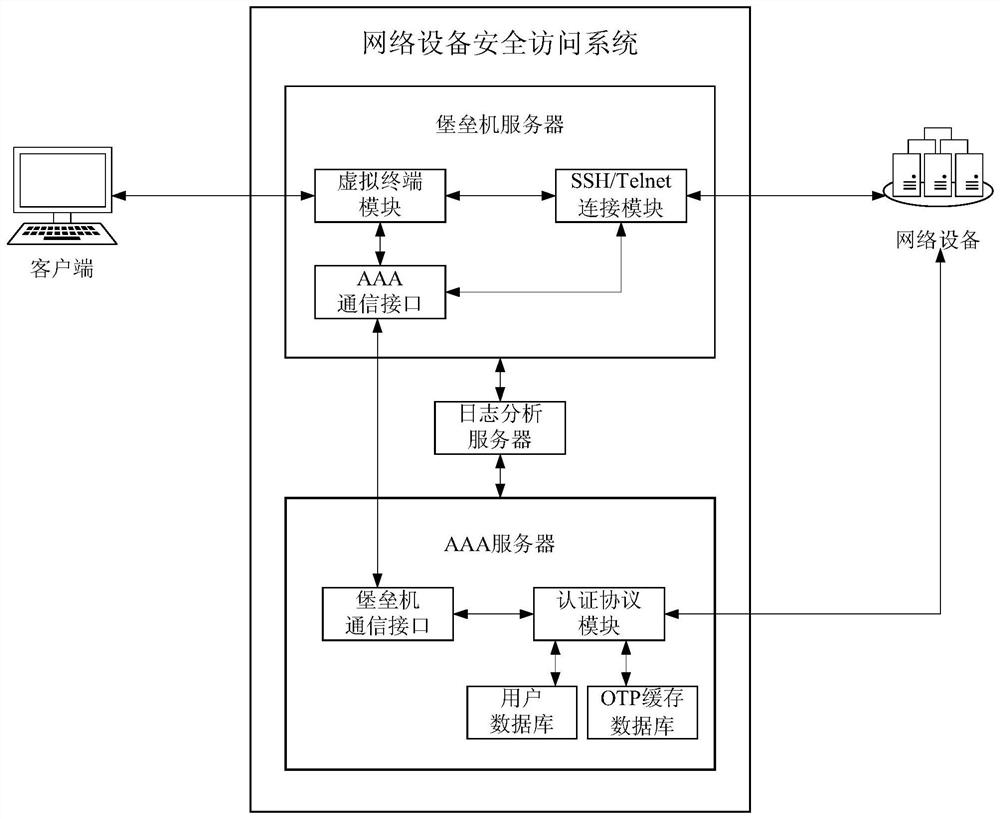
[0049] An important technical innovation feature of the system of the present invention is to use the one-time access certificate OTP, that is, the dynamic password to replace the original account password of the traditional client user when connecting to the managed network device. The dynamic password OTP is automatically generated by the AAA server according to the set algorithm for each user's operation connection request for each management network device, an unpredictable real-time random combination of characters and / or numbers, and the use of each dynamic password It has only one lifespan, and it will fail after use.
[0050] see image 3 , introducing the structure of the system of secure access to network equipment based on one-time access credentials i...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap