Method and system for remotely authorizing and maintaining cipher machine online
A cipher machine and authorization code technology, applied in the field of cipher machine maintenance, can solve problems such as manual maintenance, and achieve the effect of simplifying the process and controllable maintenance work.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
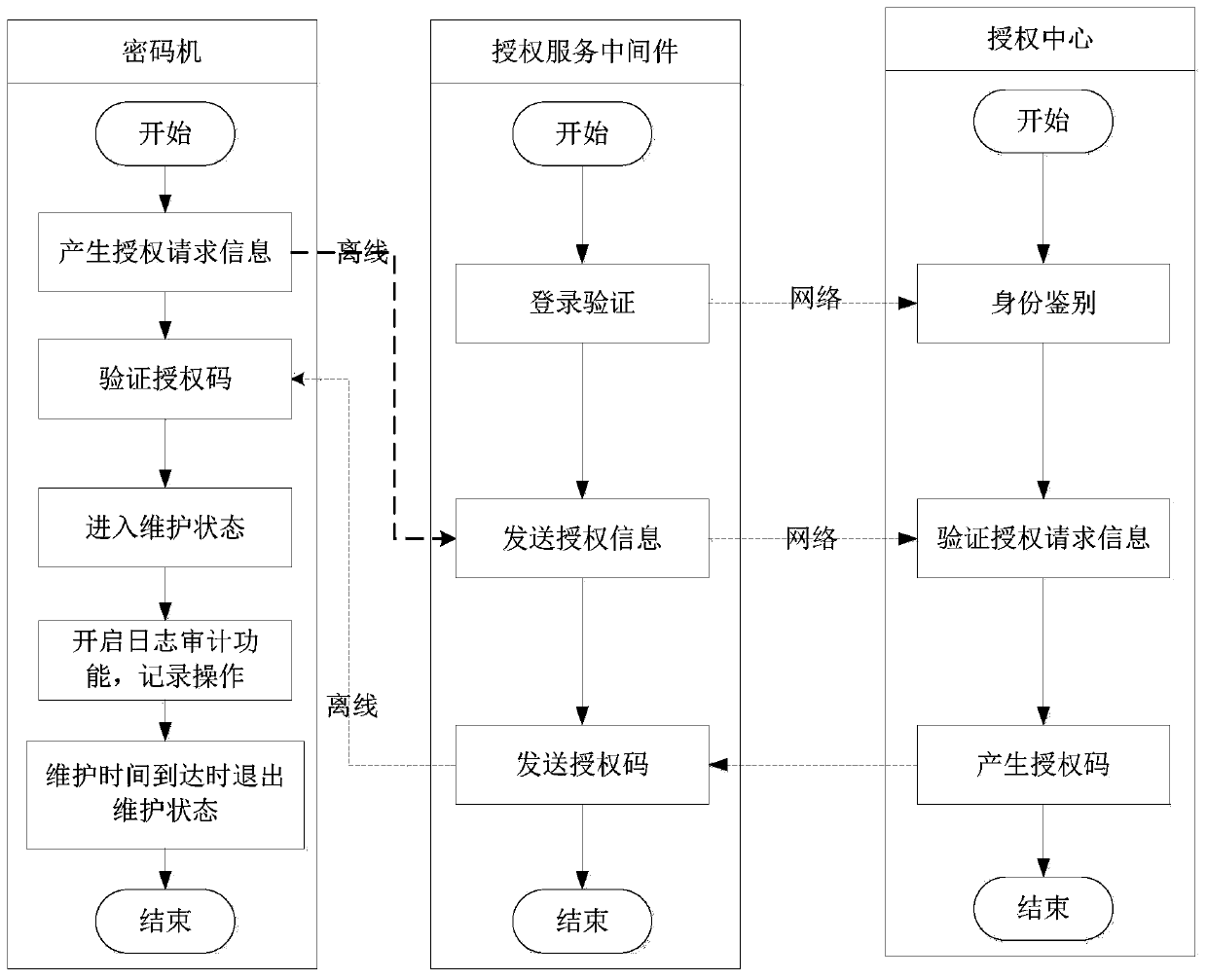
[0036] refer to figure 1 , this embodiment discloses a method for remote online authorization and maintenance of a cipher machine, which is implemented by the cooperation of the cipher machine, the authorization service middleware, and the authorization center. Specifically, the method includes:
[0037] S101: The cipher machine to be maintained generates authorization request information according to its own inherent information.
[0038] Specifically, the cipher machine to be maintained generates authorization request information according to its own inherent information, including: generating an HMAC verification value according to the MAC address, serial number and the HMAC key preset at the factory; The authorization request information is obtained by combining the request time and the generated HMAC verification value.
[0039] Both MAC address and serial number can uniquely represent a cryptographic machine. Theoretically, only one of them needs to be selected, but be...
Embodiment 2
[0050] refer to figure 2 , based on the same inventive concept, this embodiment discloses a system for remote online authorization and maintenance of a cipher machine. The system includes: a cipher machine, an authorization service middleware, and an authorization center. For interaction, the cipher machine and the authorization service middleware interact through offline input. Specifically, the authorization service middleware may be an application program installed on a smart phone terminal or other similar terminals. The terminal can exchange data with the authorization center through the online network.
[0051] The encryption machine is configured to: generate authorization request information according to its own inherent information;
[0052] The authorization service middleware is configured to: obtain the authorization request information input offline, and transfer the authorization request information to an authorization center;
[0053] The authorization cente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com