Communication method, device, storage medium and processor
A communication method and processor technology, applied in transmission systems, electrical components, etc., can solve the problems of inability to configure management addresses, separate management addresses, and complicated configuration of management addresses, and improve the convenience of deployment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
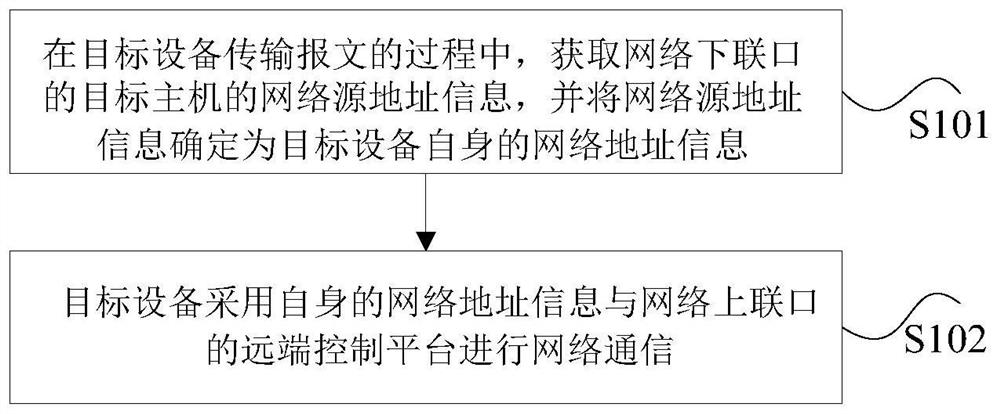
[0035] figure 1 It is a flowchart of a communication method according to an embodiment of the present application. like figure 1 As shown, the method includes the following steps:
[0036] Step S101 , in the process of transmitting the message by the target device, obtain the network source address information of the target host of the downlink port, and determine the network source address information as the network address information of the target device itself.
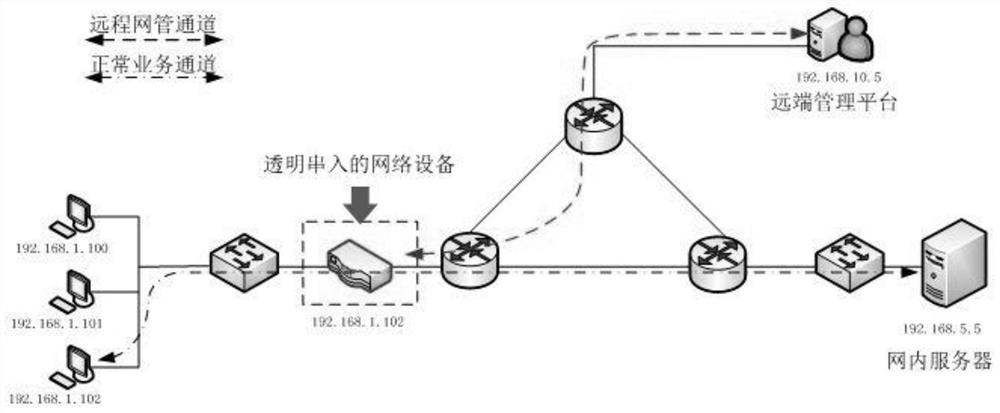
[0037] Specifically, as figure 2 As shown, it is a schematic diagram of the deployment of the target device. The target device is a network device, such as a network bridge device, network monitoring device, network security device, and general equipment such as switches and routers. The downlink port (LAN) of the device is connected to the terminal device or the uplink port of the access switch connected to the terminal device. The uplink port (WAN) of the target device is connected to the downlink port of t...
Embodiment 2
[0066] Figure 4 It is a schematic diagram of another communication method according to an embodiment of the present application. The method is a method for accessing a network of a network device with a dedicated chip architecture, such as Figure 4 As shown, the method includes:
[0067] First, the network processing chip extracts the header information of the packets received by the downlink port, and sends the extracted information to the embedded CPU of the target device.
[0068]Next, the network processing chip performs matching filtering on the source IP, destination IP, destination MAC, and protocol number of the packets received by the uplink port. Decrypt the content of the UDP packet in the filtered packets, filter the identification keywords in the decrypted content, and check the protocol format. The packets that pass the filtering and inspection are management packets sent by the management platform, and the chip forwards the management packets. The text is s...
Embodiment 3
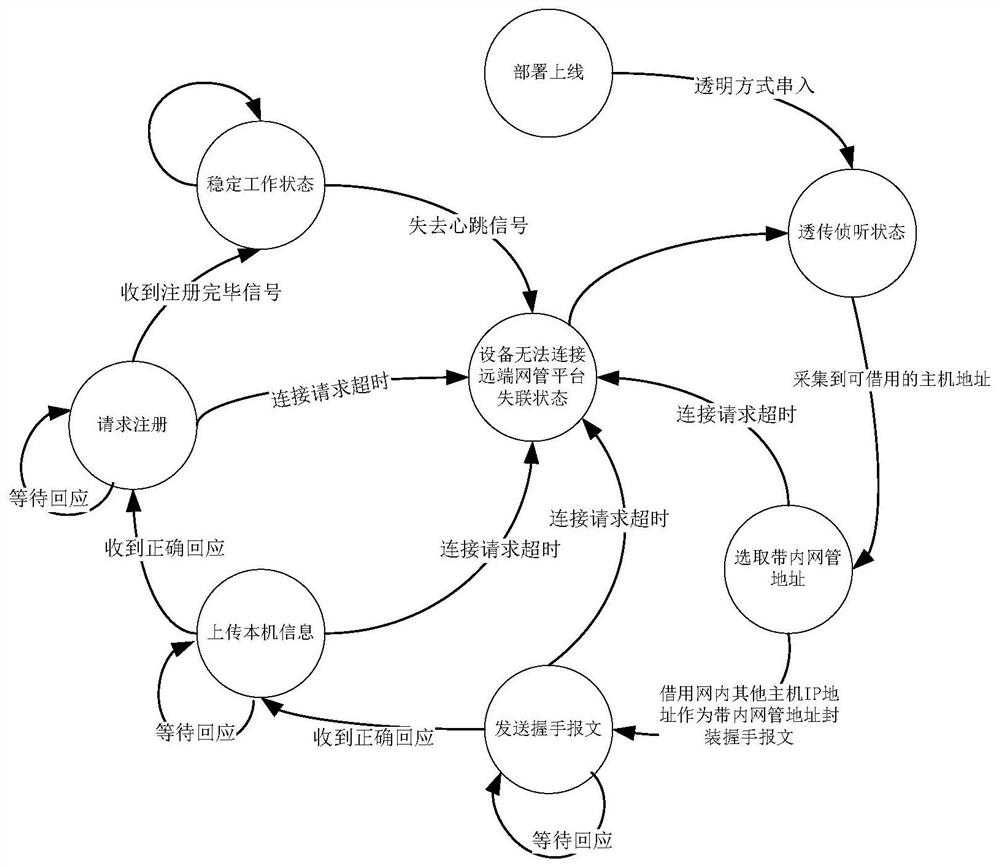
[0073] Figure 5 It is a flowchart of another communication method according to an embodiment of the present application. The target device deployed into the network in this method is a network device with a dedicated chip architecture. like Figure 5 As shown, the method includes:
[0074] Configure the destination address of the remote network management on the target device.
[0075] When the target device is just connected to the network, the default initial working state is transparent transmission and listening. The local device is deployed transparently online by being serially connected to the network, and collects the host address information encapsulated in the packets from the downlink port. Specifically, for The packet header information is extracted, and the extracted content is source MAC, source IP address, destination MAC, destination IP address and protocol type, and the extracted information is sent to the embedded CPU.
[0076] Determine whether the host...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com