Privacy protection workflow publishing method for maintaining availability of critical path
A critical path and privacy protection technology, applied in digital data protection, instruments, computing, etc., can solve problems such as difficulty in ensuring the leakage probability of the critical path in the release graph, failure to take into account path hiding, and critical path leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
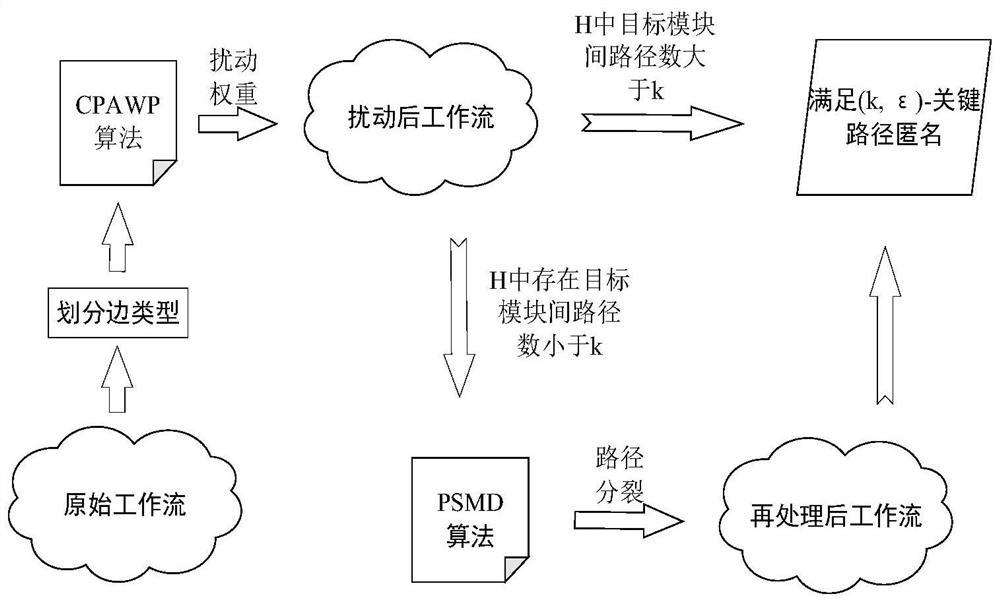
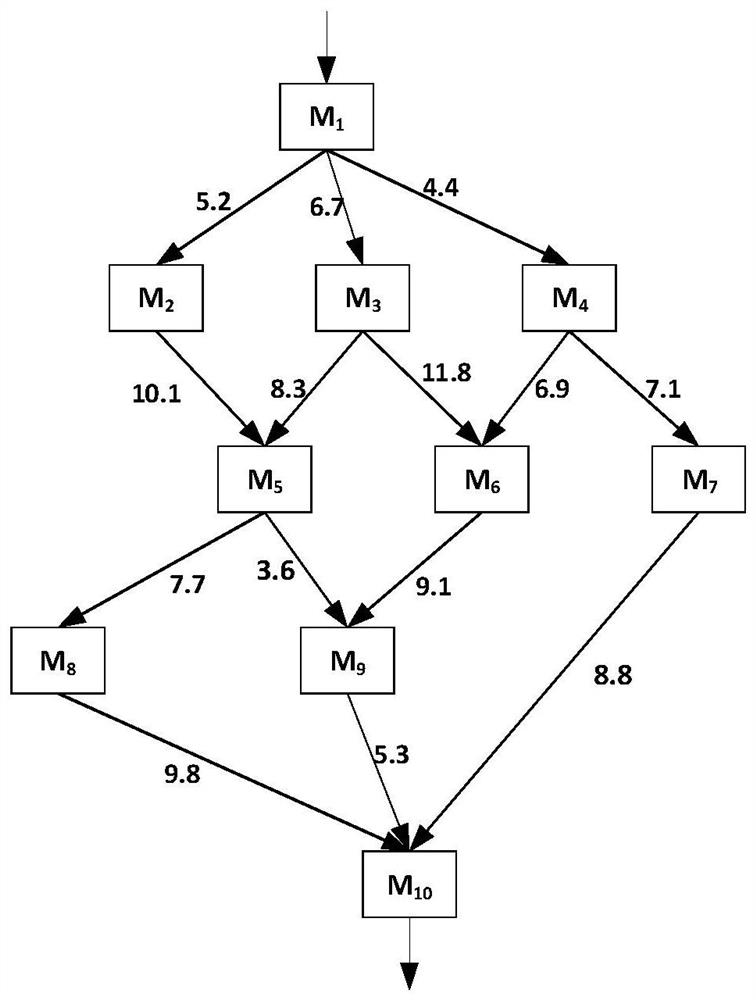
[0049] Embodiment 1: see figure 1 , a privacy-preserving lineage workflow sharing release method, comprising the following steps:
[0050] Step (1) Given the original workflow WF, the target module pair set H is divided into three categories based on the degree of participation of directed edges in the critical path, zero-visit edges (NVE), full-visit edges (AVE) and partial access edge (PVE);
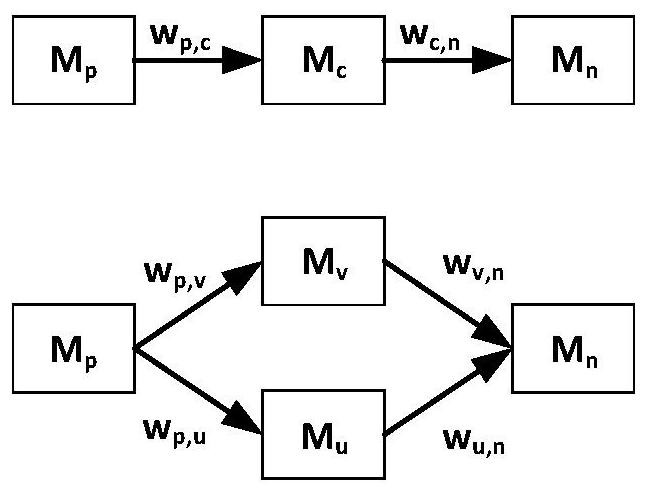
[0051] Step (2) Anonymize the critical paths between the target module pairs, and perturb the edge weights on the Top-k paths, so that the path weights satisfy the ε-error equivalence after perturbation; if there are less than k paths between the module pairs, If the ε-error equivalence between Top-k paths cannot be realized, continue to step (3);
[0052] Step (3) When there are less than k paths between target modules in H, only after step (2) is executed, the workflow does not satisfy the (k, ε)-critical path anonymity, and the path splitting method is used to find that the targe...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com