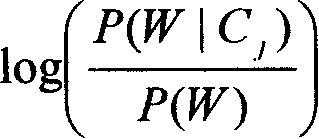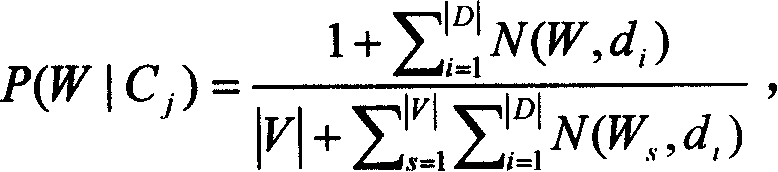Invasion detection (protection) product and firewall product protocol identifying technology
A technology for protocol identification and intrusion detection, applied in the field of protocol identification
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
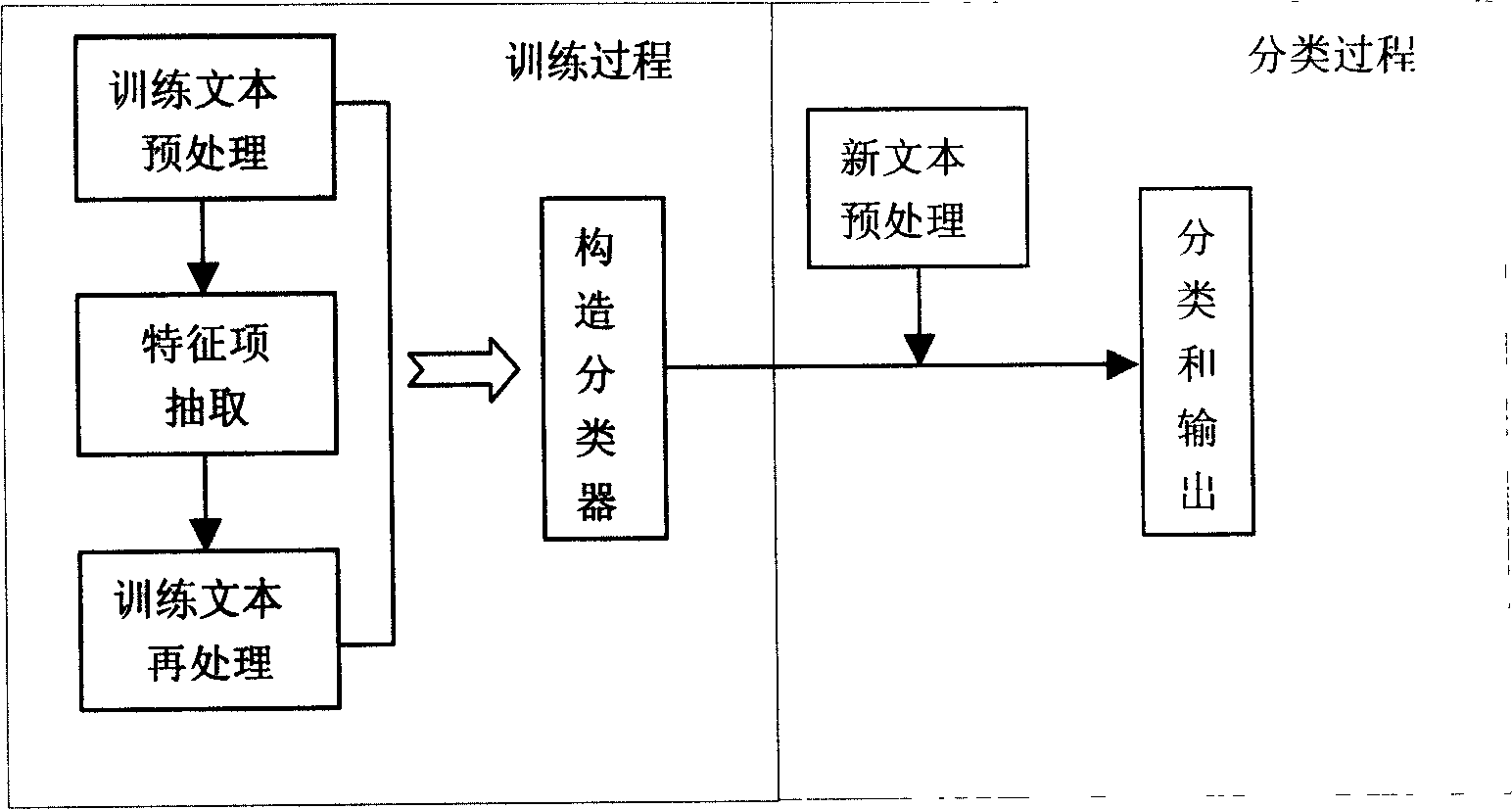
[0007] combine figure 1 , the present invention relates to a protocol identification technology in an intrusion detection (protection) product and a firewall product, wherein the protocol identification technology includes a training process method and a classification process method, and the training process method includes training text preprocessing, Feature item extraction, training text reprocessing and subsequent steps of constructing a classifier are connected. The classification process method includes the steps of new text preprocessing, classification and output. More specifically, the present invention refers to a technical method of analyzing and capturing data packets in the network, performing various statistical operations and pattern matching to find the protocol it belongs to, and then handing it over to a protocol analysis engine for further analysis. Generally speaking, in establishing the protocol recognition technology for network communication, we must fi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com