Firewall device
A firewall and virtual firewall technology, applied in the direction of network connection, etc., can solve the problems of loss of security policies, inability to filter and forward, and inability to publish security policies, and achieve the effect of increasing the number of users and suppressing the retrieval processing time.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1-1
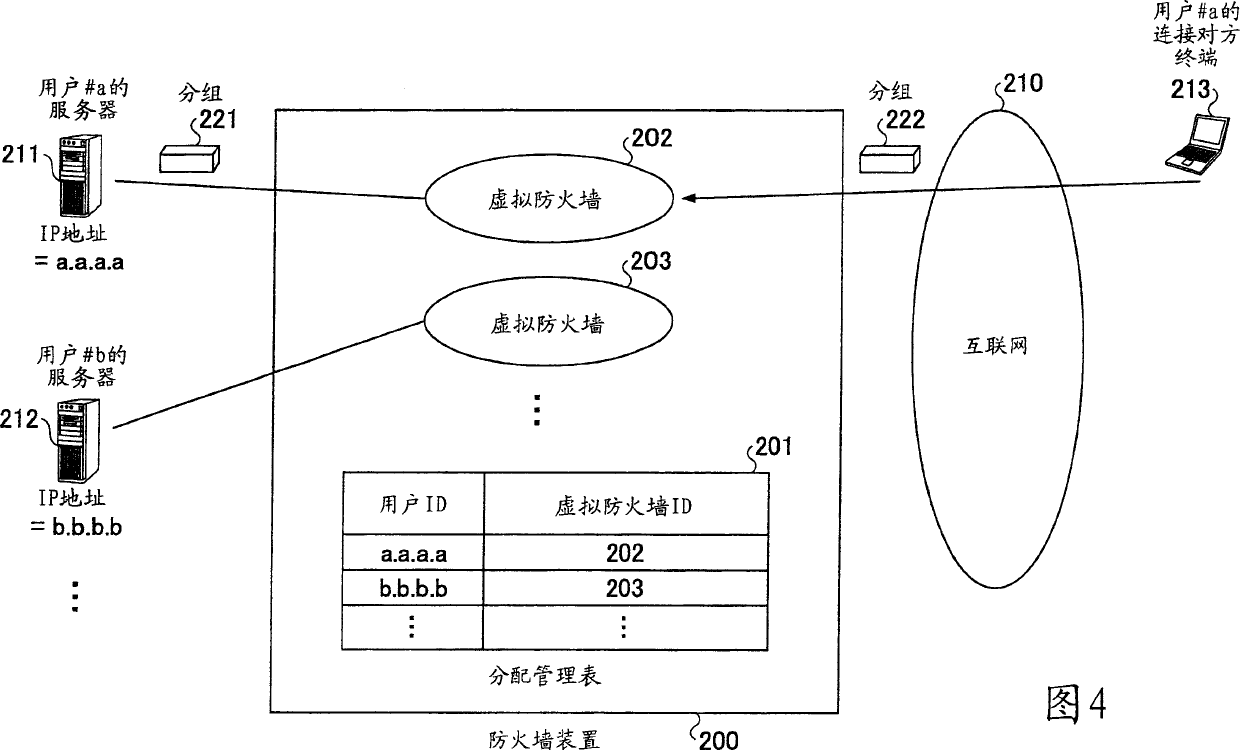
[0112] First, Embodiment 1-1 of the present invention will be described using FIG. 8 and FIG. 9 . In this example, it is assumed that the connection method between the user and the network is PPP, and the authentication communication is RADIUS.
[0113] The firewall device 100 has a virtual firewall for each user. For example, in the firewall device 100 there are: a virtual firewall 102 that protects the terminal 111 of user #a using the security policy of user #a; a virtual firewall 103 that protects the terminal 112 of user #b using the security policy of user #b.
[0114] In addition, user names and virtual firewall IDs that can be set in advance are registered in the allocation management table 101 . That is, in the allocation management table 101, the correspondence relationship between the user name #a and the virtual firewall ID 102, and the user name #b and the virtual firewall ID 103 is registered. However, since the user IP address serving as the user ID of each us...
Embodiment 1-2
[0122] Embodiment 1-2 of the present invention will be described using FIG. 10 . This example shows the following situation: In Embodiment 1-1, due to reasons such as errors in the username or password sent from user #a, the combination of the username and password sent through the notification 141 of the username and password is the same as the login in The combination of the username and password in the RADIUS server 130 is inconsistent.
[0123] In addition, since the process of issuing the user name and password notification 141 from the LCP 139 is the same as that of the embodiment 1-1, description thereof will be omitted.
[0124] For the reason described above, when the authentication error notification 642 is issued from the RADIUS server 130, the firewall device 100 transmits the authentication error notification 643 to the user terminal 111, and ends the PPP establishment process. At this time, the firewall device 100 does not perform any processing on the allocatio...
Embodiment 1-3
[0126] A third embodiment of the present invention will be described using FIG. 8 , FIG. 11 and FIG. 12 . This example shows a method in which, in Embodiment 1-1, the terminal 114 of the user #c who has not logged in to the firewall service connects to the Internet 110, and then performs IP communication with the terminal 113 of the connection partner. In addition, the user #c who has not logged in the firewall service has not registered the user name and virtual firewall in the allocation management table 101-3, but can enjoy the communication service of the Internet 110 through the terminal 114, and log the user name and password in the RADIUS server 130 .
[0127] In FIG. 12 , operations up to notification 142 of the user IP address are the same as those in Embodiment 1-1, and description thereof will be omitted.
[0128] When the user IP address notification 142 is received, the firewall device 100 holds the user IP address [c.c.c.c] of the user terminal described in the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com